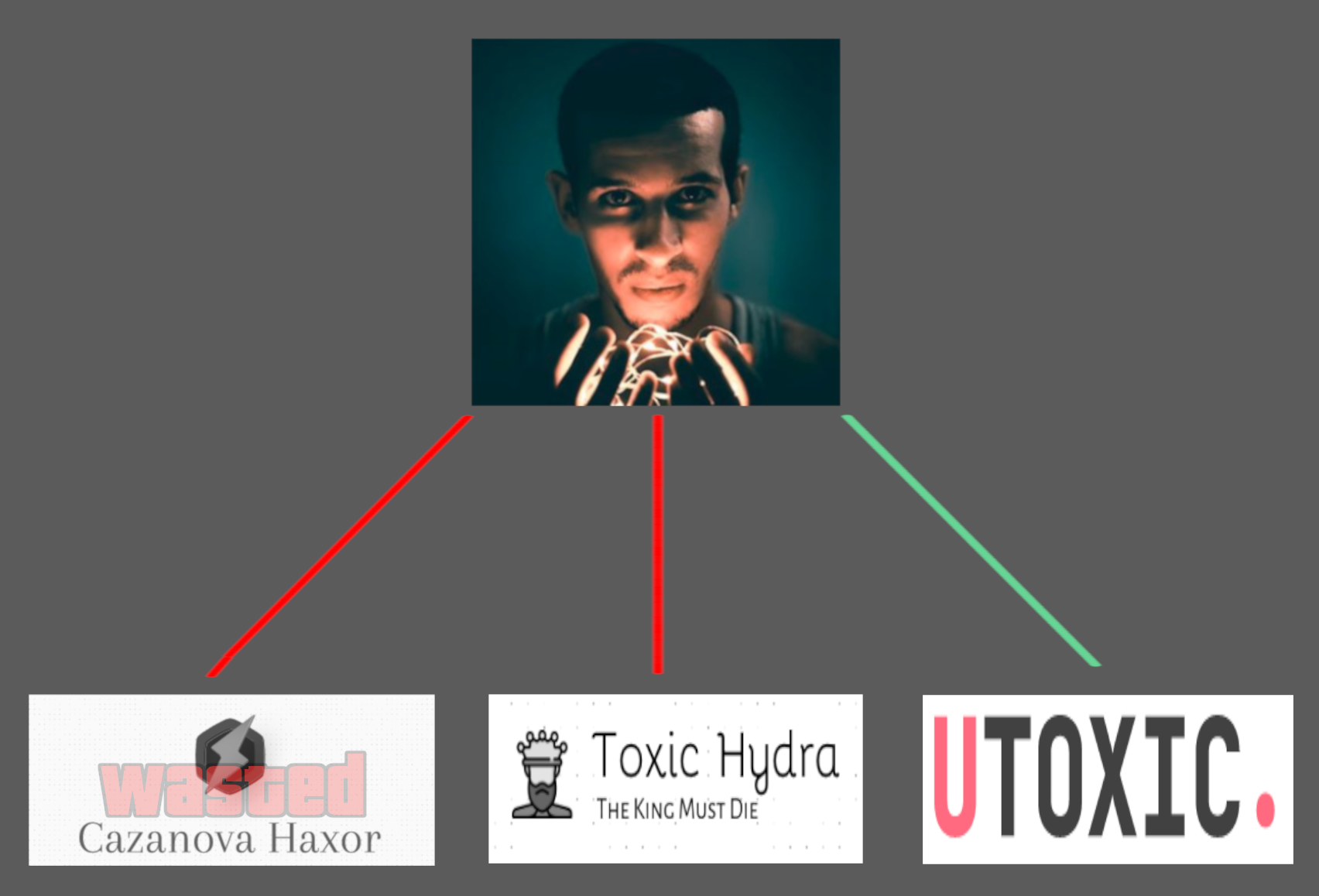
Bad Opsec: xcazanova -> thetoxichydra -> utoxic
Outline
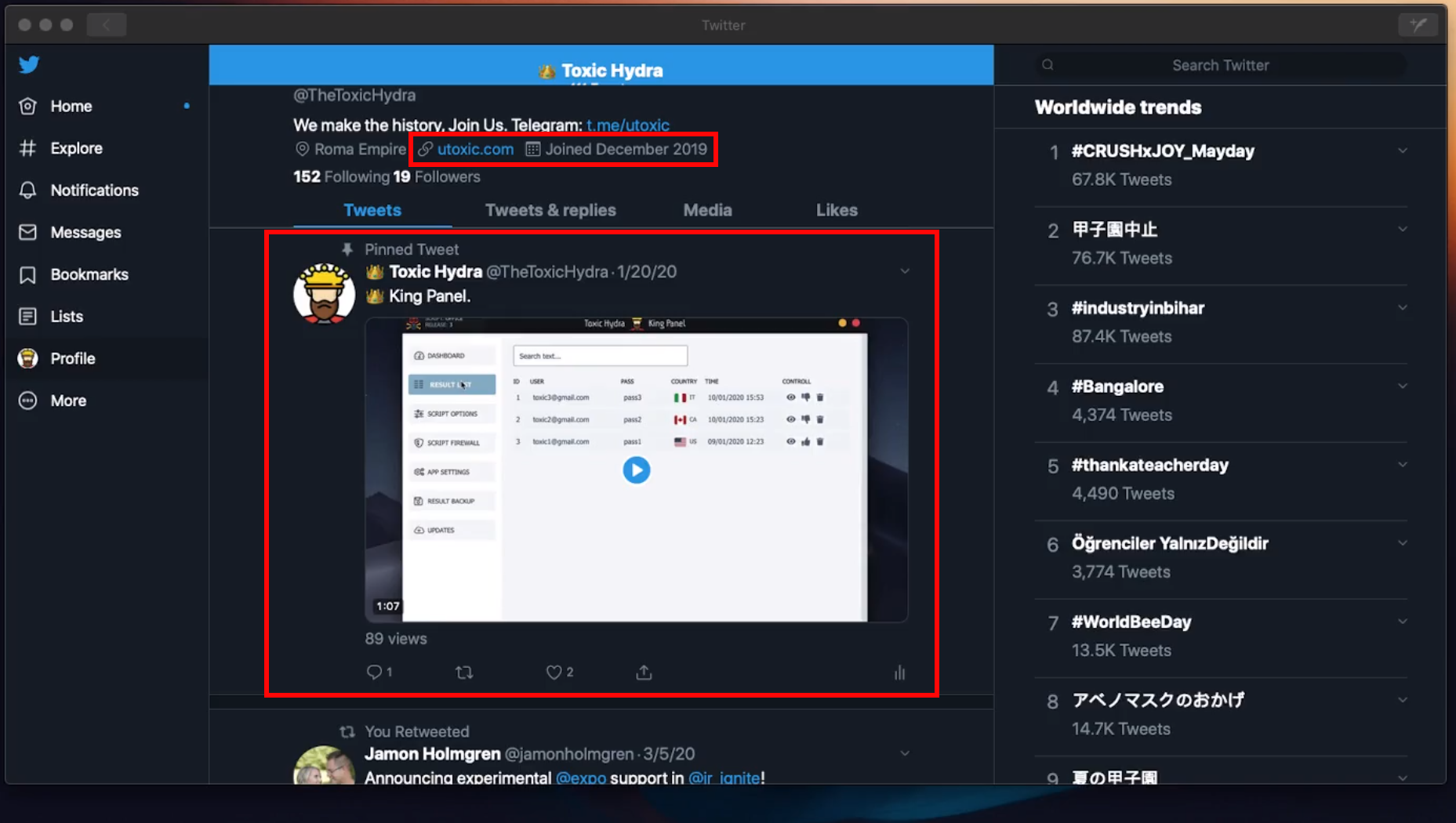
xcazanova -> thetoxichydra -> utoxic⌗
I am very confident that the phishing kit creator and distributor utoxic is the same person that was behind xcazanova: Samir Djelal.
