Trojan Malware, Recon, & BEC Attacks

Outline
Business email compromise (BEC) attacks are a big problem when it comes to organizational security and defending against them. One reason is that the attack often uses a human victim to authorize a fraudulent transaction, which can bypass existing security controls that would normally be used to prevent fraud. Another reason is that the lures used to social engineer the human victim can be expertly crafted by the attacker after they have been monitoring your activity for some time.

Earlier this year I was investigating an infected website when I found an interesting directory named ./webpanel/ that hosted a control panel interface being used in managing devices that were already infected with a trojan malware variant.
Command & Control (C2) Panels and C2 Servers⌗
Oftentimes when an attacker has infected multiple devices (e.g infected Windows computers), then they will use what is known as a C2 server to host a control panel interface that can remotely manage the infected devices from a centralized location. This provides convenience for the attacker since they only have to visit the C2 server’s URL to control the malware on the infected devices instead of being done individually for each infected device.
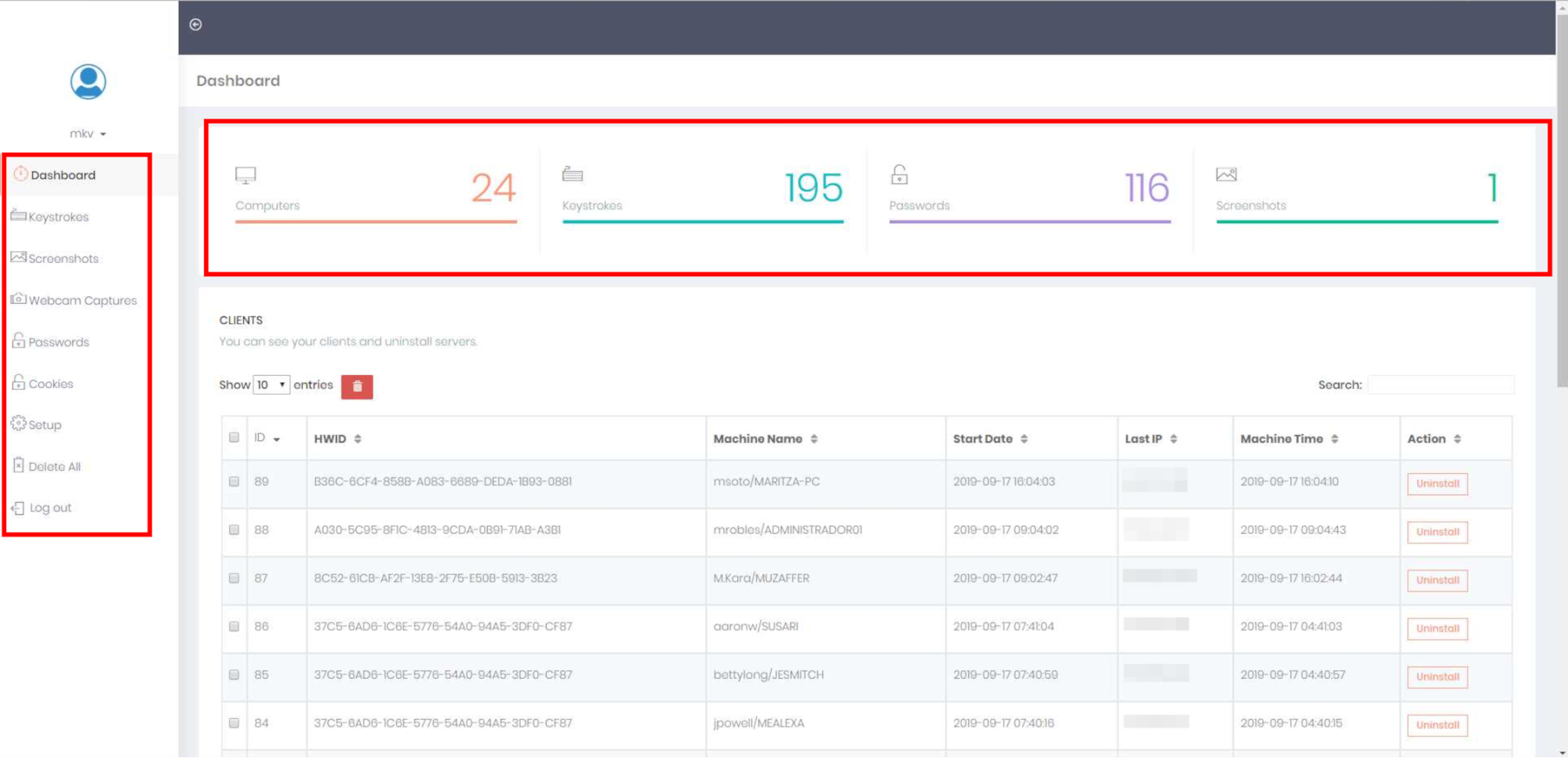
*C2 server panel collecting sensitive data from infected devices that are listed by hardware ID
Attackers will usually gain unauthorized access to an existing legitimate website, then upload their C2 control panel interface and “hide” it in a few levels of directories. This allows them to use an existing domain name and hosting server instead of having to fraudulently use someone else’s payment information to sign up for those services on their own.
