_try_action Skimmer Sends Stolen Data To cdn-frontend.com
_try_action is a JavaScript skimmer and exfiltrates the stolen payment data to fake PNG image file at cdn-frontend.com/stat/pix.png
obj_31337 Skimmer Loads From payprocess.org

This skimmer loads from payprocess.org and exfiltrates to processpayment.cc
PHP -> JavaScript Conversion - $dataoo Skimmer
A comparison of a skimmer that an attacker rolled out in separate PHP and JavaScript versions. Big thanks to Baryo (@ctrl__esc)!
An Angrybeaver Has Joined The Skimming Game
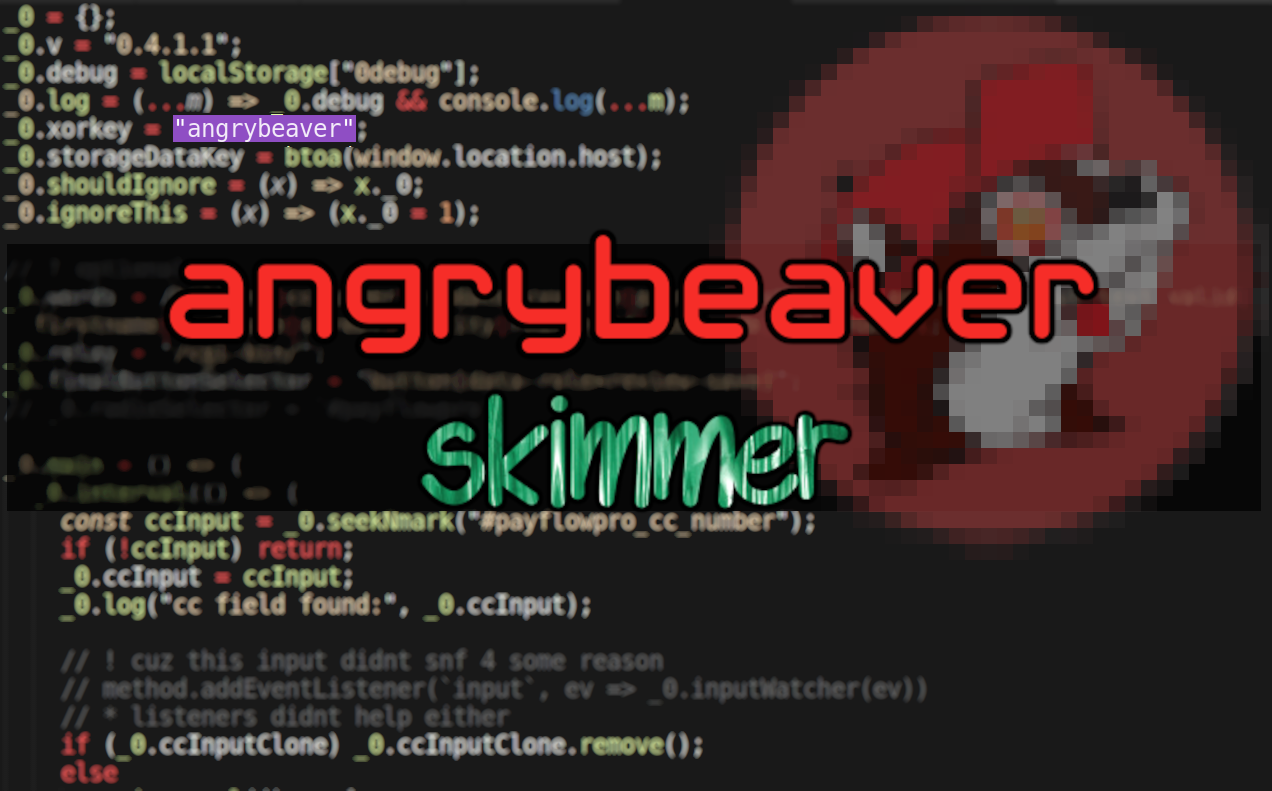
angrybeaver is a skimmer written in JavaScript that is designed to target Payflowpro & authorizenet payments on Magento ecommerce websites. It doesn’t use the same obfuscation techniques that are popular among other JS skimmers.