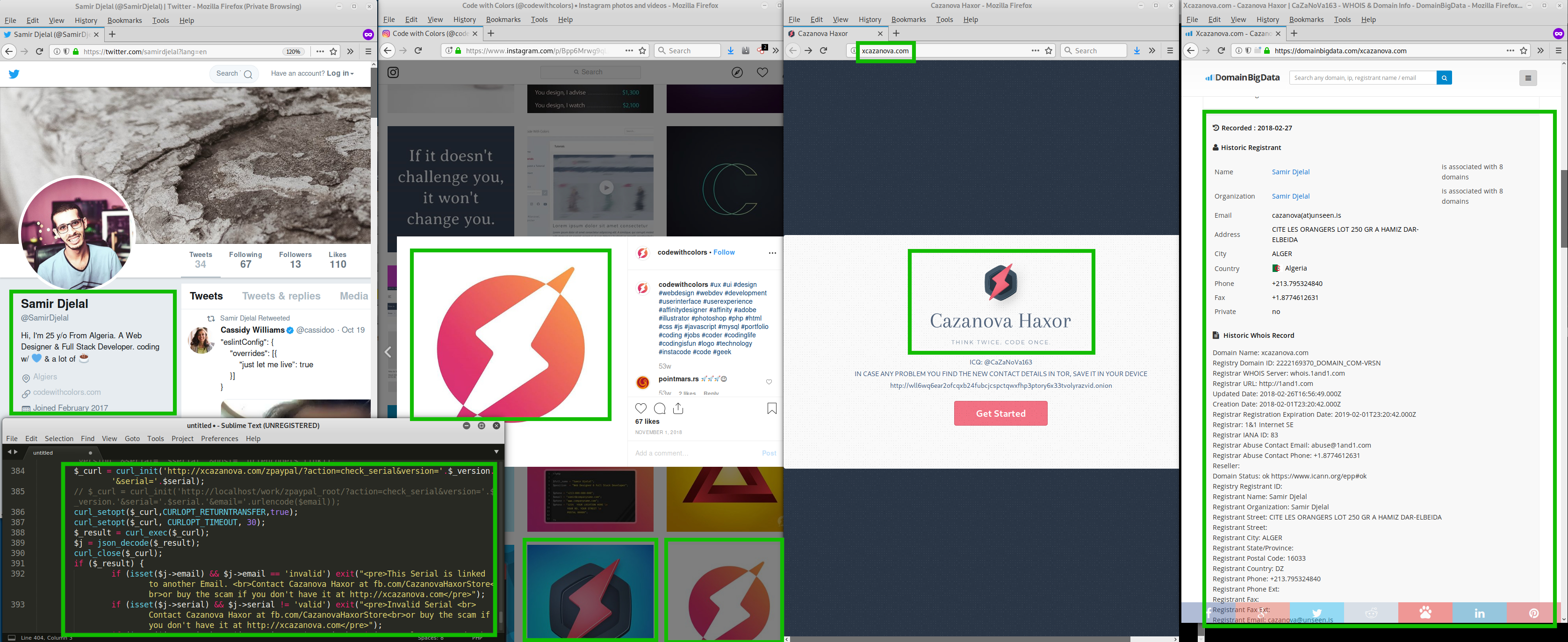
Samir Djelal will deny any involvement, as one would expect, but your boy ain’t buying it.
Allow me to show you why…
Samir Djelal + TheToxicHydra (utoxic)⌗
The first direct linkage between Samir and TheToxicHydra (utoxic) was spotted in a tweet reply.