Trojan Spyware: Origin Logger/Phoenix Keylogger⌗
The C2 panel interface matches the same panel that is used for the malware Origin Logger, which is bundled with the C2 panel and then sold to attackers. As the name suggests, its primary purpose is logging keystrokes, clipboard, HTTP cookies, taking periodic screenshots, and also viewing the webcam of infected computers. The creators even took the time to create marketing material for their Origin Logger malware:
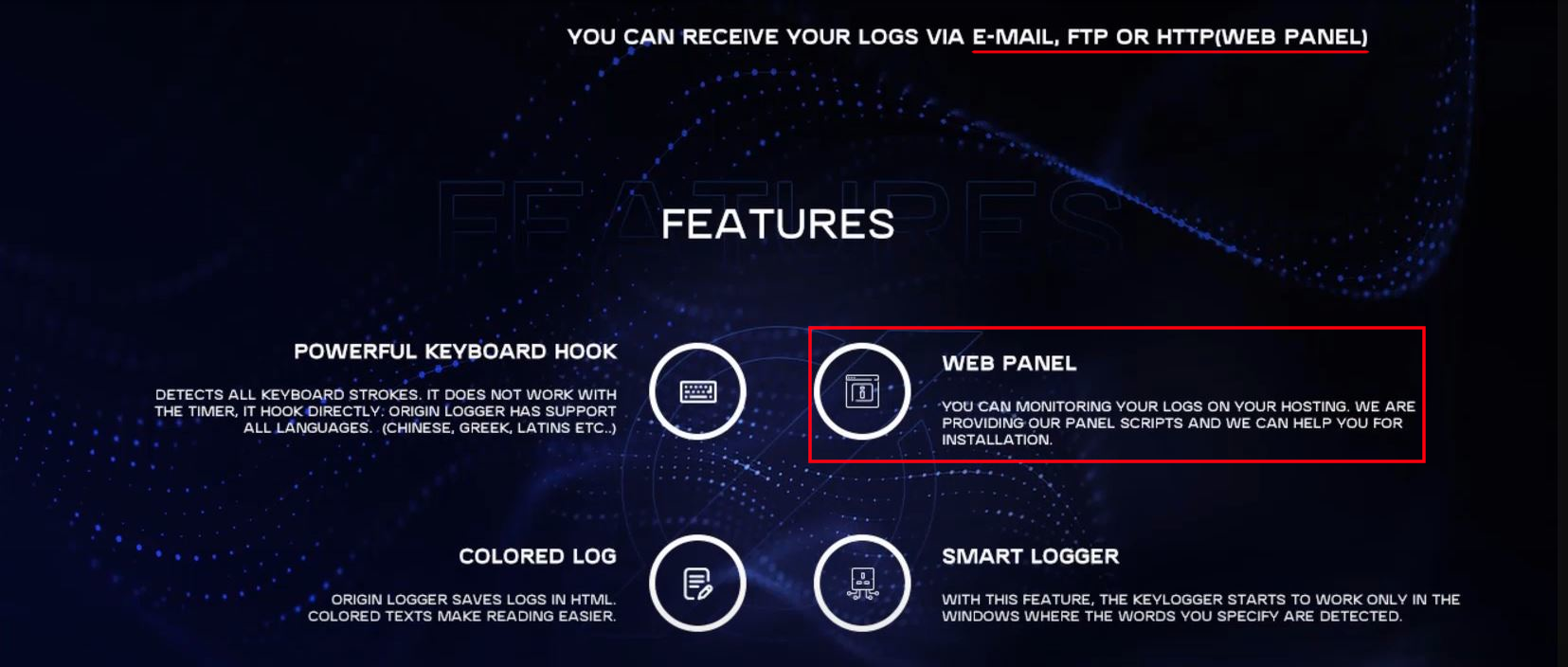
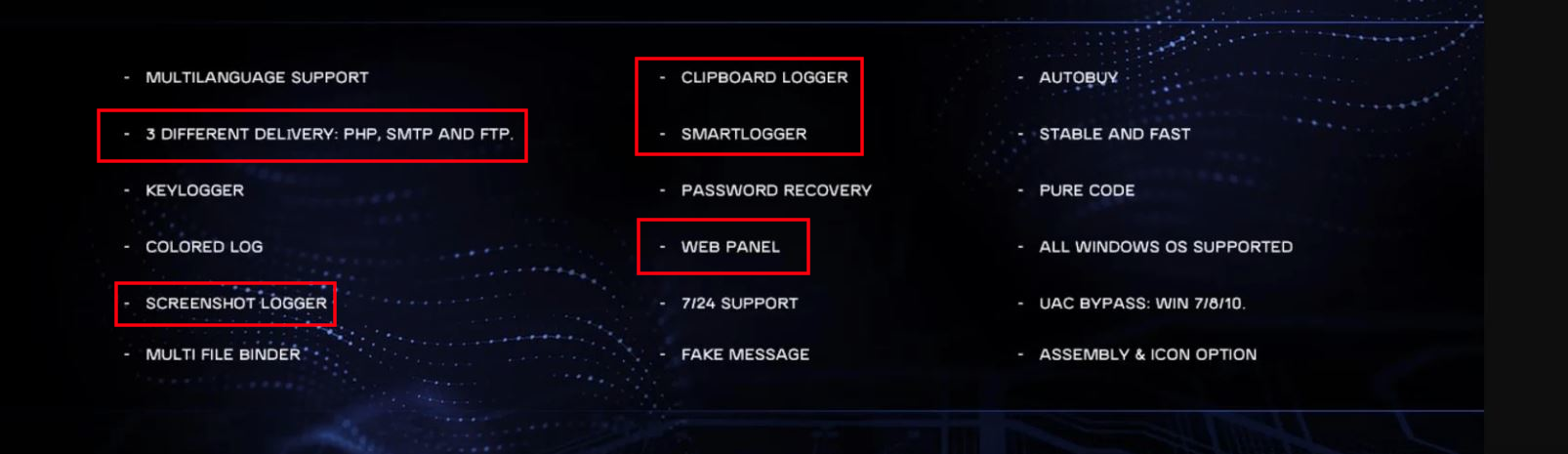
Shadowing⌗
When a device is infected with this malware, it becomes easy for an attacker to become familiar with an employee’s schedule and their communications. For certain industries that use expensive equipment or large orders, this knowledge can create opportunities for the attacker.
For example, one of the infected devices that the attackers were monitoring was assigned to an oil field services supervisor. The attacker probably already knows that expensive, large, and hard-to-transport equipment is used on active oil fields, but they need more specific information. The **Origin Logger **malware is what the attacker hopes will provide that information…and it did so by taking a screenshot as the supervisor was writing an email to management:
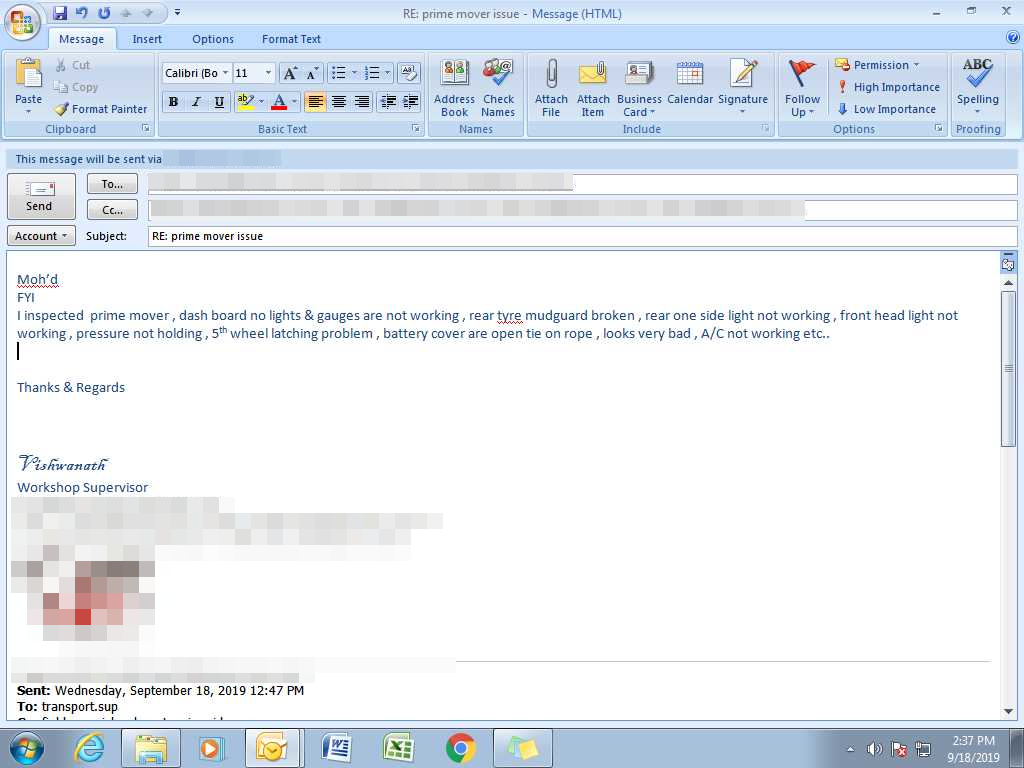
As shown in the above image, the email text is about a piece of equipment called a “prime mover”, which is a type of heavy utility truck, that needs to be replaced/repaired. The oil field services operation could be disrupted if they do not have the equipment to do their jobs, so this could be an opportunity for the attacker to craft a BEC email asking for payment for a “prime mover” truck. The attacker can say it was ordered quickly to avoid any service disruptions, or something similar to avoid suspicion when asking payment to be sent to the new bank account details that they will provide to the victim organization.

*Astra utility truck used by oil field service companies
Attempted BEC⌗
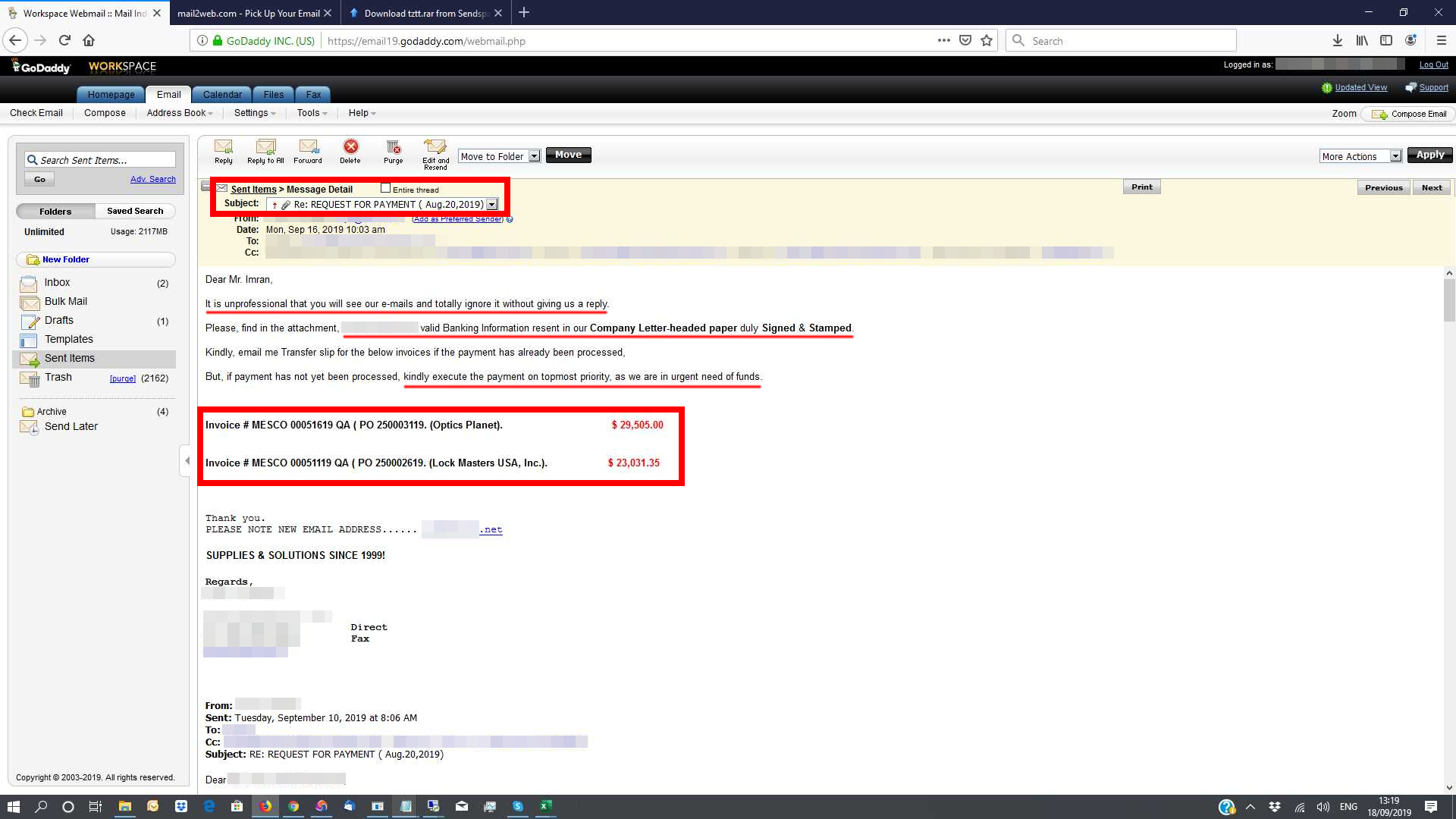
It seems that the attacker infected his own device, possibly for testing or troubleshooting purposes, but they never actually removed the malware so screenshots of their own device were being sent back to the C2 server! This is a big failure in their operational security as it gives us direct insight into some of the attacker’s tactics and operation.
The screenshot shows us a BEC email originally titled REQUEST FOR PAYMENT in the Sent folder and the email contents include a request for payment to the bank details provided in the attachment. The payment is for two invoices and together they total over $52,000 USD, so it is easy to see why attackers find it worthwhile to infect devices and monitor them for BEC opportunities.
How do we know it is the attacker? There is a screenshot of their Discord chat with a fellow attacker where they discuss losing access to the C2 panel due to someone, likely the website owner, deleting the files.
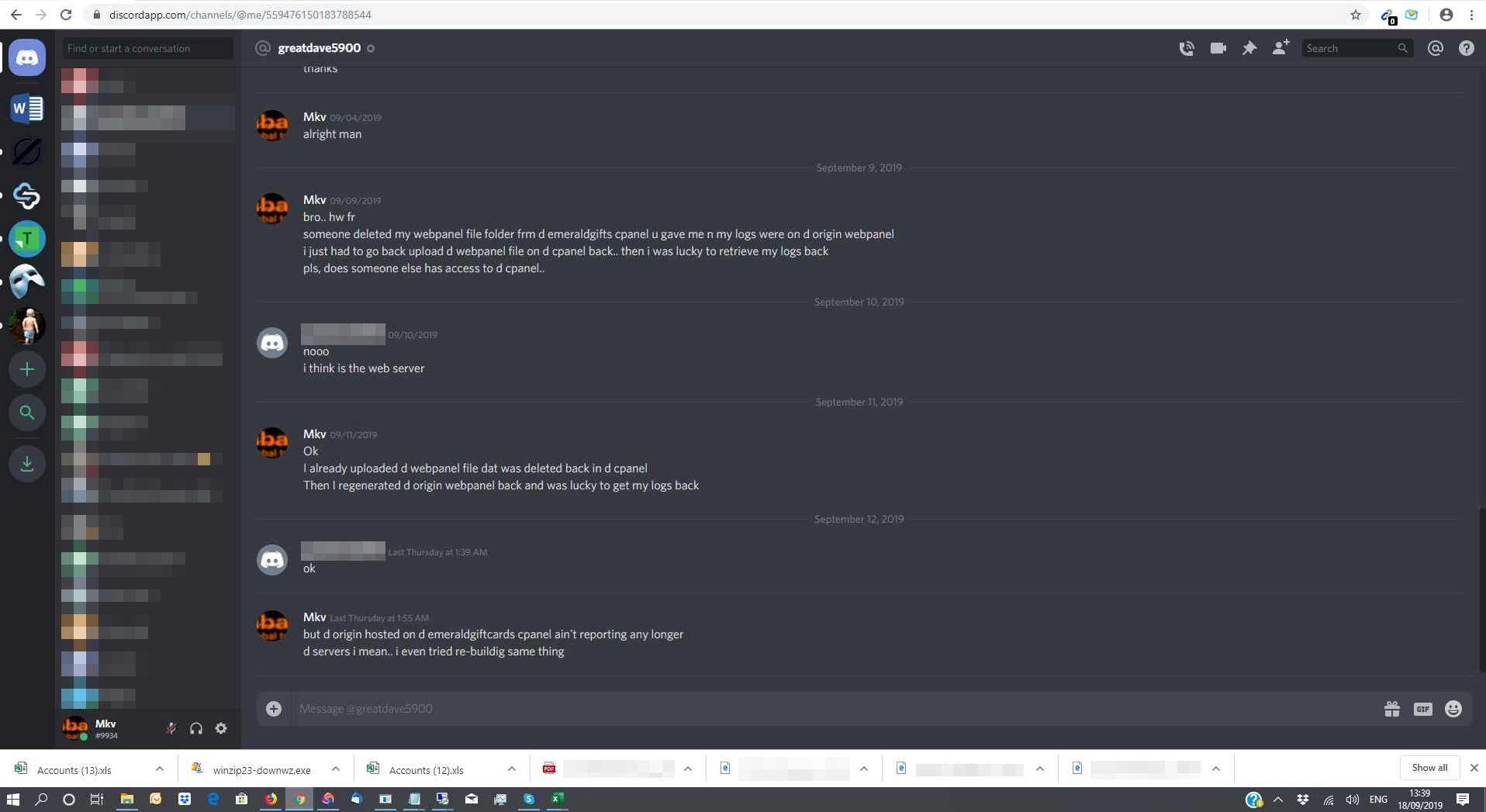
Unfortunately deleting the ./webpanel/ directory containing the C2 panel interface files did not fix the problem because the attacker knew the website’s cPanel password, so they just re-uploaded the C2 panel via the cPanel File Manager. This is why I always recommend resetting your hosting panel password along with any FTP/SSH users as removing the malware is not always enough to cut off unauthorized access to the website.