PaaS à la carte: Phishing Kit Caught In Development
Outline
An unsuspecting .tar.gz on a compromised website turned out to contain a directory of various malware, scam, and phishing content.
Background⌗
A further examination of the phishing content revealed some interesting correspondence between the PaaS (phishing-as-a-service) customer and the phishing kit creator.
Apparently the buyer had ordered a phishing kit to be created that would be used to target icscards.nl, but it sounds like the buyer wasn’t happy with the initial version and left a message for the phishing kit creator in a TXT file:
Buyer Is Not Satisfied 😐⌗
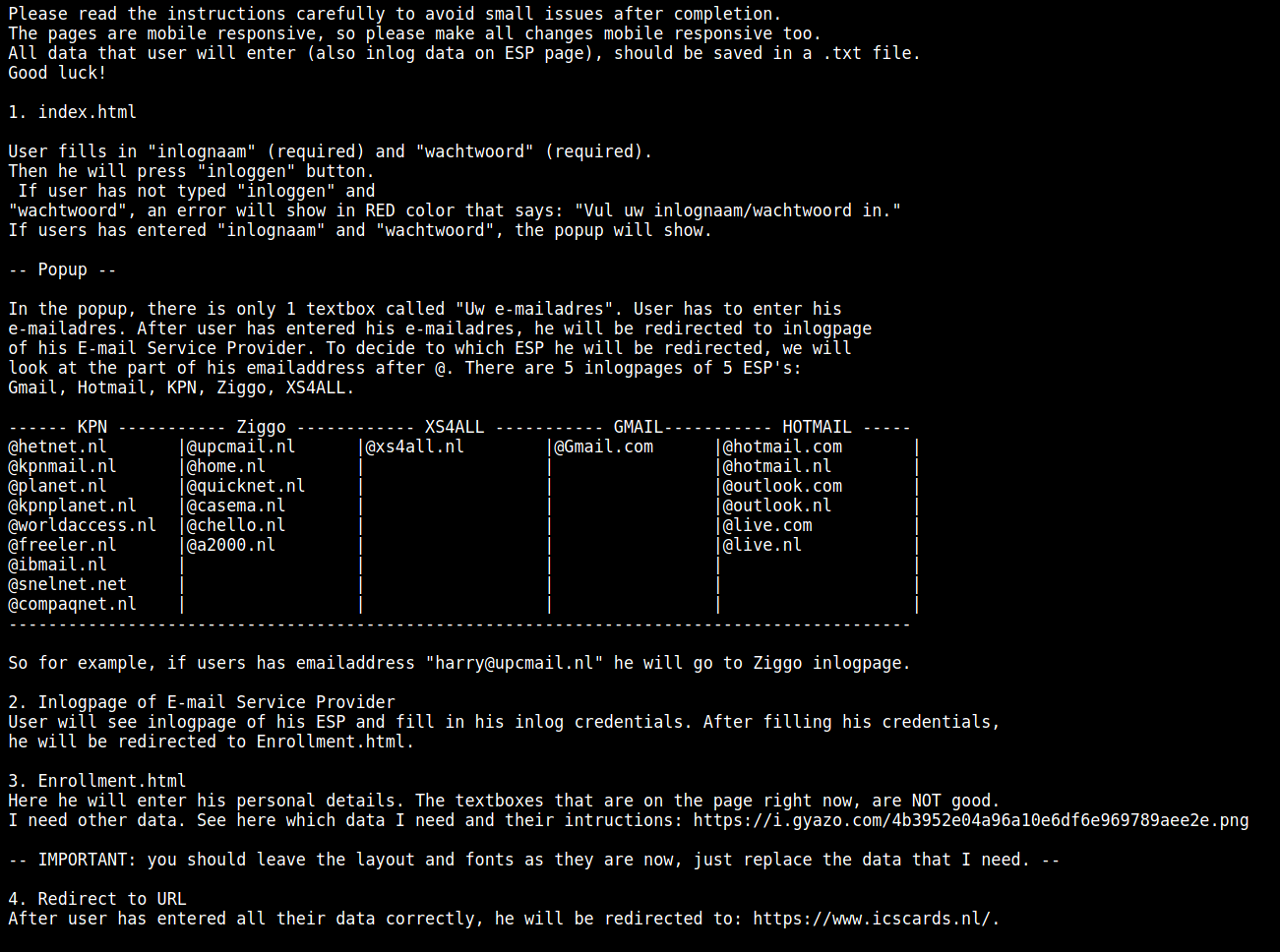
Please read the instructions carefully to avoid small issues after completion.