The tweet was quoted by Samir’s friend, @Anas_Kamoun, and is still online at the time of this writing:
https://twitter.com/Anas_Kamoun/status/1233504899679375360
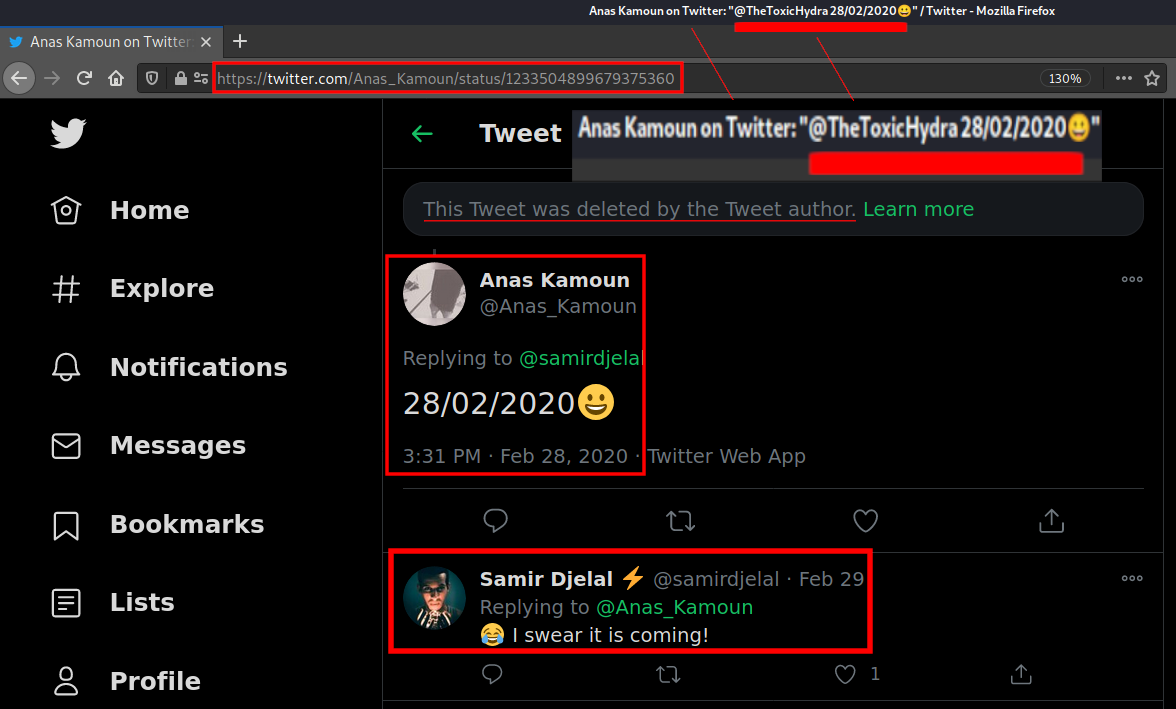
We can see it clearly references a date of Feb 28, 2020 and the deleted Twitter user @TheToxicHydra.
