Hidden Tracking Pixel Used To Detect & Track Phishing Pages
Outline
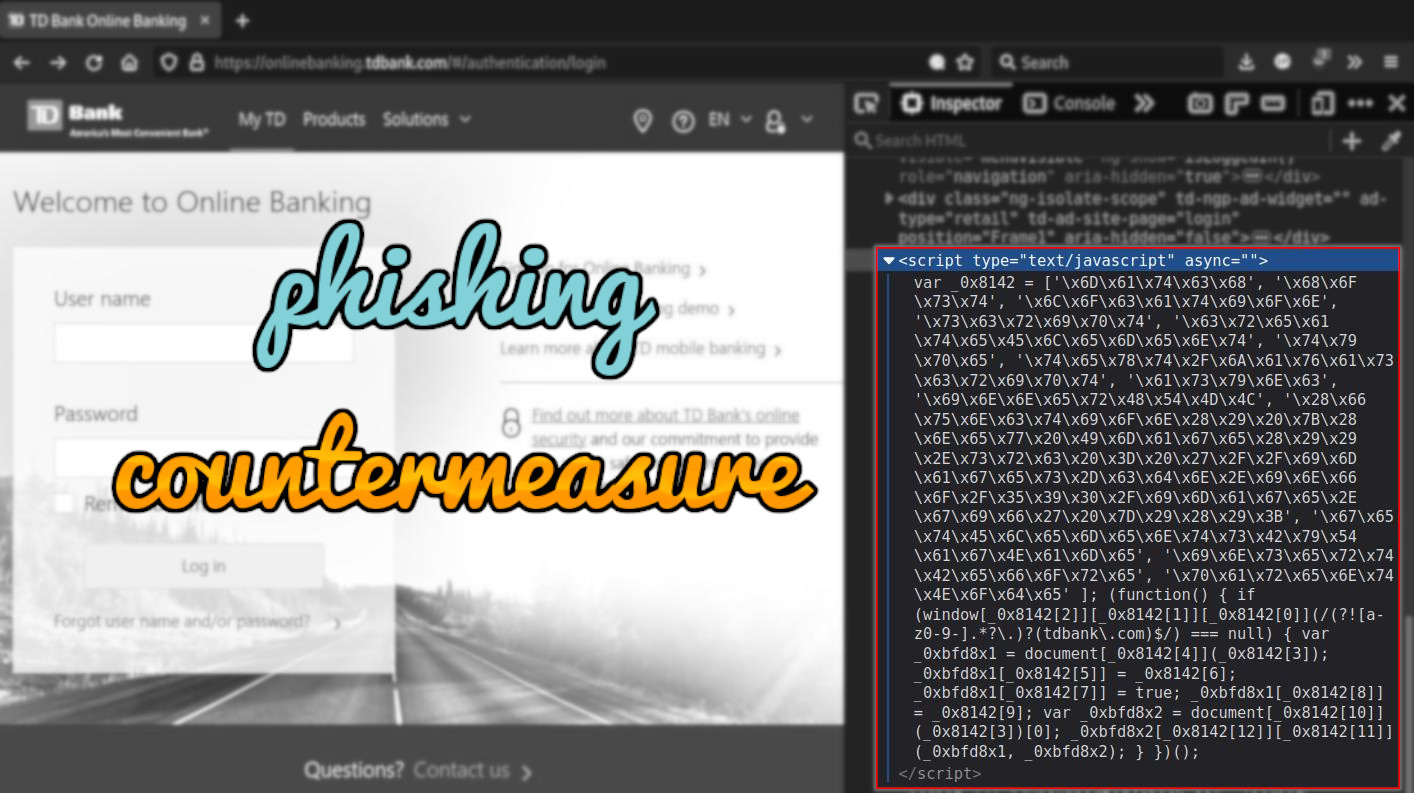
While checking out a phishing kit targeting TD Bank - I noticed a strange piece of obfuscated JavaScript in the source HTML:
var _0x8142 = ['\x6D\x61\x74\x63\x68', '\x68\x6F\x73\x74', '\x6C\x6F\x63\x61\x74\x69\x6F\x6E', '\x73\x63\x72\x69\x70\x74', '\x63\x72\x65\x61\x74\x65\x45\x6C\x65\x6D\x65\x6E\x74', '\x74\x79\x70\x65', '\x74\x65\x78\x74\x2F\x6A\x61\x76\x61\x73\x63\x72\x69\x70\x74', '\x61\x73\x79\x6E\x63', '\x69\x6E\x6E\x65\x72\x48\x54\x4D\x4C', '\x28\x66\x75\x6E\x63\x74\x69\x6F\x6E\x28\x29\x20\x7B\x28\x6E\x65\x77\x20\x49\x6D\x61\x67\x65\x28\x29\x29\x2E\x73\x72\x63\x20\x3D\x20\x27\x2F\x2F\x69\x6D\x61\x67\x65\x73\x2D\x63\x64\x6E\x2E\x69\x6E\x66\x6F\x2F\x35\x39\x30\x2F\x69\x6D\x61\x67\x65\x2E\x67\x69\x66\x27\x20\x7D\x29\x28\x29\x3B', '\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x73\x42\x79\x54\x61\x67\x4E\x61\x6D\x65', '\x69\x6E\x73\x65\x72\x74\x42\x65\x66\x6F\x72\x65', '\x70\x61\x72\x65\x6E\x74\x4E\x6F\x64\x65' ]; (function() { if (window[_0x8142[2]][_0x8142[1]][_0x8142[0]](/(?![a-z0-9-].*?\.)?