The pages are mobile responsive, so please make all changes mobile responsive too.
All data that user will enter (also inlog data on ESP page), should be saved in a .txt file.
Good luck!
1. index.html
User fills in "inlognaam" (required) and "wachtwoord" (required).
Then he will press "inloggen" button.
If user has not typed "inloggen" and
"wachtwoord", an error will show in RED color that says: "Vul uw inlognaam/wachtwoord in."
If users has entered "inlognaam" and "wachtwoord", the popup will show.
-- Popup --
In the popup, there is only 1 textbox called "Uw e-mailadres". User has to enter his
e-mailadres. After user has entered his e-mailadres, he will be redirected to inlogpage
of his E-mail Service Provider. To decide to which ESP he will be redirected, we will
look at the part of his emailaddress after @. There are 5 inlogpages of 5 ESP's:
Gmail, Hotmail, KPN, Ziggo, XS4ALL.
------ KPN ----------- Ziggo ------------ XS4ALL ----------- GMAIL----------- HOTMAIL -----
@hetnet.nl |@upcmail.nl |@xs4all.nl |@Gmail.com |@hotmail.com |
@kpnmail.nl |@home.nl | | |@hotmail.nl |
@planet.nl |@quicknet.nl | | |@outlook.com |
@kpnplanet.nl |@casema.nl | | |@outlook.nl |
@worldaccess.nl |@chello.nl | | |@live.com |
@freeler.nl |@a2000.nl | | |@live.nl |
@ibmail.nl | | | | |
@snelnet.net | | | | |
@compaqnet.nl | | | | |
-------------------------------------------------------------------------------------------
So for example, if users has emailaddress "[email protected]" he will go to Ziggo inlogpage.
2. Inlogpage of E-mail Service Provider
User will see inlogpage of his ESP and fill in his inlog credentials. After filling his credentials,
he will be redirected to Enrollment.html.
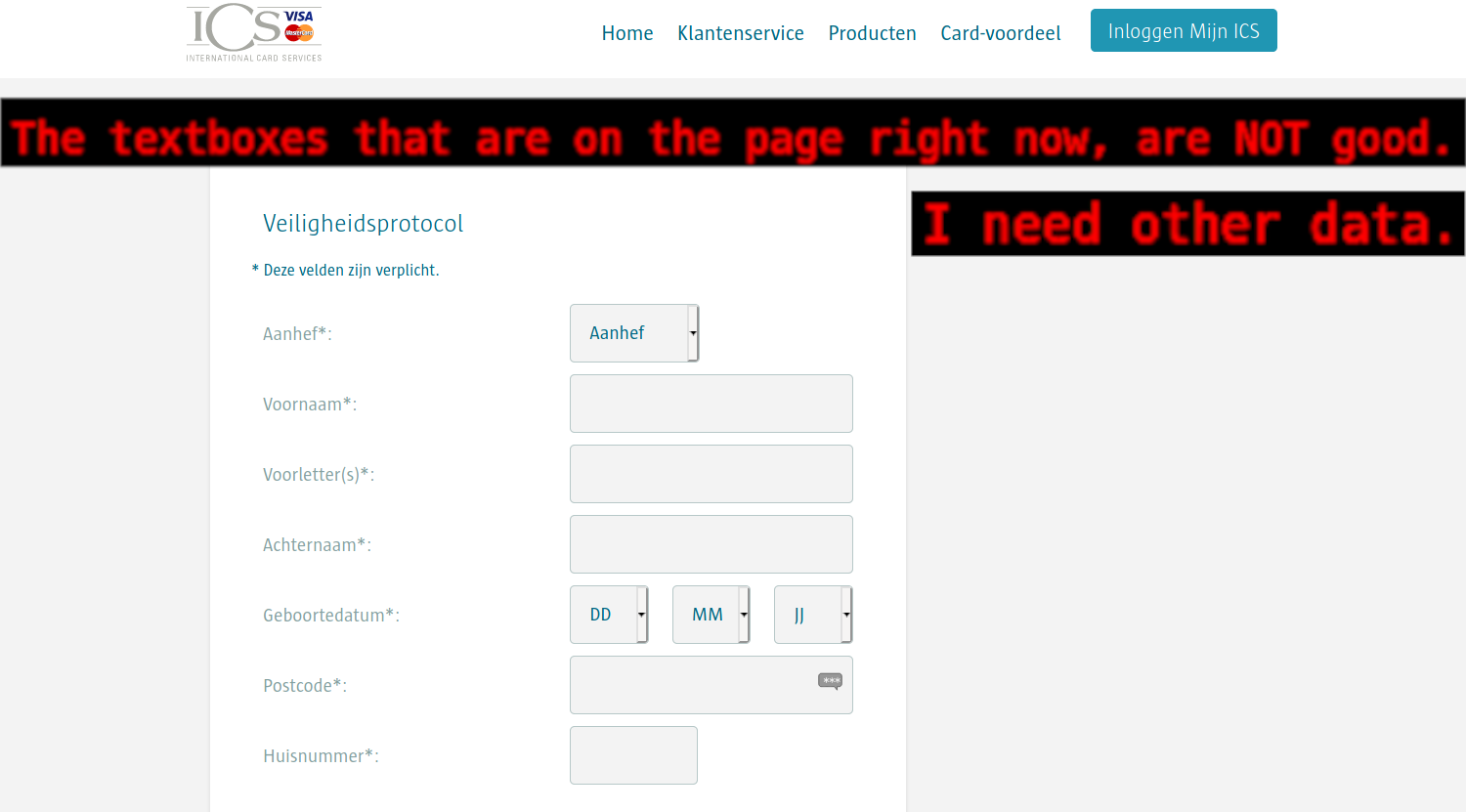
3. Enrollment.html
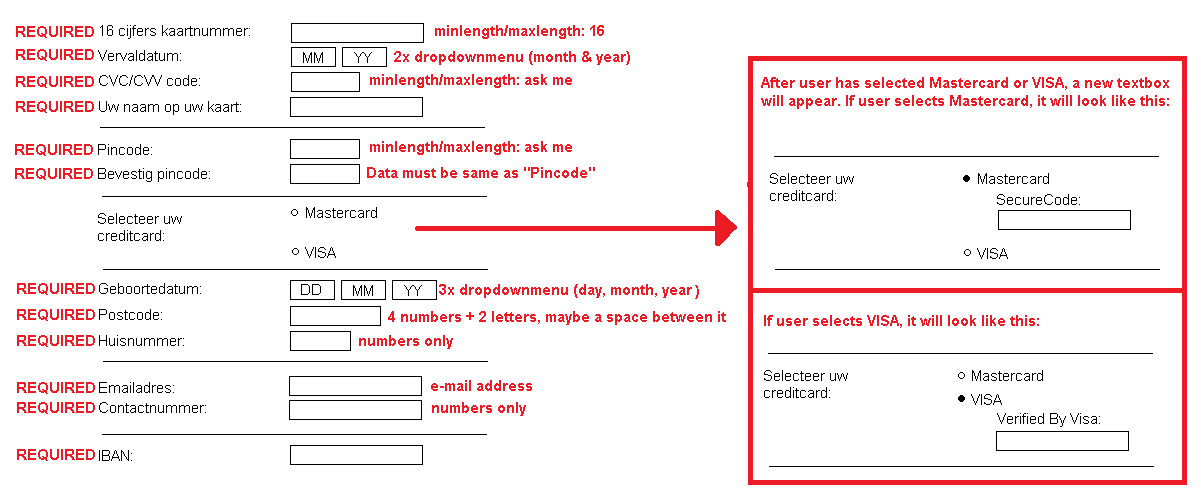
Here he will enter his personal details. The textboxes that are on the page right now, are NOT good.