.wtf() Skimmer Targets WooCommerce PayPal Pro
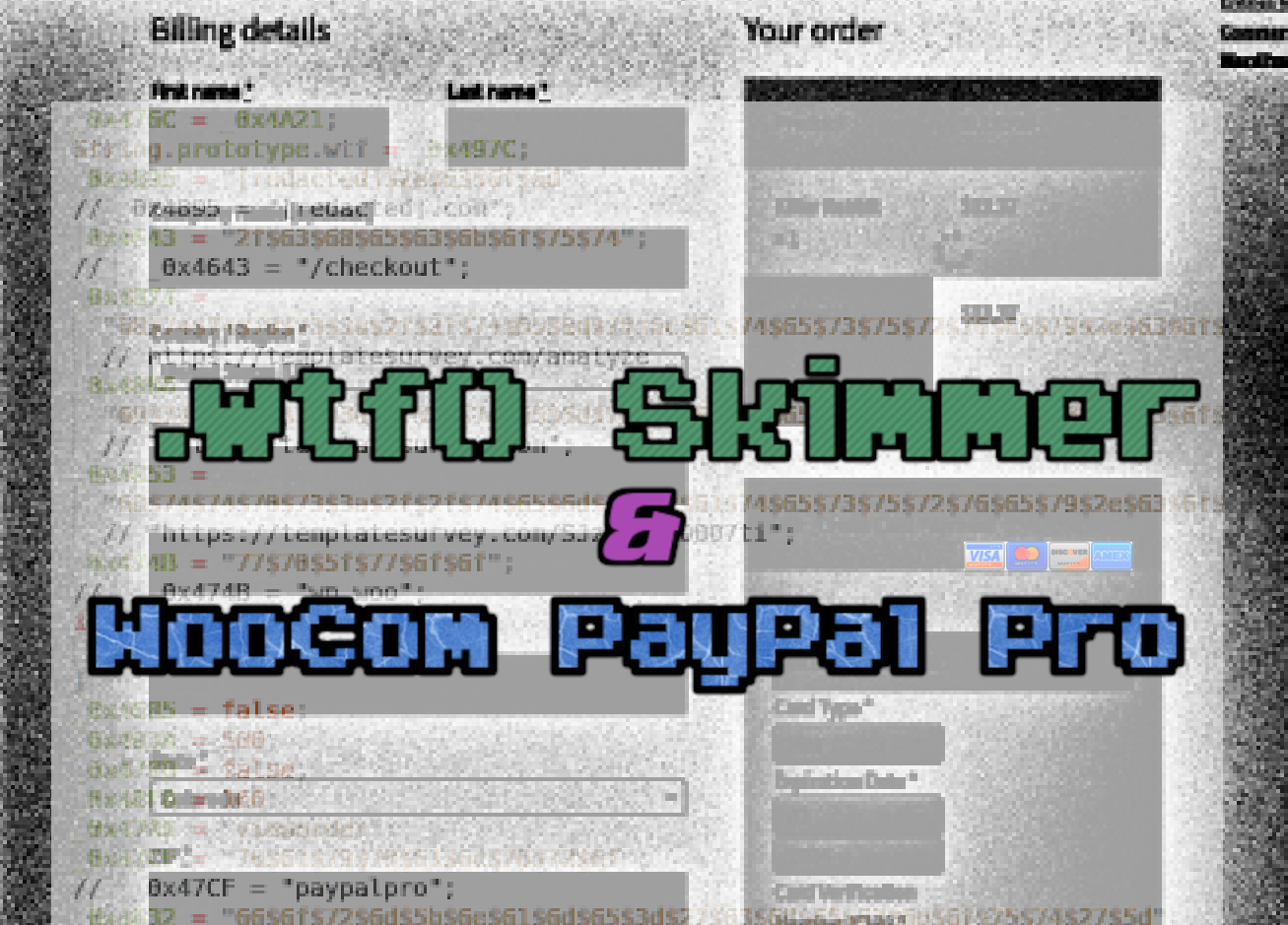
A JavaScript skimmer designed to steal payment data entered into the WooCommerce PayPal Pro gateway on the victim’s infected ecommerce website. Lowkey exfiltration domain: templatesurvey[.]com.