(tdbank\.com)$/) === null) { var _0xbfd8x1 = document[_0x8142[4]](_0x8142[3]); _0xbfd8x1[_0x8142[5]] = _0x8142[6]; _0xbfd8x1[_0x8142[7]] = true; _0xbfd8x1[_0x8142[8]] = _0x8142[9]; var _0xbfd8x2 = document[_0x8142[10]](_0x8142[3])[0]; _0xbfd8x2[_0x8142[12]][_0x8142[11]](_0xbfd8x1, _0xbfd8x2); } })();
Tracking Pixel Countermeasure⌗
After deobfuscating we are left with plaintext JavaScript:\
(function () {
if (window.location.host.match(/(?![a-z0-9-].*?\.)?(tdbank\.com)$/) === null) {
var _0xbfd8x1 = document.createElement('script');
_0xbfd8x1.type = 'text/javascript';
_0xbfd8x1.async = true;
_0xbfd8x1.innerHTML = "(function() {(new Image()).src = '//images-cdn.info/590/image.gif' })();";
var _0xbfd8x2 = document.getElementsByTagName('script')[0];
_0xbfd8x2.parentNode.insertBefore(_0xbfd8x1, _0xbfd8x2);
}
})();
The JavaScript will check the browser’s URL against a regular expression using the function window.location.host.match.
If the URL in the browser does not use the domain tdbank.com then the JavaScript will load the “tracking pixel” by sending a request to the domain images-cdn.info:
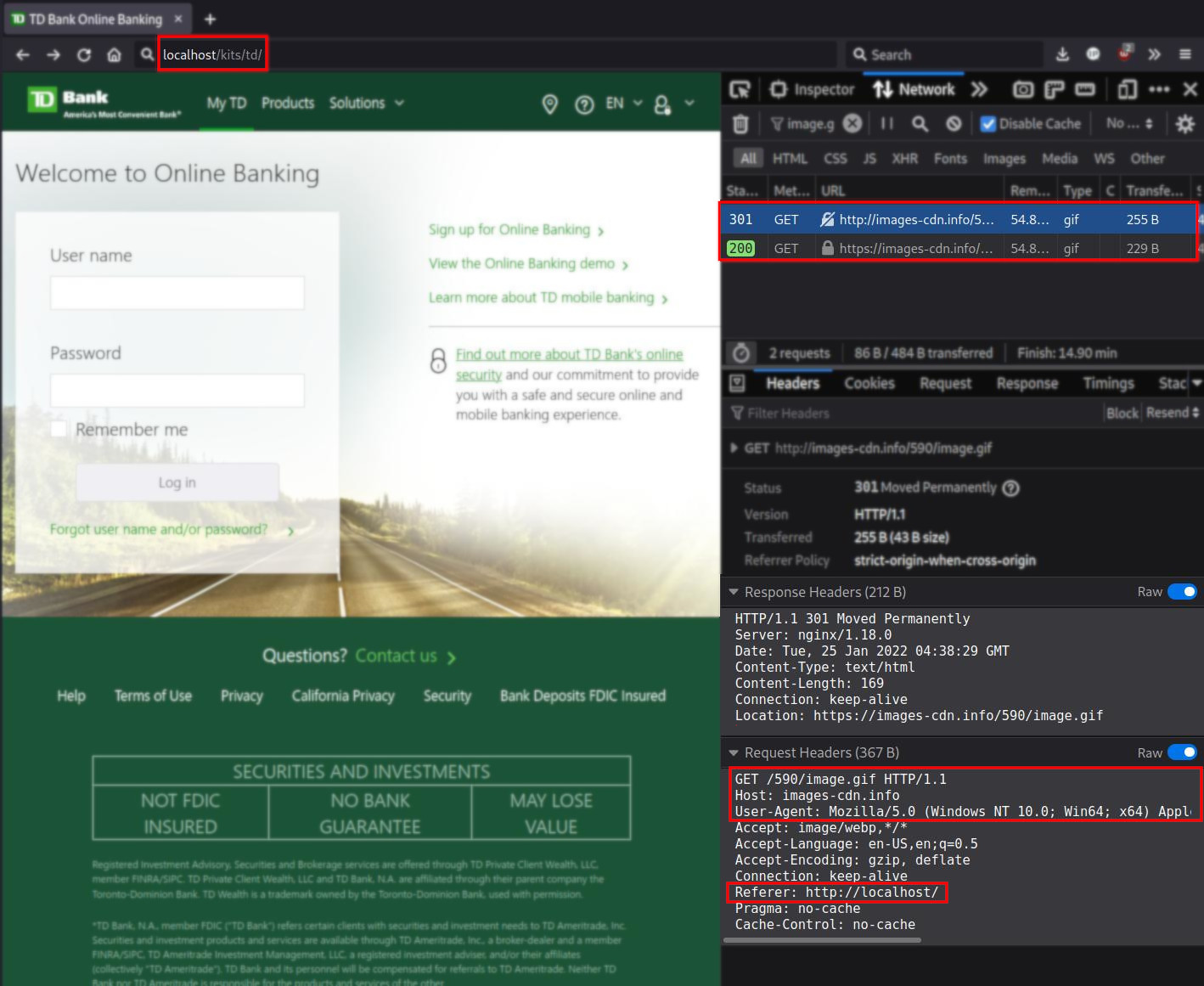
When the HTTP request is sent to images-cdn.info it includes the referer URL in the Referer: field, which reveals the domain name from where the request was sent.
GET /590/image.gif HTTP/1.1
Host: images-cdn.info
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.36
Accept: image/webp,*/*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Referer: http://localhost/
Pragma: no-cache
Cache-Control: no-cache
So for the security company that operates the domain images-cdn.info, they can find new domains that are likely to contain phishing content by just monitoring the Referer: field in the access logs for images-cdn.info.
All it takes is for one person to load the phishing page (e.g often times phishers will test the phishing page) and it will be enough for the page to get taken down.
Why Do Phishing Pages Have This Tracker?⌗
Phishers will often use scraping tools like HTTrack to quickly download the login page resources of their phishing target.
From there they can then modify the downloaded resources to make their phishing page, however they do not always check the existing resources being loaded from the scraped resources.
It’s basically the equivalent of using GPS to track stolen items in real time.