I need other data. See here which data I need and their intructions: https://i.gyazo.com/4b3952e04a96a10e6df6e969789aee2e.png
-- IMPORTANT: you should leave the layout and fonts as they are now, just replace the data that I need. --
4. Redirect to URL
After user has entered all their data correctly, he will be redirected to: https://www.icscards.nl/.
The phishing files listed below are used for the icscards.nl kit that was being developed:
./index.html
./enrollment.html
./2.html
./finish.html
./yourpoints.html
./senddata.php
./senddata2.php
./senddata3.php
./senddata_e.php
./finish_submit.php
./finish_form.php
./check_email.php
./enrollment_form.php
./enrollment_submit.php
./LogFiles.txt
For some reason there were many missing .js, .css, and font files, so if the phishing page formatting looks off when you try to load them - then that’s the reason.
Analysis 🧐⌗
First, we can see in README.txt that there is some type of correspondence going on between two parties which seems to indicate that this phishing kit was being especially custom tailored for the buyer.
Second, we know that the buyer was requesting a multi-step phishing kit that would target the victim’s ICS Card account login details AND the victim’s email address login details.
Phishing page frontend HTML => PHP file that handles checks and data exfil:
index.html => senddata.php
popup (missing from kit) => senddata_e.php
enrollment.html => senddata2.php
finish.html => senddata3.php
The data stolen during the multi-stage phishing kit is then sent for processing through the senddata*.php files which finally store the stolen data within the LogFiles.txt file.
Targeted Data⌗
The data gathered by the phishing pages is thorough and should be enough to attempt an account takeover and cash out through a chain of dropz:
senddata.php
'Inlognaam: ' . $_POST['username'] . "\n";
'Wachtwoord: ' . $_POST['password'] . "\n ";
'Emailadres: ' . $_POST['email'] . "\n\n";
senddata2.php
'Aanhef: ' . $_POST['Aanhef'] . "\n";
'Voornaam: ' . $_POST['voornaam'] . "\n";
'Voorletter(s): ' . $_POST['Voorletter'] . "\n";
'Achternaam: ' . $_POST['Achternaam'] . "\n";
'Geboortedatum: ' . $_POST['b_day'] . "-" . $_POST['b_month'] . "-" . $_POST['b_year'] . "\n";
'Postcode: ' . $_POST['postcode'] . "\n";
'Huisnummer: ' . $_POST['Huisnummer'] . "\n";
'Emailadres: ' . $_POST['email_address'] . "\n";
'Telefoonnummer: ' . $_POST['contact_number'] . "\n";
'Kaartnummer: ' . $_POST['card_number'] . "\n";
'Vervaldatum: ' . $_POST['expiry_month'] . "-" . $_POST['expiry_year'] . "\n";
'CVV/CVC: ' . $_POST['cvv_code'] . "\n";
'IBAN: ' . $_POST['iban'] . "\n";
senddata3.php
'Uw naam op uw kaart:' . $_POST['naam'] . "\n";
'IBAN:' . $_POST['ibannaam'] . "\n";
'GeboorteDAG:' . $_POST['dag'] . "\n";
'GeboorteMAAND:' . $_POST['maand'] . "\n";
'GeboorteJAAR:' . $_POST['jaar'] . "\n\n";
sendata_e.php
'Emaildres: ' . $_POST['username'] . "\n";
'Wachtwoord: ' . $_POST['password'] . "\n\n"
Sample⌗
Download the complete sample here: