Renamed wp-config.php => Sensitive Data Exposure
Outline
Renaming Website Configuration Files⌗
While troubleshooting a problem, it may be necessary for a website owner or support provider to temporarily rename an existing wp-config.php file so that they can test the website with a separate wp-config.php file. For example, after a setting change or database login change.
Unforunately poor training and information has led to the people renaming the wp-config.php file by appending text to the end of it so that it becomes something like wp-config.php.bak.
Why Is This Bad?⌗
By default, a PHP file needs to have the file extension set to .php in order for the PHP code to be properly executed. While it’s possible to force the HTTP server to load PHP code in different file extensions other than .php - it’s pretty uncommon.
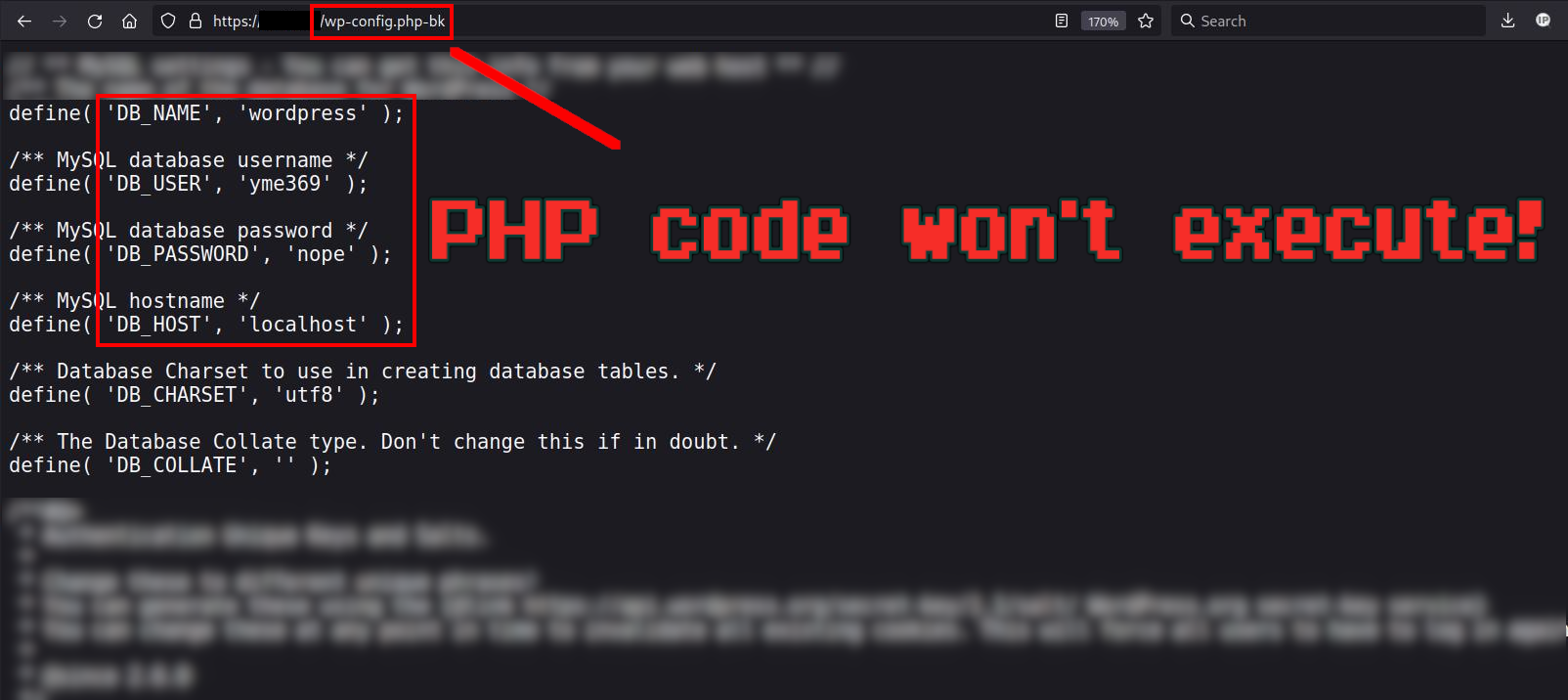
The problem with appending text to an existing file extension like wp-config.php is that it will prevent the PHP interpreter from reading and executing the PHP code. A common way this is done is by renaming wp-config.php to wp-config.php-bak, which prevents the PHP code from being executed.
This means that instead of the PHP code running and displaying a web page - it will instead just simply dump the code from the renamed PHP file.
For an attacker this allows them to view your MySQL database login information simply by sending a GET request to the renamed configuration file (e.g wp-config.php).
Since the attacker doesn’t know for certain how you renamed the configuration file - they will enumerate the most common renaming variations in the hopes that one of them is successful in dumping the PHP source code instead of it executing.
Prevention & Mitigation⌗
-
Training and Awareness
The easiest way to prevent this is to not change the PHP file extension on any PHP configuration file, so if you need to rename such a file then try prepending text to the filename instead of appending text at the end.
This is important for both website owners and also web hosting or support providers as they often commit this mistake during routine troublehsootings.
-
Web Application Firewall (WAF) like mod_security or a network IDS/IPS like Suricata
A WAF or IDS/IPS will allow you to simply drop requests sent to
wp-config.phpas there’s really no reason why someone would send a direct request to that file. Depending on the choice of WAF or IDS/IPS - you may need to create your own rule to block this malicious activity.
Most Requested wp-config.php Filenames⌗
This crawling technique is popular with AnonymousFox and the most commonly requested filename variations are listed below:
/wp-config.bak
/wp-config.good
/wp-config.php_
/wp-config.php~
/wp-config.php.0
/wp-config.php.1
/wp-config.php_1
/wp-config.php.2
/wp-config.php.3
/wp-config.php.4
/wp-config.php.5
/wp-config.php.6
/wp-config.php.7
/wp-config.php.8
/wp-config.php.9
/wp-config.php.a
/wp-config.php.b
/wp-config.php.backup
/wp-config.php-bak
/wp-config.php.bak
/wp-config.php_bak
/wp-config.php.bak1
/wp-config.php.bk
/wp-config.php.cust
/wp-config.php.disabled
/wp-config.php.new
/wp-config.php_new
/wp-config.php.old
/wp-config.php_Old
/wp-config.php.orig
/wp-config.php_orig
/wp-config.php-original
/wp-config.php.original
/wp-config.php_original
/wp-config.phporiginal
/wp-config.php.save
/wp-config.php.swn
/wp-config.php.swo
/wp-config.php.swp