Samir Djelal, @samirdjelal, replied promising that “it is coming”.
I’m going to assume “it” is a reference to a new Office phish kit release under the new alias TheToxicHydra.
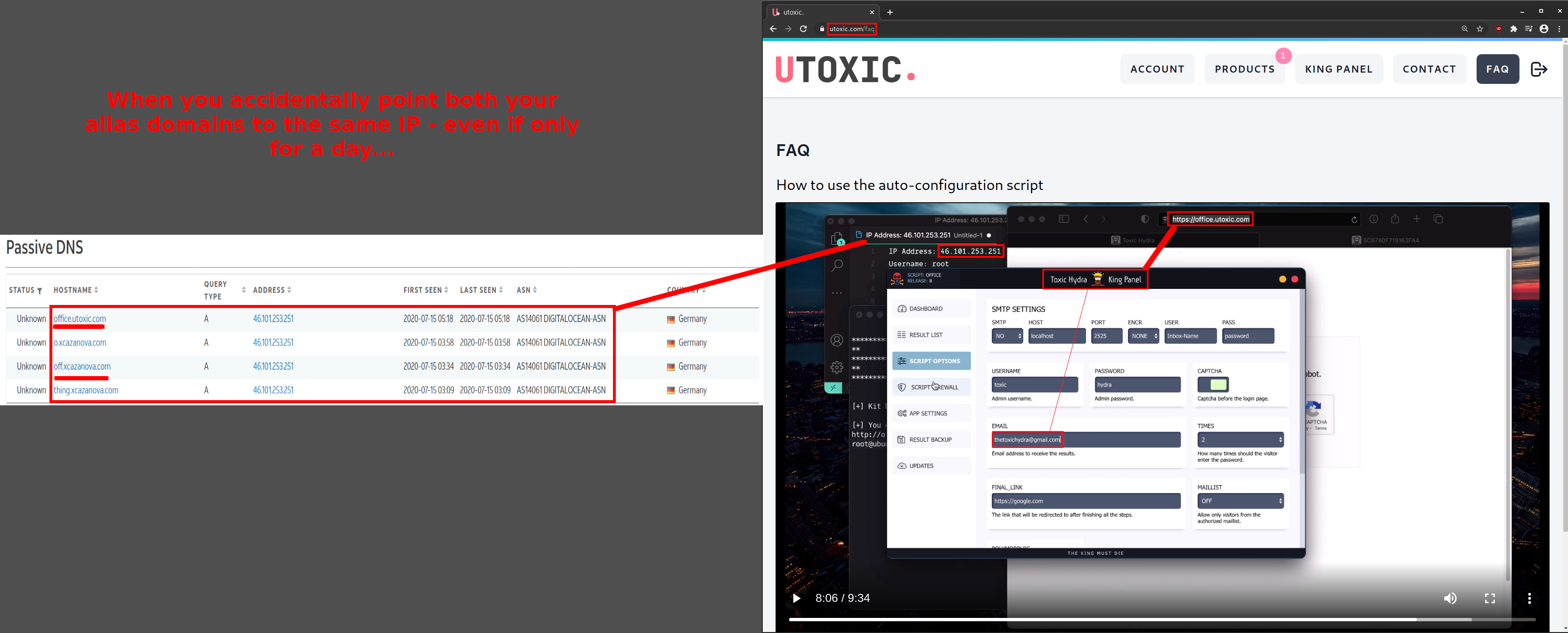
46.101.253.251 passive DNS⌗
If you watch the tutorial video for setting up the phishing kit - then you can see the IP address 46.101.253.251 lurking in the background.
On July 15, 2020 the subdomains office.utoxic.com and off.xcazanova.com were found briefly resolving to the DigitalOcean server IP 46.101.253.251.
Utoxic Tries Email Opsec - Fails Horribly 😂⌗
This one is funny.
So utoxic.com has a mailing list that is used to inform its customers of new product releases. For unknown reasons, they shut down their previously used Telegram channel, so the mailing list is the best way to stay informed.
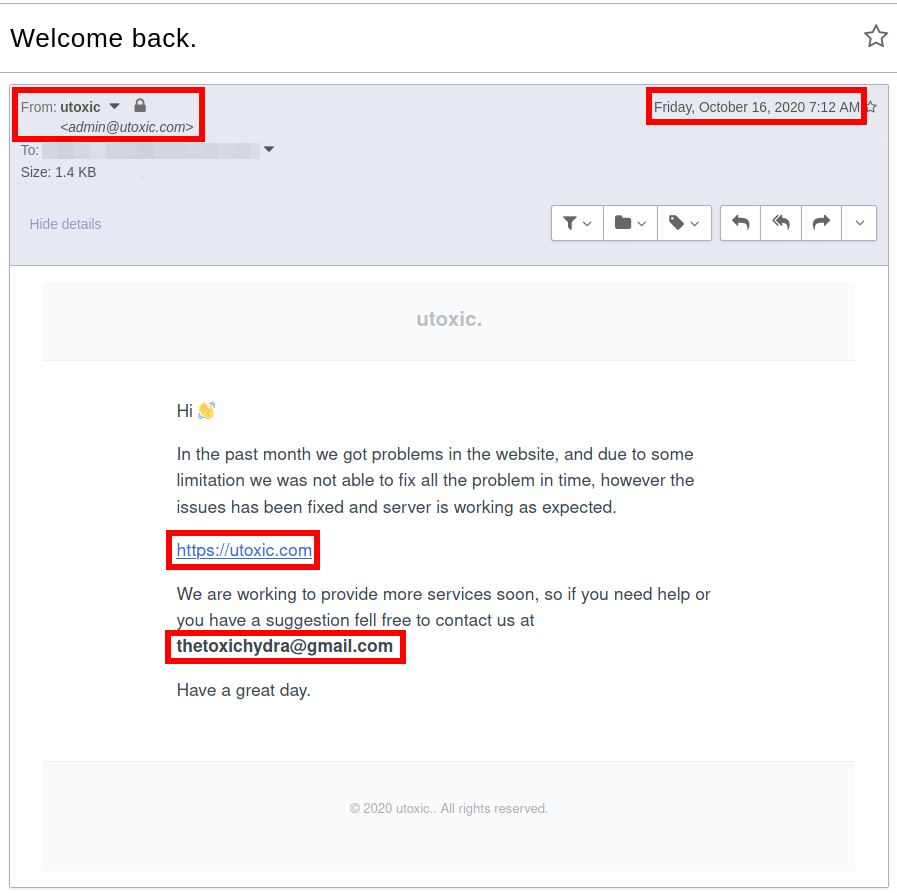
Samir AKA utoxic thought he would be slick and use a compromised email account to send the email to the utoxic.com mailing list.
This is usually used to distance the criminal from the crime - similar to how a criminal may steal a car to use in commission of a more serious crime.
So what went wrong?
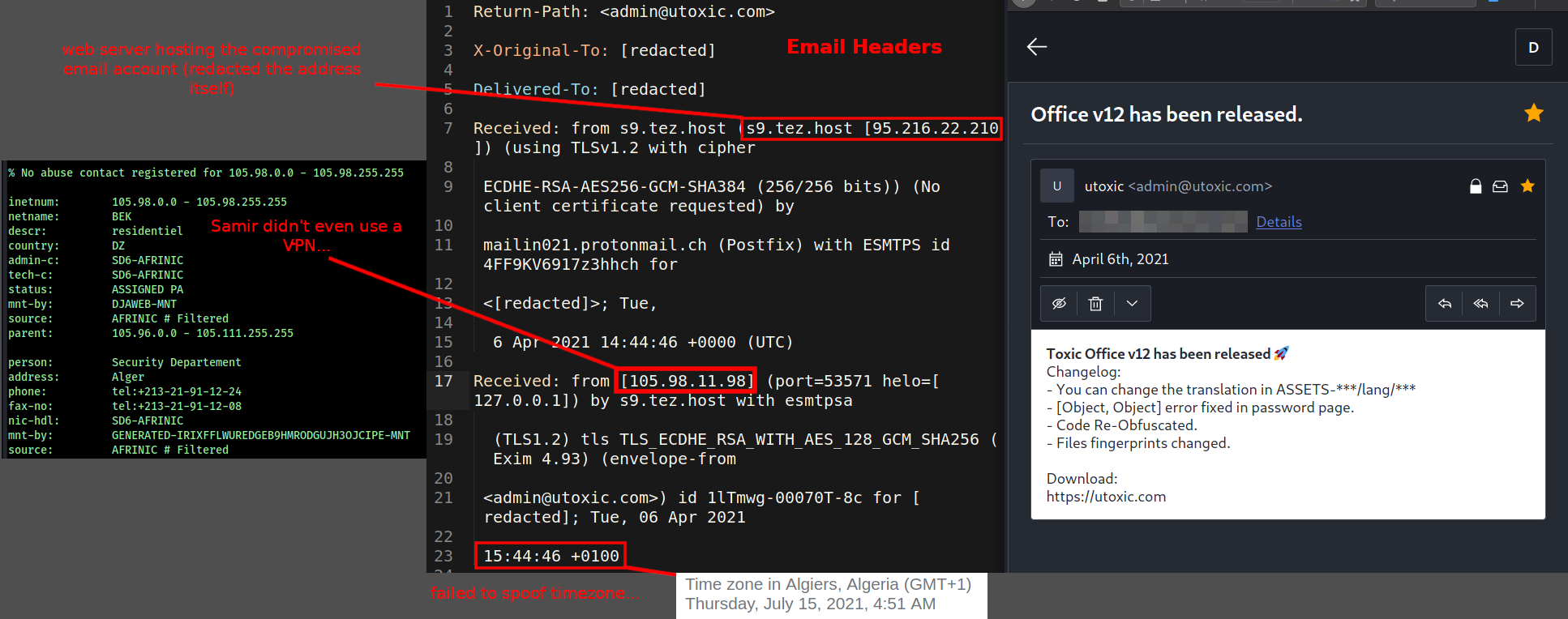
-
Samir doesn’t understand email headers
-
Samir didn’t use a VPN - straight up used a residential Algiers ISP
-
Samir didn’t spoof their timezone - only reinforcing this email was sent by someone in Algeria
Design Element Similarities⌗
Note the faint “print dot” background design found across various creations associated with Samir Djelal - you will probably have to view the full size image and zoom in.
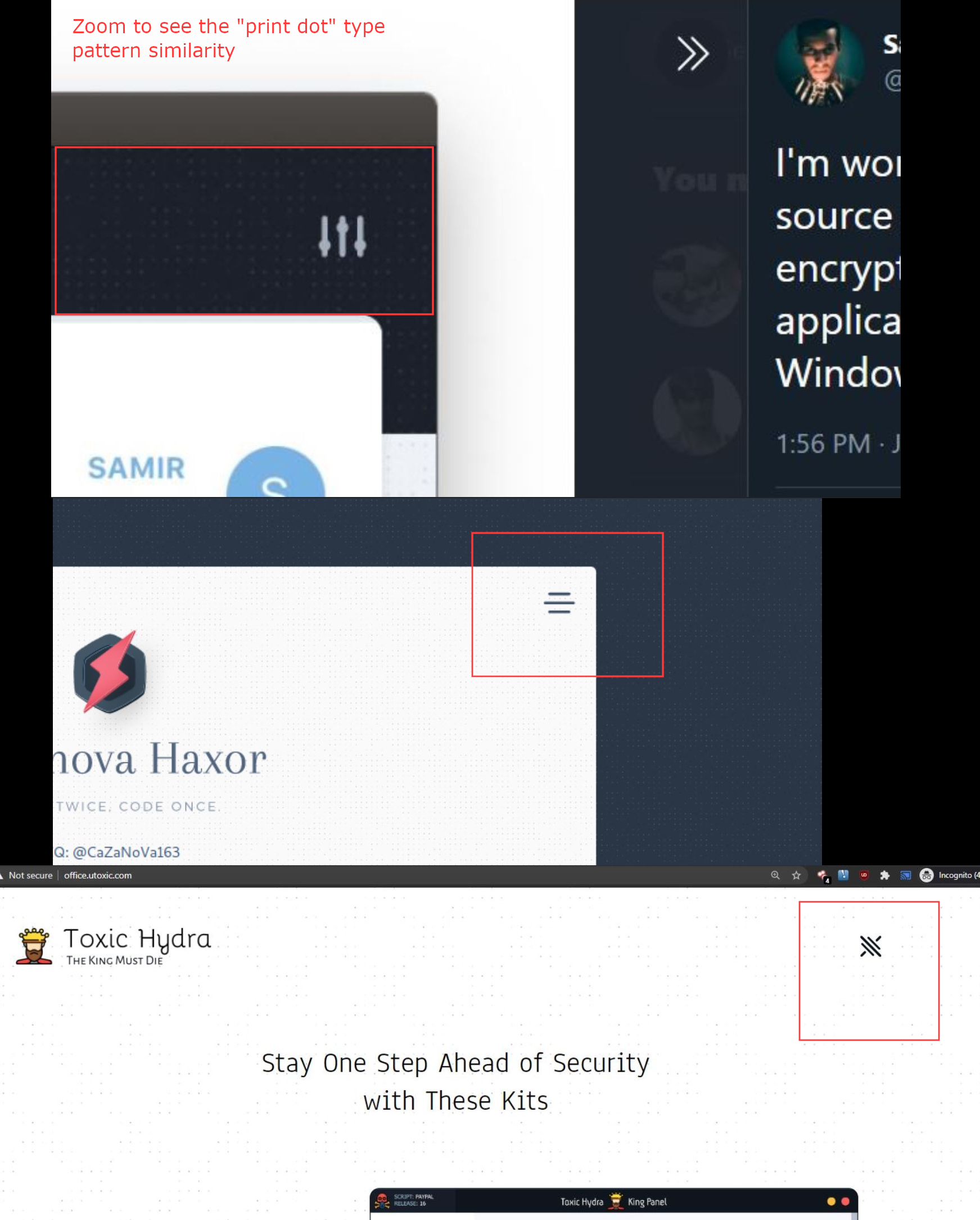
While I wouldn’t depend on something like this for attribution - it only reinforces the theory that these aliases are all operated by Samir Djelal, or someone close to him.
I could be totally off base on this one and it might be much more common than I though, but still thought I would mention it.
Misc Images⌗
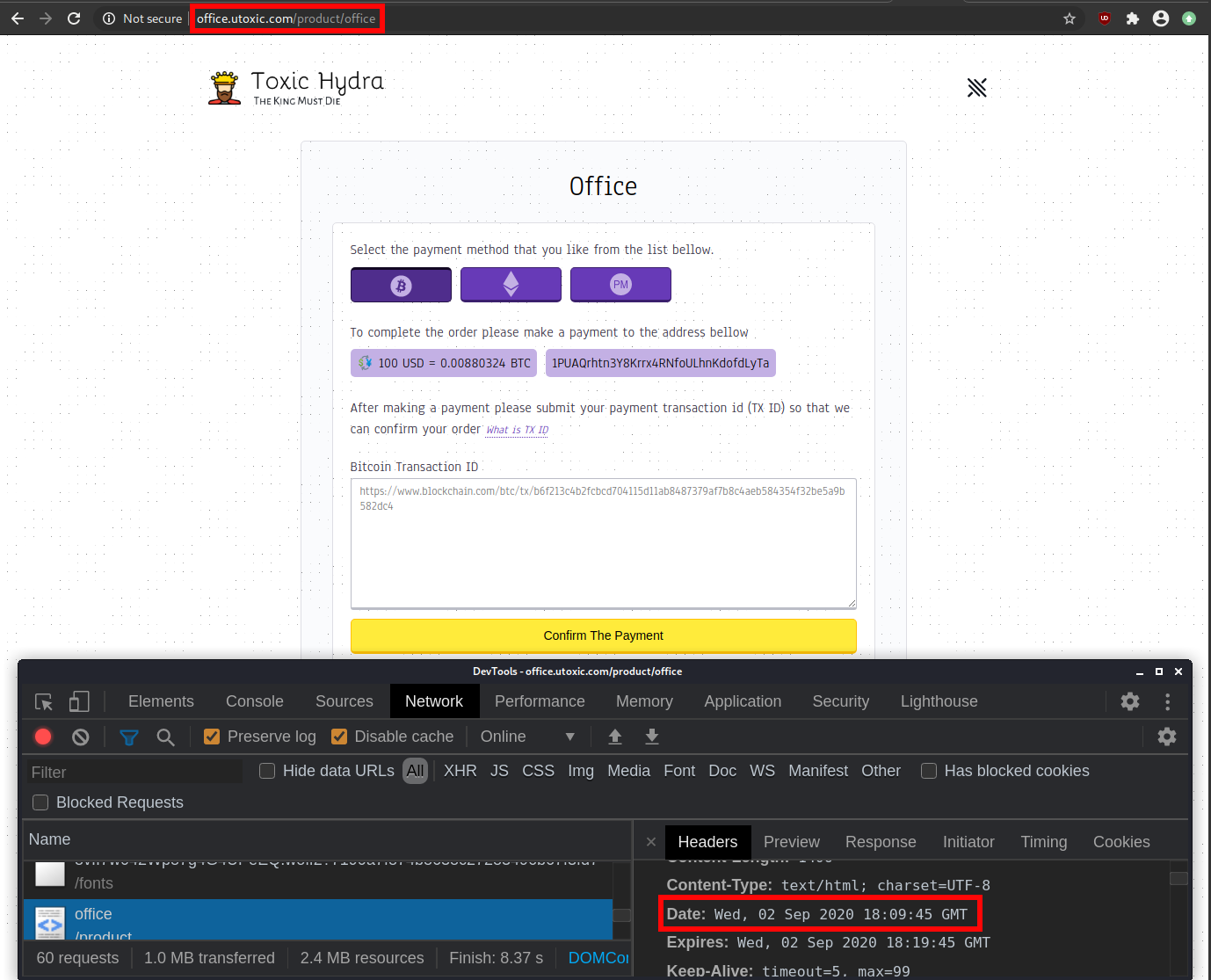
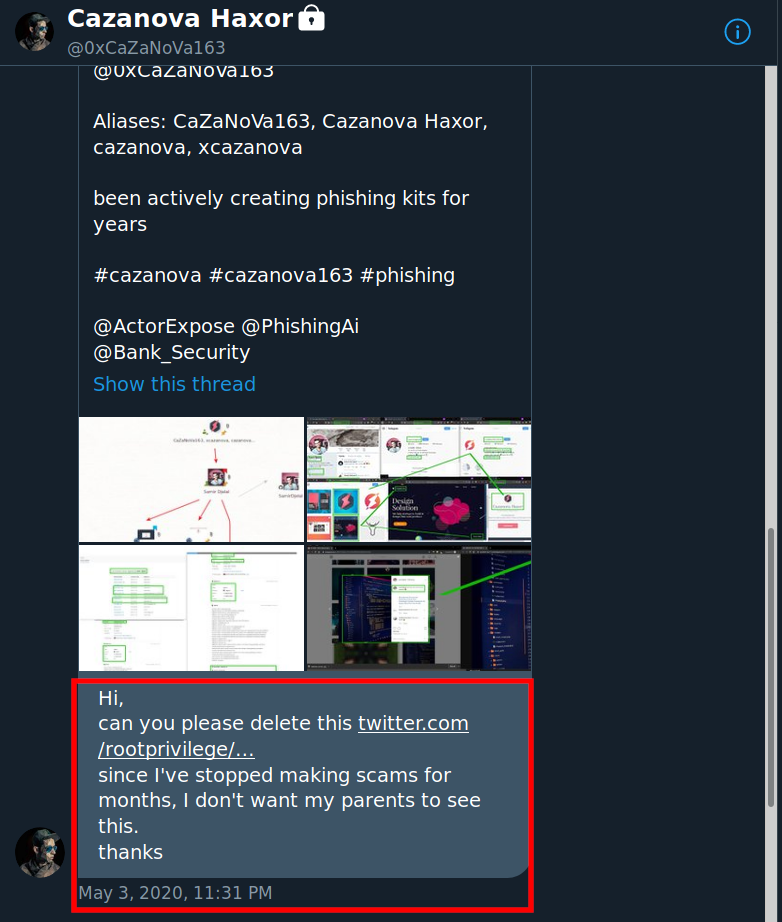
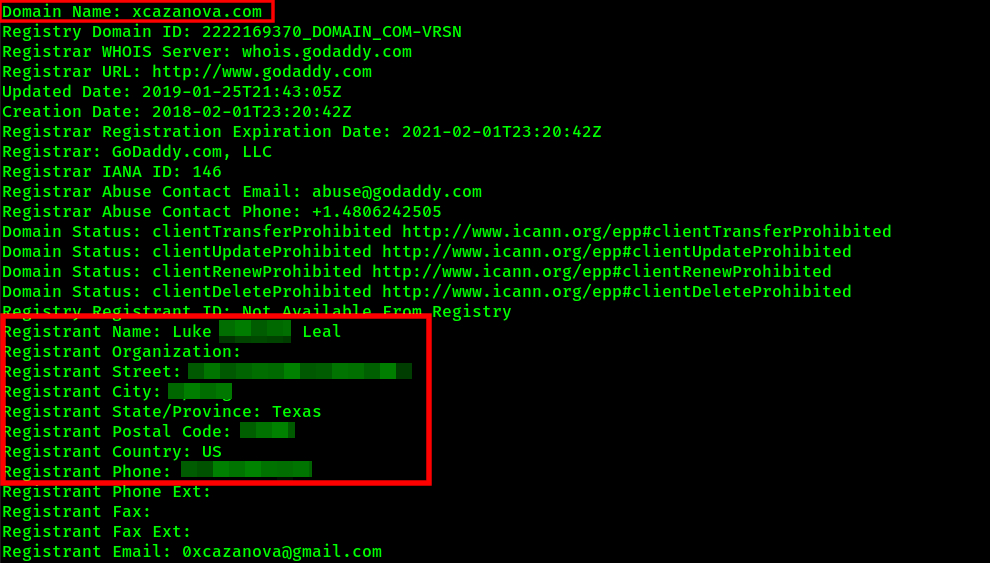
This idiot disabled private whois and put in my personal information as the registration info so that it would look like I owned the malicious domain xcazanova.com whenever someone ran a whois on it.
I guess some half ass way of trying to frame me? Dunno.
“Nothing will happen believe me” - famous last words?⌗
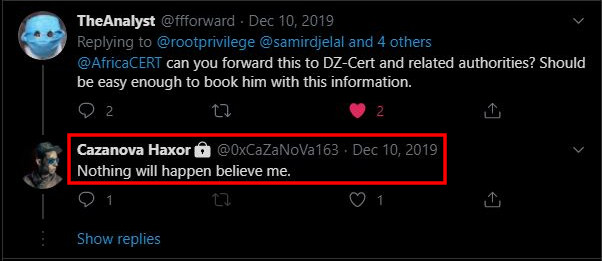
For a while it seemed that Samir Djelal was correct and that he was untouchable in Algeria, however cooperation between North African countries and INTERPOL has greatly increased this year.
In fact they very recently arrested Dr Hex in Morocco, he was also a phishing kit creator.
The suspect is also alleged to have helped develop carding and phishing kits, which were then sold to other individuals through online forums to allow them to facilitate similar malicious campaigns against victims.
Fast money comin' slow, you better think quick 😉