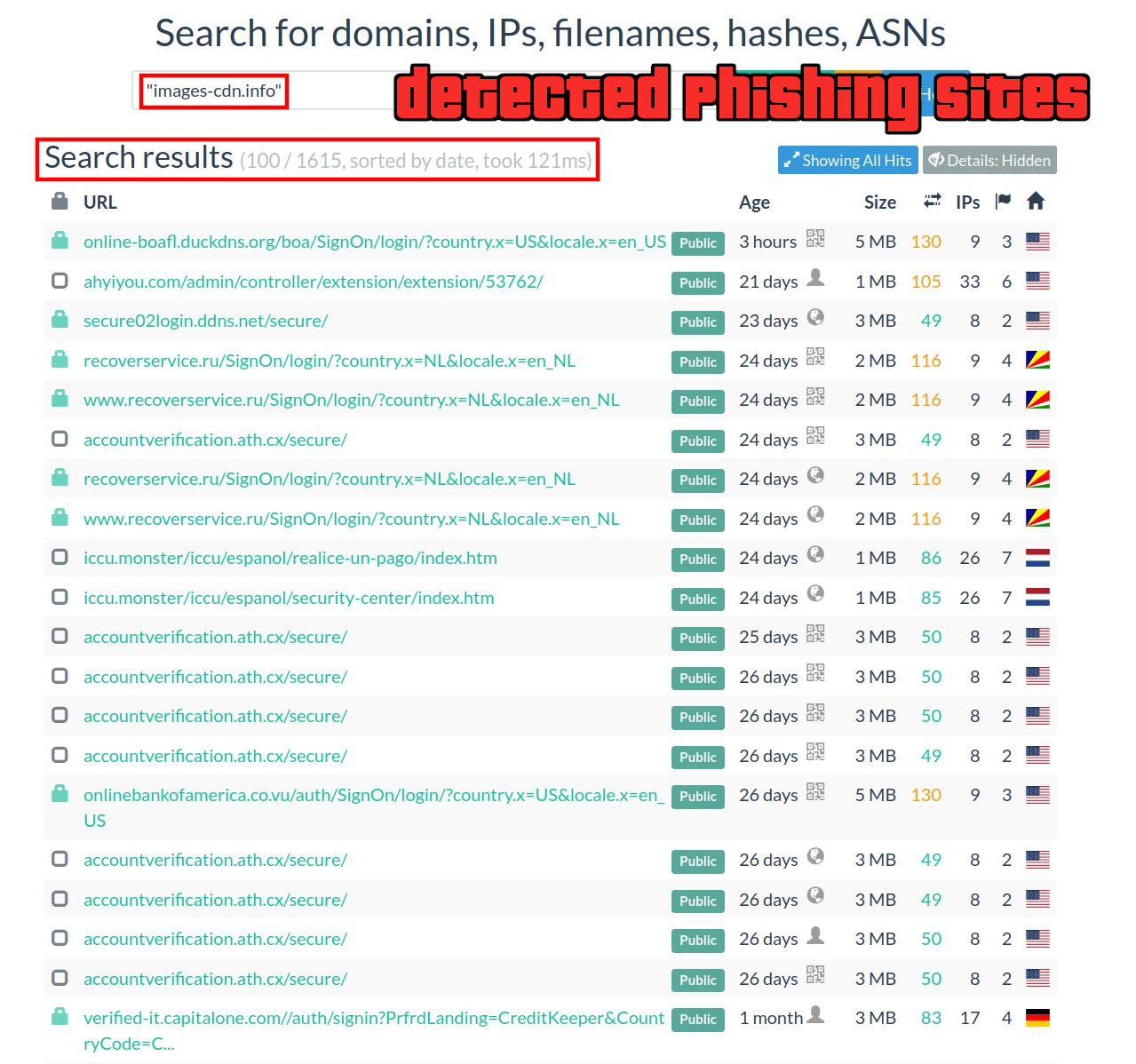
Brand Security Companies⌗
This is a technique that is sometimes employed by different types of brand/phishing security companies seeking to have the latest alerts when a phishing page goes online that unknowingly uses this obfuscated code.
One reason is that it can alert for phishing pages that are set up on domains that are not maliciously registered but have been compromised in some way. This means that such a phishing page would not likely be detected by using an alert system like monitoring domain or SSL/TLS cert registrations for suspicious domains.
I have seen advanced phishing pages that were created using HTTrack, but attackers are also increasingly trying to move away from that method - or they audit the code. This form of code auditing has become necessary on the phisher’s end due to the rampant scamming/stealing that occurs when phishing kits are shared and a backdoor is hidden within it to steal the payment data from the phisher.