Spox is Dila Belimi

Outline
NAME: DILA BELMILI
KNOWN ALIASES: Spox, Spox_dz, Sp0x, seller_62, SPOX CODER, spoxstore, Team Spox, Spoxy
KNOWN LOCATIONS: Mila and Grarem Gouga, Mila Province, Algeria
Intro to Spox⌗
I first covered Spox phishing kits in an old post - which you can view here.
Spox is a phishing kit creator and distributor who has operated since at least 2017, but I didn’t personally start running into his phishing kits until 2019.
Spox Quits After My July 2020 Post? ✌️⌗
Just days after the Sucuri post went live on July 13, 2020, Spox seemed to think it was a good idea to stop his phishing kit operation and said goodbye in his Telegram channel while promising to see us in the next life.
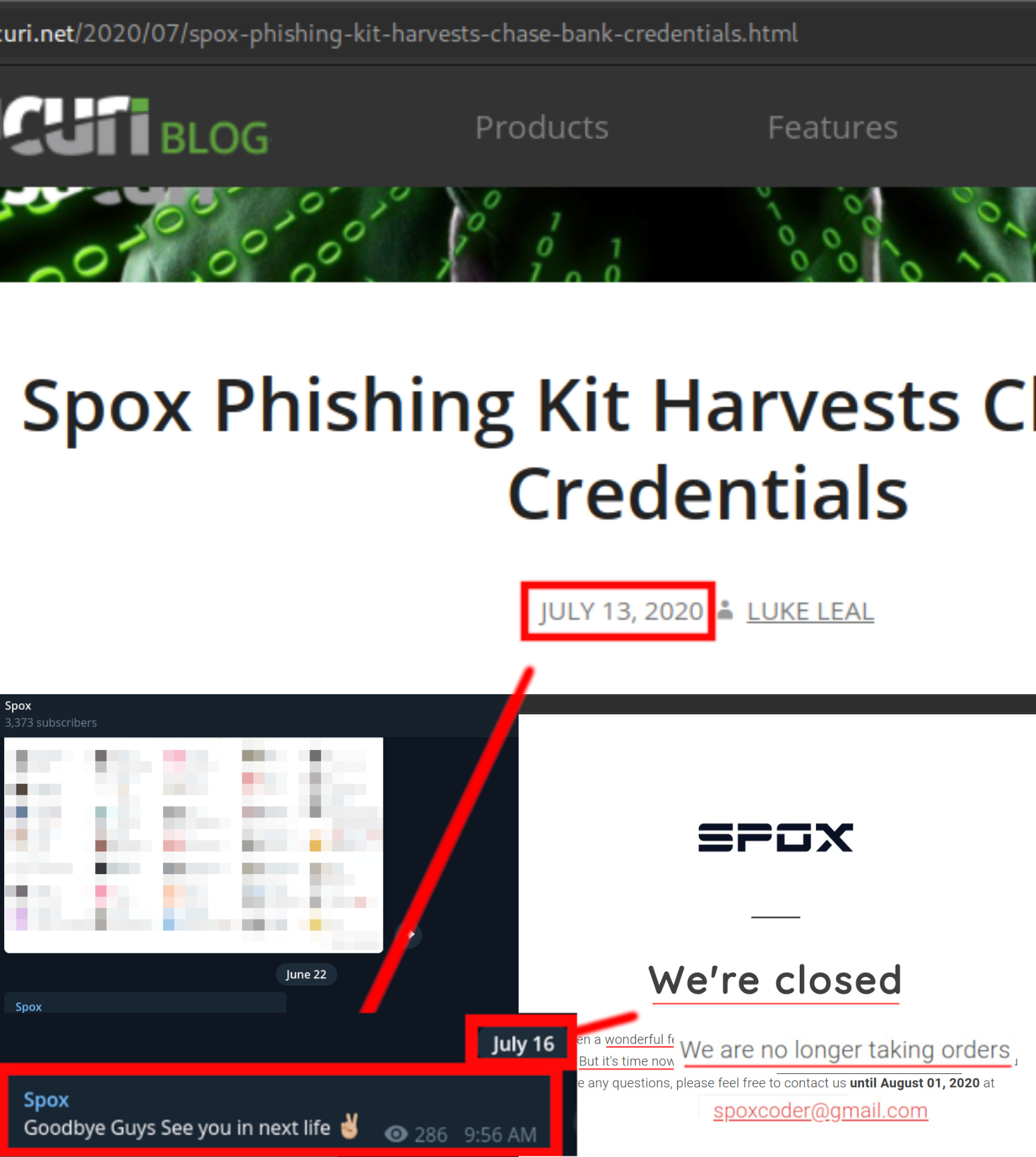
A bit of a dramatic exit, but as long as he actually quits scamming people then I don’t mind.
