Renamed wp-config.php => Sensitive Data Exposure
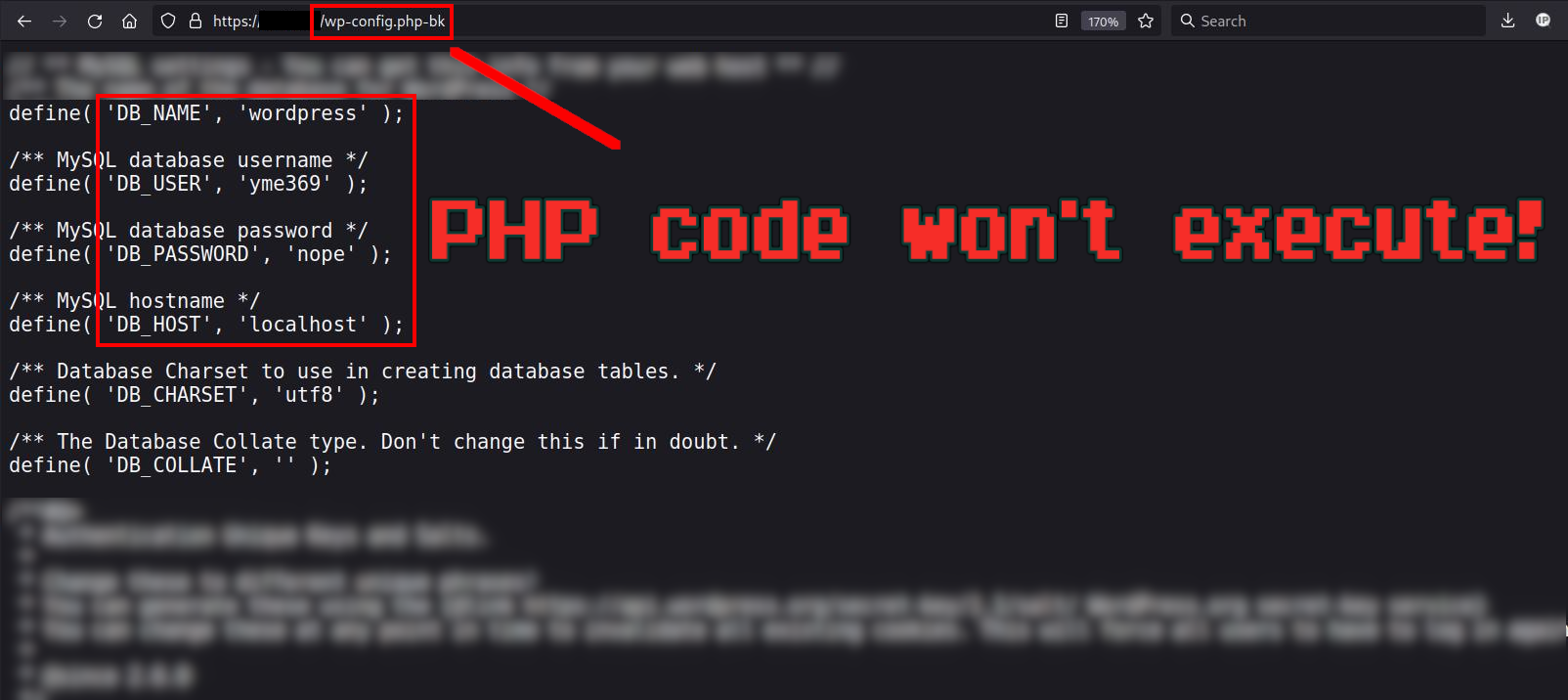
Attackers continue to find easy victims by crawling websites using enumeration techniques and looking for configuration files that have had their file extension modified.