I knew better than to just take his word that he quit the game. Usually these phishers just ditch the burned alias and start using a new one. I’ll cover more on that in a different post, though.
Spox Confirms Via August 2020 Email He Hasn’t Quit⌗
I decided to wait until the “end of support” date, August 1, 2020, that was listed in the closure message shown on his website spox-coder.xyz (shown in the lower right section of the image collage above).
After the August 1, 2020 date passed, I sent Spox an email asking if he will still be providing updates to his scampages/phishing kits. He enthusiastically said yes! ☠️☠️☠️
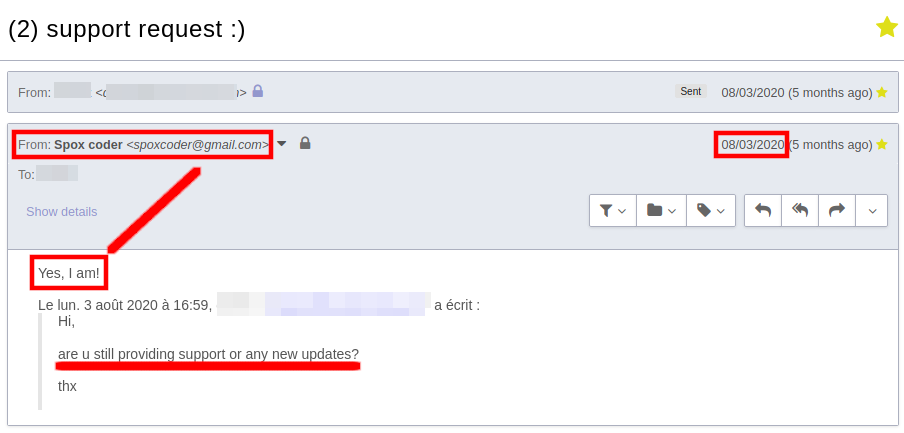
Eventually Spox just removed the “We’re closed” message from his websites spox-coder.xyz and market0day.com, then resumed selling phishing kits from market0day.com.
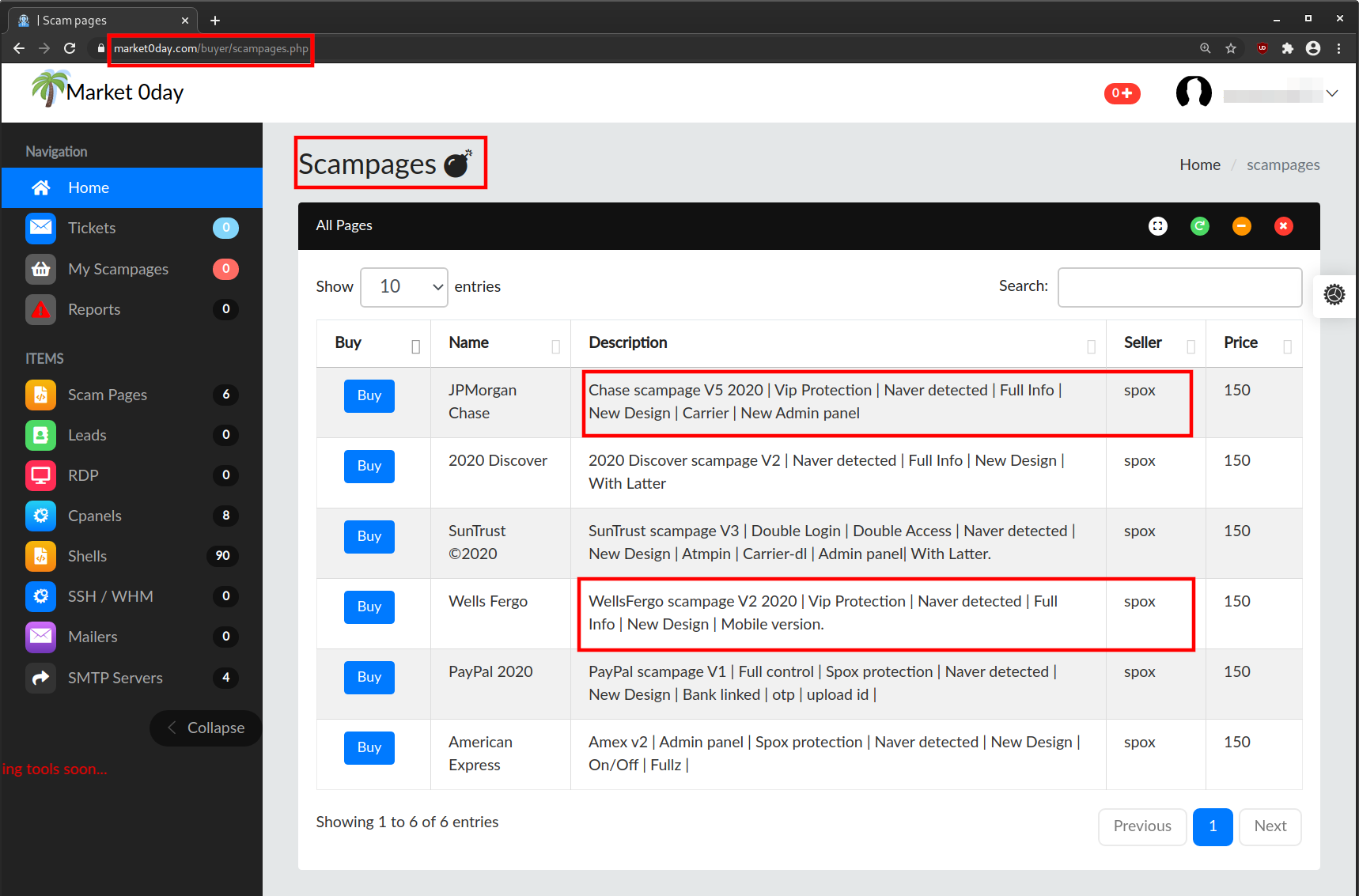
Spox just copies the store layout that others use and doesn’t have the design creativity that his fellow scammer xcazanova has… 😂 😂
Let’s Find Out Who Spox Is 🧐⌗
While expected, the fake quitting kinda annoyed me, so it was time to go deeper…
Actually didn’t even really have to go deep as this idiot scammer just straight up put his suspected name in the earliest versions of his malicious tools - not even kidding.
Check out this basic BIN checker by SPOX CODER { DILA BELMILI }:
<?php
//API BIN URL BY SPOX CODER { DILA BELMILI }
$DILA_BIN = isset($_GET['bin']) ? trim(htmlentities($_GET['bin'])):'';
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, "https://lookup.binlist.net/".$DILA_BIN."");
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_POST, 1);
curl_setopt($ch, CURLOPT_ENCODING, 'gzip, deflate');
$headers = array();
$headers[] = "Accept-Encoding: gzip, deflate, br";
$headers[] = "Accept-Language: ar,en-US;q=0.9,en;q=0.8";
$headers[] = "User-Agent: Mozilla/5.0 (Windows NT 6.3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.106 Safari/537.36";
$headers[] = "Content-Type: application/json";
$headers[] = "Accept: application/json, text/javascript, */*; q=0.01";
$headers[] = "X-Requested-With: XMLHttpRequest";
$headers[] = "Connection: keep-alive";
curl_setopt($ch, CURLOPT_HTTPHEADER, $headers);
$final = curl_exec($ch);
echo $final;
exit();
?>
<html><head><title>Checker Bin By Spox.</title></head></html>
And then we can also see the name DILA BELMILI in v1 of his Wells Fargo phishing kit:
if ($success == "false") {
echo "<br><br><br><h3><center><h3 style='color:red'>YOUR API PROTECTION IS DEAD</h3> Please Contact Owner < Dila Belmili > On <a href='https://t.me/seller_62' target='_blanc'> TELEGRAM</></center></h3>";
}
I thought I had seen bad opsec before, but I ain’t never seen a fail this bad before! 🤣🤣🤣
Dila Belmili Doesn’t Even Try To Hide⌗
Once the suspected name, Dila Belmili, was found - the rest was trivial.
One of Dila Belmili’s Facebook page just straight up lists him as Spox under Other Names section:
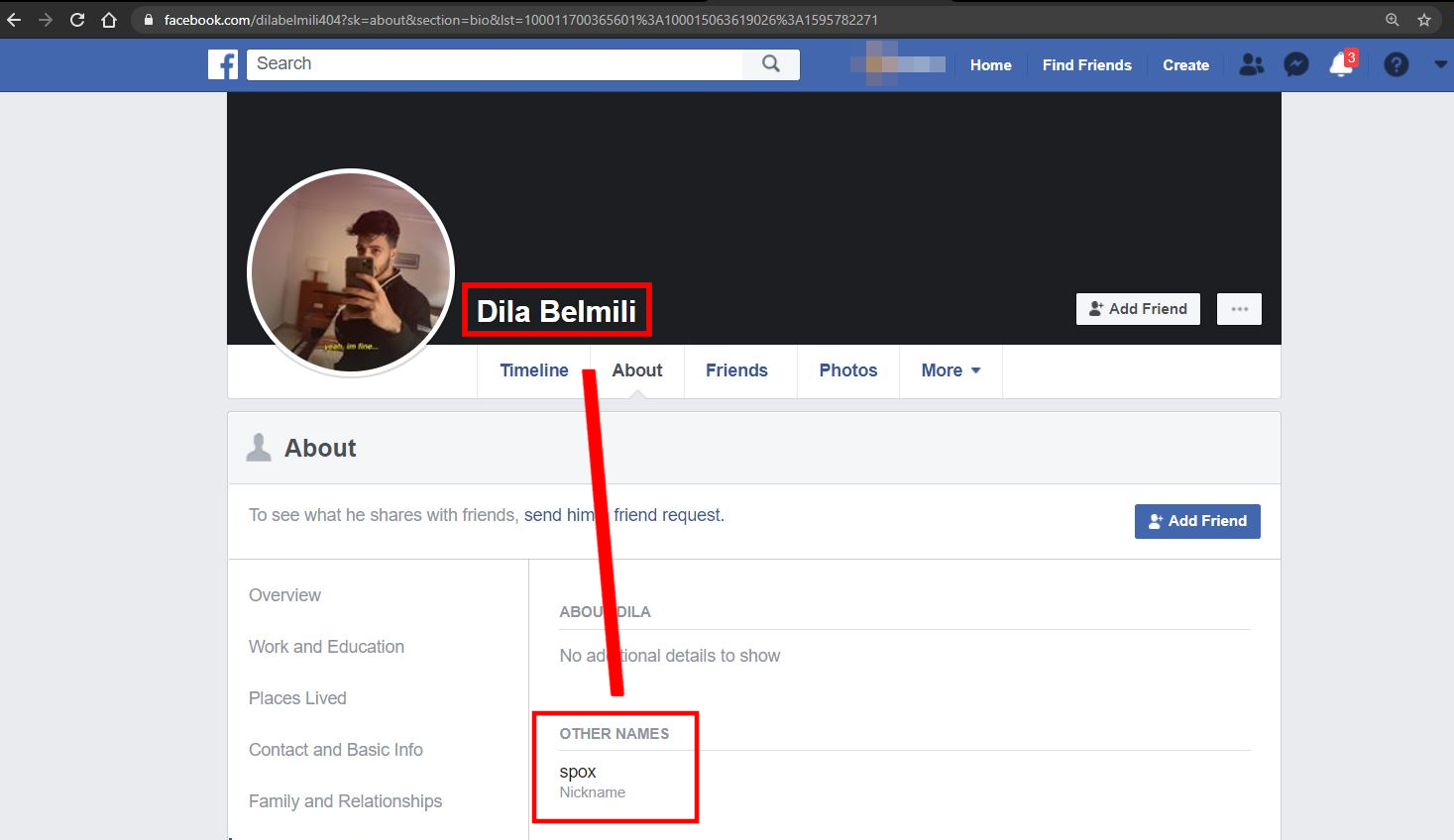
This was almost too easy that I was beginning to wonder if it might just be an elaborate decoy profile, but it’s pretty aged and it had other known phishing actors that haven’t been revealed (yet 😇).
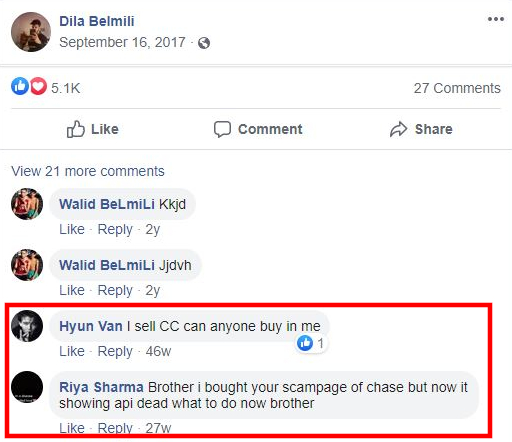
What pissed me off was seeing this scammer trying to sell off items that I highly suspect were carded with the payment data he has stolen from average people.
Here we can see Dila Belmili selling off a new Alienware laptop right on Facebook:
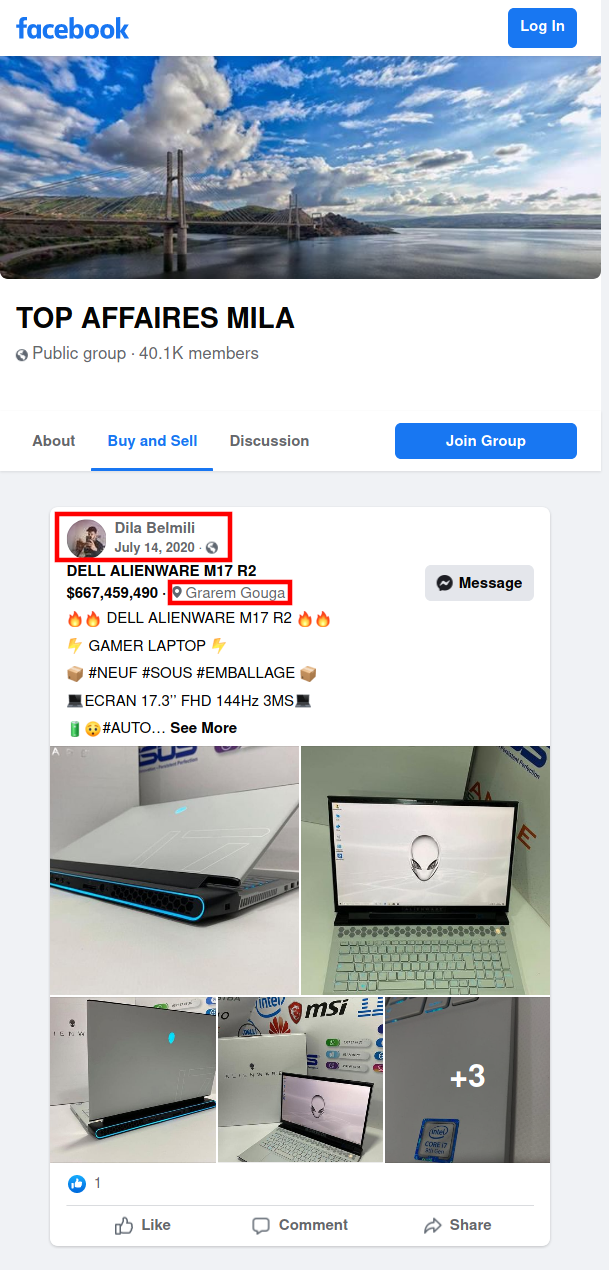
Damn he wants over $2,600 USD (348,000 DA) for this suspected carded item.
Wait, hold up…check out this image from his Instagram compared to the item he listed for sale - I think we found where Spox alien logo originates!
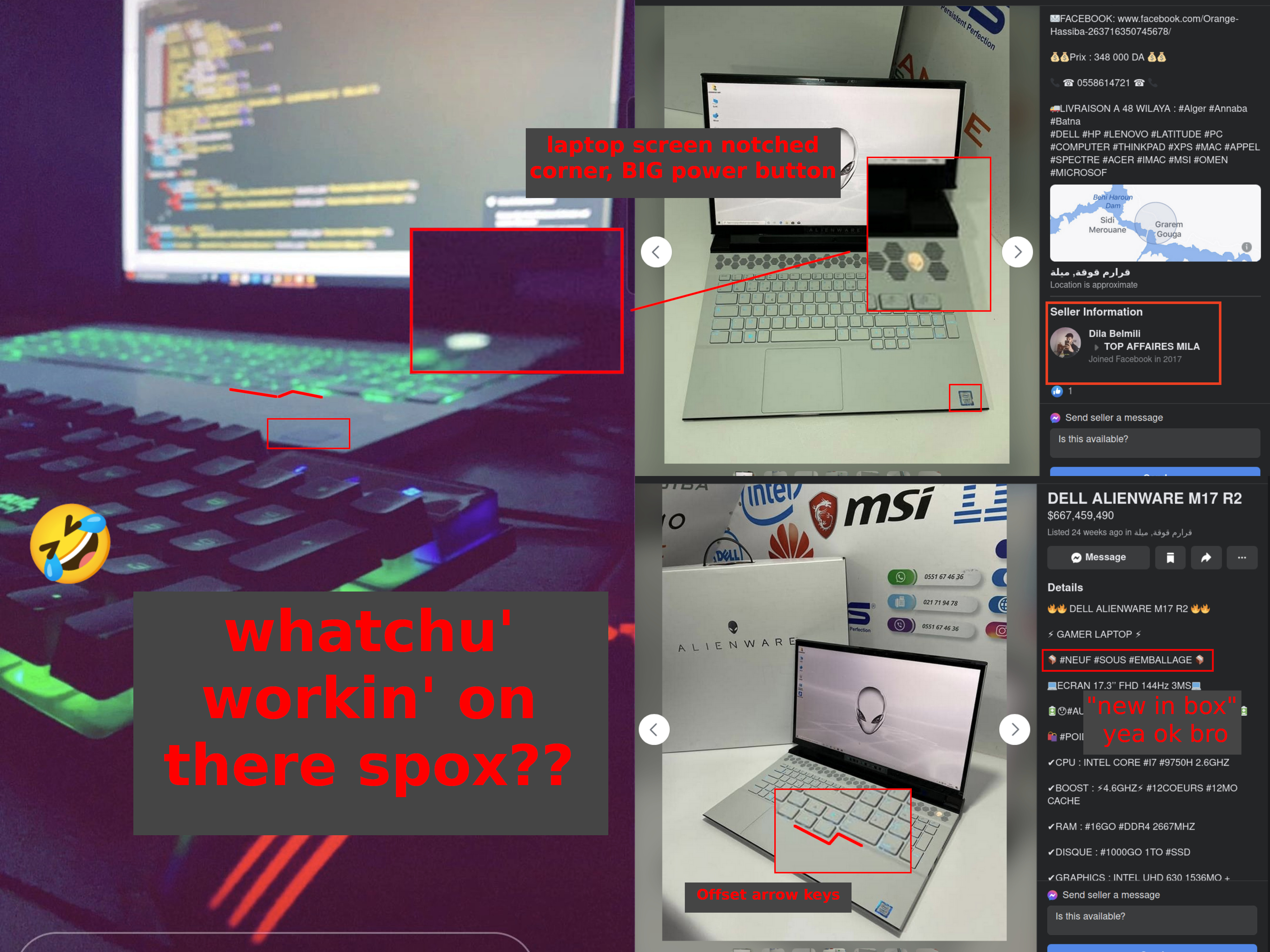
And this dude even left his location 🇩🇿 🇩🇿 on when he made that post - he just don’t give a fuck 🤣🤣🤣
Conclusion⌗
I’m fairly certain Spox’s last name is Belmili, but I am not able to definitively determine if his first name is indeed Dila, but I highly suspect it is.
If he doesn’t care to use any discernable form of opsec, then why would he try to hide his name? Sadly it seems that law enforcement in Algeria is either corrupt or totally incompetent - probably both.
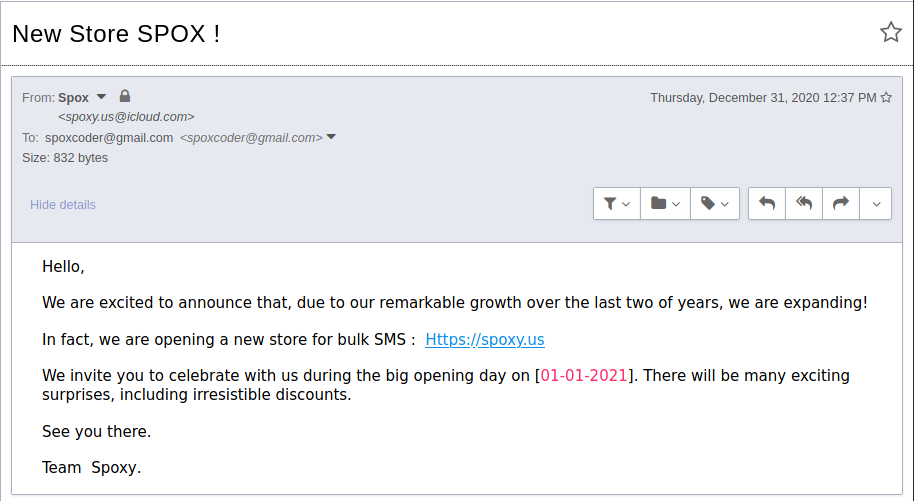
And lastly, I decided to create this post after receiving an email from Spox about expanding to a new fraud/scam online store he was having a “big opening day” on New Years Day 2021 due to “remarkable growth over the last two years”:
# whois spoxy.us
Domain Name: spoxy.us
Registry Domain ID: DDC2DA432F748452DAA59FE7B9FA9DE43-NSR
Registrar WHOIS Server: whois.godaddy.com
Registrar URL: whois.godaddy.com
Updated Date: 2020-12-09T01:51:02Z
Creation Date: 2020-11-21T03:43:12Z
Registry Expiry Date: 2021-11-21T03:43:12Z
Registrar: GoDaddy.com, LLC
Registrar IANA ID: 146
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +1.4806242505
